Exam Details
Exam Code
:JN0-334Exam Name
:Security, Specialist (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:90 Q&AsLast Updated
:
Juniper Juniper Certifications JN0-334 Questions & Answers
-
Question 11:
Which default protocol and port are used for JIMS to SRX client communication?
A. WMI over TCP; port 389
B. ADSI over TCP; port 389
C. HTTPS over TCP: port 443
D. RPC over TCP, port 135
-
Question 12:
Click the Exhibit button.

You have deployed Sky ATP to protect your network from attacks so that users are unable to download malicious files. However, after a user attempts to download a malicious file, they are still able to communicate through the SRX Series device.
Referring to the exhibit, which statement is correct?
A. Change the security policy from a standard security policy to a unified security policy.
B. Remove the fallback options in the advanced anti-malware policy.
C. Configure a security intelligence policy and apply it to the security policy.
D. Lower the verdict threshold in the advanced anti-malware policy.
-
Question 13:
Which two statements apply to policy scheduling? (Choose two.)
A. A policy refers to many schedules.
B. A policy refers to one schedule.
C. Multiple policies can refer to the same schedule.
D. A policy stays active regardless of when the schedule is active.
-
Question 14:
Click the Exhibit button.
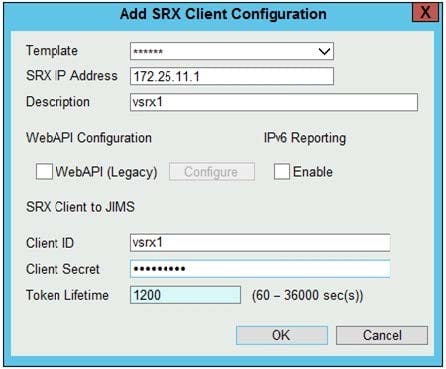
Referring to the exhibit, which two values in the JIMS SRX client configuration must match the values configured on the SRX client? (Choose two.)
A. IPv6 Reporting
B. Client ID
C. Client Secret
D. Token Lifetime
-
Question 15:
Which two statements describe SSL proxy on SRX Series devices? (Choose two.)
A. SSL proxy supports TLS version 1.2.
B. Client-protection is also known as reverse proxy.
C. SSL proxy is supported when enabled within logical systems.
D. SSL proxy relies on Active Directory to provide secure communication.
-
Question 16:
You are troubleshooting advanced policy-based routing (APBR). Which two actions should you perform in this scenario? (Choose two.)
A. Verify that the APBR profiles are applied to the egress zone.
B. Verity inet.0 for correct route leaking.
C. Review the APBR statistics for matching rules and route modifications.
D. Inspect the application system cache for the application entry.
-
Question 17:
When working with network events on a Juniper Secure Analytics device, flow records come from which source?
A. tap port
B. SPAN
C. switch
D. mirror
-
Question 18:
You are deploying a vSRX into a vSphere environment which applies the configuration from a bootable ISO file containing the juniper.conf file. After the vSRX boots and has the configuration applied, you make additional device specific configuration changes, commit, and reboot the device. Once the device finishes rebooting, you notice the specific changes you made are missing but the original configuration is applied.
In this scenario, what is the problem?
A. Configuration changes do not persist after reboots on vSRX.
B. The juniper.conf file was not applied to the vSRX.
C. The configuration file is corrupt.
D. The ISO file is still mounted on the vSRX.
-
Question 19:
Which three statements are true about the difference between cSRX-based virtual security deployments and vSRX-based virtual security deployments? (Choose three.)
A. vSRX provides Layer 2 to Layer 7 secure services and cSRX provides Layer 4 to Layer 7 secure services.
B. cSRX requires less storage and memory space for a given deployment than vSRX-based solutions.
C. cSRX-based solutions are more scalable than vSRX-based solutions.
D. vSRX and cSRX both provide Layer 2 to Layer 7 secure services.
E. vSRX provides faster deployment time and faster reboots compared to cSRX.
-
Question 20:
Which two statements describe superflows in Juniper Secure Analytics? (Choose two.)
A. JSA only supports Type A and Type C superflows.
B. Superflows can negatively impact licensing limitations.
C. Disk space usage is reduced on the JSA device.
D. Superflows combine many flows into a single flow.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-1103
Design, Associate (JNCIA-Design)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-334 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.