Exam Details
Exam Code
:ECSAv8Exam Name
:EC-Council Certified Security Analyst (ECSA) v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:Aug 10, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAv8 Questions & Answers
-
Question 31:
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
A. SMTP Queue Bouncing
B. SMTP Message Bouncing
C. SMTP Server Bouncing
D. SMTP Mail Bouncing
-
Question 32:
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
A. Vulnerability Report
B. Executive Report
C. Client-side test Report
D. Host Report
-
Question 33:
Fuzz testing or fuzzing is a software/application testing technique used to discover coding errors and security loopholes in software, operating systems, or networks by inputting massive amounts of random data, called fuzz, to the system in an attempt to make it crash.
Fuzzers work best for problems that can cause a program to crash, such as buffer overflow, cross-site scripting, denial of service attacks, format bugs, and SQL injection.
Fuzzer helps to generate and submit a large number of inputs supplied to the application for testing it against the inputs. This will help us to identify the SQL inputs that generate malicious output.
Suppose a pen tester knows the underlying structure of the database used by the application (i.e., name, number of columns, etc.) that she is testing.
Which of the following fuzz testing she will perform where she can supply specific data to the application to discover vulnerabilities?
A. Clever Fuzz Testing
B. Dumb Fuzz Testing
C. Complete Fuzz Testing
D. Smart Fuzz Testing
-
Question 34:
Internet Control Message Protocol (ICMP) messages occur in many situations, such as whenever a datagram cannot reach the destination or the gateway does not have the buffering capacity to forward a datagram. Each ICMP message contains three fields: type, code, and checksum. Different types of Internet Control Message Protocols (ICMPs) are identified by a type and code field.
Which of the following ICMP messages will be generated if the destination port is not reachable?
A. ICMP Type 11 code 1
B. ICMP Type 5 code 3
C. ICMP Type 3 code 2
D. ICMP Type 3 code 3
-
Question 35:
To locate the firewall, SYN packet is crafted using Hping or any other packet crafter and sent to the firewall. If ICMP unreachable type 13 message (which is an admin prohibited packet) with a source IP address of the access control device is received, then it means which of the following type of firewall is in place?
A. Circuit level gateway
B. Stateful multilayer inspection firewall
C. Packet filter
D. Application level gateway
-
Question 36:
Which of the following is an ARP cache poisoning technique aimed at network switches?
A. Replay Attack
B. Mac Flooding
C. Man-in-the Middle Attack
D. DNS Poisoning
-
Question 37:
Which of the following documents helps in creating a confidential relationship between the pen tester and client to protect critical and confidential information or trade secrets?
A. Penetration Testing Agreement
B. Rules of Behavior Agreement
C. Liability Insurance
D. Non-Disclosure Agreement
-
Question 38:
TCP/IP model is a framework for the Internet Protocol suite of computer network protocols that defines the communication in an IP-based network. It provides end-to-end connectivity specifying how data should be formatted, addressed, transmitted, routed and received at the destination. This functionality has been organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved.

Which of the following TCP/IP layers selects the best path through the network for packets to travel?
A. Transport layer
B. Network Access layer
C. Internet layer
D. Application layer
-
Question 39:
Amazon, an IT based company, conducts a survey on the usage of the Internet. They found that company employees spend most of the time at work surfing the web for their personal use and for inappropriate web site viewing. Management decide to block all such web sites using URL filtering software.
How can employees continue to see the blocked websites?
A. Using session hijacking
B. Using proxy servers
C. Using authentication
D. Using encryption
-
Question 40:
A Blind SQL injection is a type of SQL Injection attack that asks the database true or false questions and determines the answer based on the application response. This attack is often used when the web application is configured to show generic error messages, but has not mitigated the code that is vulnerable to SQL injection.
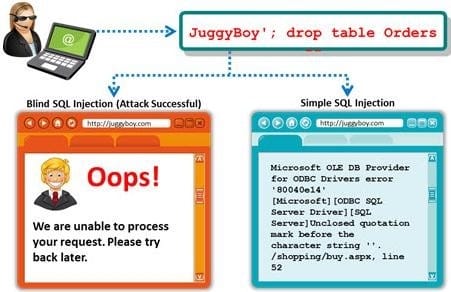
It is performed when an error message is not received from application while trying to exploit SQL vulnerabilities. The developer's specific message is displayed instead of an error message. So it is quite difficult to find SQL vulnerability in such cases.
A pen tester is trying to extract the database name by using a blind SQL injection. He tests the database using the below query and finally finds the database name.
http://juggyboy.com/page.aspx?id=1; IF (LEN(DB_NAME())=4) WAITFOR DELAY '00:00:10'-
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),1,1)))=97) WAITFOR DELAY '00:00:10'-
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),2,1)))=98) WAITFOR DELAY '00:00:10'-
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),3,1)))=99) WAITFOR DELAY '00:00:10'-
http://juggyboy.com/page.aspx?id=1; IF (ASCII(lower(substring((DB_NAME()),4,1)))=100) WAITFOR DELAY '00:00:10'-
What is the database name?
A. WXYZ
B. PQRS
C. EFGH
D. ABCD
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAv8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.