Exam Details
Exam Code
:ECSAv8Exam Name
:EC-Council Certified Security Analyst (ECSA) v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:Aug 10, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAv8 Questions & Answers
-
Question 21:
Which of the following is not a condition specified by Hamel and Prahalad (1990)?
A. Core competency should be aimed at protecting company interests
B. Core competency is hard for competitors to imitate
C. Core competency provides customer benefits
D. Core competency can be leveraged widely to many products and markets
-
Question 22:
What threat categories should you use to prioritize vulnerabilities detected in the pen testing report?
A. 1, 2, 3, 4, 5
B. Low, medium, high, serious, critical
C. Urgent, dispute, action, zero, low
D. A, b, c, d, e
-
Question 23:
Which of the following has an offset field that specifies the length of the header and data?
A. IP Header
B. UDP Header
C. ICMP Header
D. TCP Header
-
Question 24:
Many security and compliance projects begin with a simple idea: assess the organization's risk, vulnerabilities, and breaches. Implementing an IT security risk assessment is critical to the overall security posture of any organization.
An effective security risk assessment can prevent breaches and reduce the impact of realized breaches.
What is the formula to calculate risk?
A. Risk = Budget x Time
B. Risk = Goodwill x Reputation
C. Risk = Loss x Exposure factor
D. Risk = Threats x Attacks
-
Question 25:
John, the penetration tester in a pen test firm, was asked to find whether NTP services are opened on the target network (10.0.0.7) using Nmap tool.
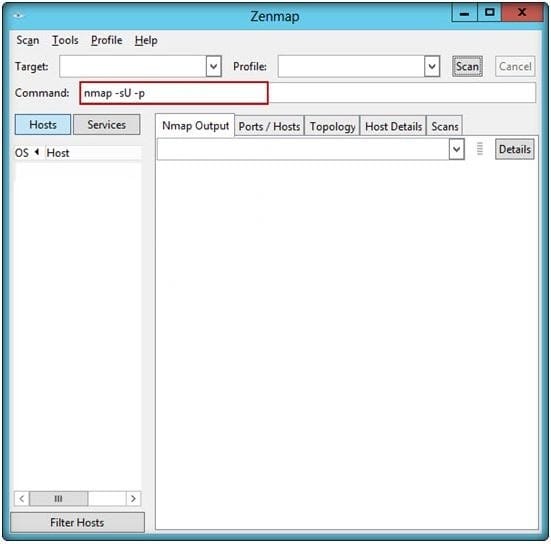
Which one of the following Nmap commands will he use to find it?
A. nmap -sU 璸 389 10.0.0.7
B. nmap -sU 璸 123 10.0.0.7
C. nmap -sU 璸 161 10.0.0.7
D. nmap -sU 璸 135 10.0.0.7
-
Question 26:
In the context of penetration testing, what does blue teaming mean?
A. A penetration test performed with the knowledge and consent of the organization's IT staff
B. It is the most expensive and most widely used
C. It may be conducted with or without warning
D. A penetration test performed without the knowledge of the organization's IT staff but with permission from upper management
-
Question 27:
Identify the port numbers used by POP3 and POP3S protocols.
A. 113 and 981
B. 111 and 982
C. 110 and 995
D. 109 and 973
-
Question 28:
The objective of social engineering pen testing is to test the strength of human factors in a security chain within the organization. It is often used to raise the level of security awareness among employees.

The tester should demonstrate extreme care and professionalism during a social engineering pen test as it might involve legal issues such as violation of privacy and may result in an embarrassing situation for the organization.
Which of the following methods of attempting social engineering is associated with bribing, handing out gifts, and becoming involved in a personal relationship to befriend someone inside the company?
A. Accomplice social engineering technique
B. Identity theft
C. Dumpster diving
D. Phishing social engineering technique
-
Question 29:
SQL injection attacks are becoming significantly more popular amongst hackers and there has been an estimated 69 percent increase of this attack type.
This exploit is used to great effect by the hacking community since it is the primary way to steal sensitive data from web applications. It takes advantage of non-validated input vulnerabilities to pass SQL commands through a web application for execution by a back- end database.
The below diagram shows how attackers launched SQL injection attacks on web applications.

Which of the following can the attacker use to launch an SQL injection attack?
A. Blah' "2=2 ?
B. Blah' and 2=2 -
C. Blah' and 1=1 -
D. Blah' or 1=1 -
-
Question 30:
Port numbers are used to keep track of different conversations crossing the network at the same time. Both TCP and UDP use port (socket) numbers to pass information to the upper layers. Port numbers have the assigned ranges.
Port numbers above 1024 are considered which one of the following?
A. Dynamically assigned port numbers
B. Statically assigned port numbers
C. Well-known port numbers
D. Unregistered port numbers
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAv8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.