Exam Details
Exam Code
:DCAExam Name
:Docker Certified Associate (DCA)Certification
:Docker CertificationsVendor
:DockerTotal Questions
:199 Q&AsLast Updated
:Jul 04, 2025
Docker Docker Certifications DCA Questions & Answers
-
Question 131:
The output of which command can be used to find the architecture and operating system an image is compatible with?
A. docker image inspect --filter {{.Architecture}} {{.OS}} '
B. docker image ls
C. docker image inspect --format {{.Architecture}} {{.OS}} '
D. docker image info
-
Question 132:
One of several containers in a pod is marked as unhealthy after failing its livenessProbe many times. Is this the action taken by the orchestrator to fix the unhealthy container? Solution: The controller managing the pod is autoscaled back to delete the unhealthy pod and alleviate load.
A. Yes
B. No
-
Question 133:
The Kubernetes yaml shown below describes a networkPolicy.
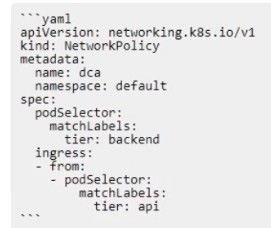
Will the networkPolicy BLOCK this traffic?
Solution: a request issued from a pod bearing the tier: backend label, to a pod bearing the tier: frontend label
A. Yes
B. No
-
Question 134:
Will this command list all nodes in a swarm cluster from the command line?
Solution: 'docker node Is'
A. Yes
B. No
-
Question 135:
You want to create a container that is reachable from its host's network. Does this action accomplish this?
Solution: Use either EXPOSE or --publish to access the containers on the bridge network
A. Yes
B. No
-
Question 136:
Following the principle of least privilege, which of the following methods can be used to securely grnt access to the specific user to communicate to a Docker engine? (Choose two.)
A. Utilize the '--host 0.0.0.0:2375' option to the Docker daemon to listen on port 2375 over TCP on all interfaces
B. Utilize openssl to create TLS client and server certificates, configuring the Docker engine to use with mutual TLS over TCP.
C. Utilize the '--host 127.0.0.1:2375' option to the Docker daemon to listen on port 2375 over TCP on localhost
D. Give the user root access to the server to allow them to run Docker commands as root.
-
Question 137:
Seven managers are in a swarm cluster.
Is this how should they be distributed across three datacenters or availability zones?
Solution: 3-3-1
A. Yes
B. No
-
Question 138:
Will this command display a list of volumes for a specific container?
Solution: docker volume logs nginx --containers'
A. Yes
B. No
-
Question 139:
Your organization has a centralized logging solution, such as Splunk.
Will this configure a Docker container to export container logs to the logging solution?
Solution: docker logs
A. Yes
B. No
-
Question 140:
Is this a supported user authentication method for Universal Control Plane? Solution: PAM
A. Yes
B. No
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Docker exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your DCA exam preparations and Docker certification application, do not hesitate to visit our Vcedump.com to find your solutions here.