JN0-1331 Exam Details
-
Exam Code
:JN0-1331 -
Exam Name
:Security Design, Specialist (JNCDS-SEC) -
Certification
:Juniper Certifications -
Vendor
:Juniper -
Total Questions
:65 Q&As -
Last Updated
:Jan 13, 2026
Juniper JN0-1331 Online Questions & Answers
-
Question 1:
You are asked to provide a design proposal for a campus network. As part of the design, the customer requires that all end user devices must be authenticated before being granted access to their Layer 2 network. Which feature meets this requirement?
A. IPsec
B. 802.1X
C. NAT
D. ALGs -
Question 2:
Click the Exhibit button.
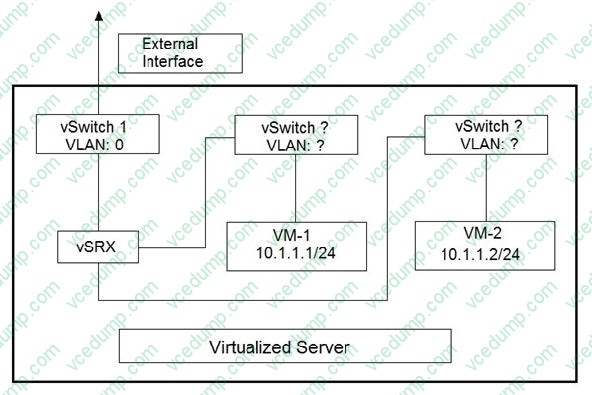
You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device. Which two actions must you perform to accomplish this task? (Choose two.)
A. Place both VMs in the same vSwitch
B. Place both VMs in the same VLAN
C. Place both VMs in different vSwitches
D. Place both VMs in different VLANs -
Question 3:
You are designing an enterprise WAN network that must connect multiple sites. You must provide a design proposal for the security elements needed to encrypt traffic between the remote sites. Which feature will secure the traffic?
A. BFD
B. OSPF
C. GRE
D. IPsec -
Question 4:
You are designing a corporate WAN using SRX Series devices as a combined firewall and router at each site. Regarding packet-mode and flow-mode operations in this scenario, which statement is true?
A. Packet-mode on SRX Series devices is required for deep packet inspection
B. Packet-mode is only supported on high-end SRX Series devices
C. An SRX Series device in flow-mode cannot forward packet-mode traffic
D. Flow-mode on SRX Series devices is required for security services -
Question 5:
You are creating a security design proposal for a customer who is connecting their headquarters to a remote branch site over an unsecured Internet connection. As part of your design, you must recommend a solution to connect these sites together and ensure that the communication is secured and encrypted.
In this scenario, which solution do you recommend?
A. GRE
B. XMPP
C. IPsec
D. MPLS -
Question 6:
You are designing a new network for your organization with the characteristics shown below.
All traffic must pass inspection by a security device.
A center-positioned segmentation gateway must provide deep inspection of each packet using 10 Gbps interfaces.
Policy enforcement must be centrally managed.
Which security model should you choose for your network design?
A. Intrazone Permit
B. trust but verify
C. user-role firewall policies
D. Zero Trust -
Question 7:
You are required to design a university network to meet the conditions shown below.
Users connected to the university network should be able to access the Internet and the research department lab network.
The research department lab network should not be able to reach the Internet.
Which three actions satisfy the design requirements? (Choose three.)
A. Use a global permit policy for Internet traffic
B. Use a global deny security policy for the research lab
C. Use separate security zones for each department
D. Use the default deny security policy for the research lab
E. Use a static NAT rule between the internal zones for the research lab -
Question 8:
You are designing a network management solution that provides automation for Junos devices. Your customer wants to know which solutions would require additional software to be deployed to existing Junos devices. Which two solutions satisfy this scenario? (Choose two.)
A. SaltStack
B. Ansible
C. Puppet
D. Chef -
Question 9:
Which solution provides a certificate based on user identity for network access?
A. network access control
B. user firewall
C. IP filtering
D. MAC filtering -
Question 10:
You are using SRX Series devices to secure your network and you require sandboxing for malicious file detonation. However, per company policy, you cannot send potentially malicious files outside your network for sandboxing. Which feature should you use in this situation?
A. Sky ATP
B. UTM antivirus
C. IPS
D. JATP
Related Exams:
-
JN0-102
Internet Associate, Junos(JNCIA-Junos) -
JN0-104
Junos, Associate (JNCIA-Junos) -
JN0-105
Junos, Associate (JNCIA-Junos) -
JN0-1101
Juniper Networks Certified Design Associate (JNCDA) -
JN0-1103
Design, Associate (JNCIA-Design) -
JN0-130
Juniper networks Certified internet specialist.e(jncis-e) -
JN0-1301
Data Center Design, Specialist (JNCDS-DC) -
JN0-1302
Data Center Design Specialist (JNCDS-DC) -
JN0-1331
Security Design, Specialist (JNCDS-SEC) -
JN0-1332
Security Design, Specialist (JNCDS-SEC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-1331 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.