Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Aug 23, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 831:
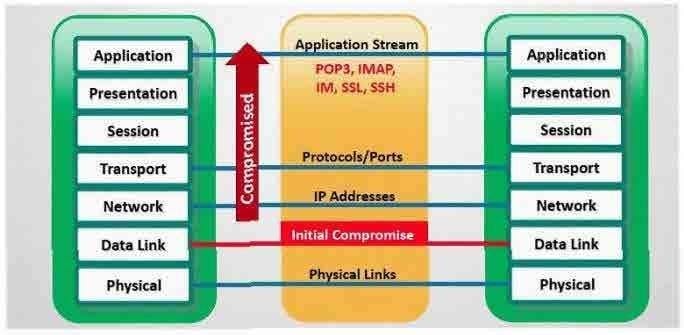
In which part of OSI layer, ARP Poisoning occurs?
A. Transport Layer
B. Datalink Layer
C. Physical Layer
D. Application layer
-
Question 832:
TCP/IP Session Hijacking is carried out in which OSI layer?
A. Datalink layer
B. Transport layer
C. Network layer
D. Physical layer
-
Question 833:
SNMP is a connectionless protocol that uses UDP instead of TCP packets (True or False)
A. true
B. false
-
Question 834:
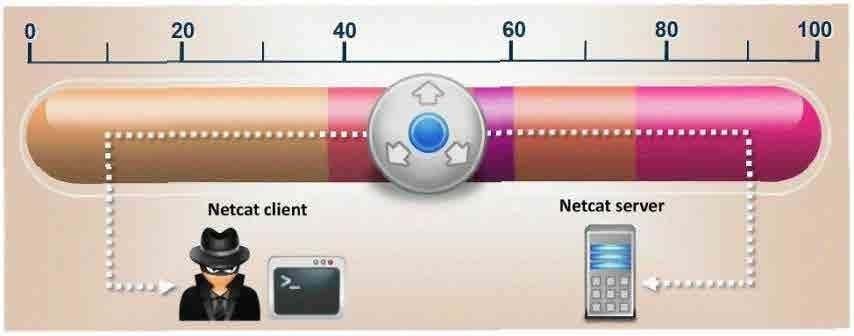
What is the correct command to run Netcat on a server using port 56 that spawns command shell when connected?
A. nc -port 56 -s cmd.exe
B. nc -p 56 -p -e shell.exe
C. nc -r 56 -c cmd.exe
D. nc -L 56 -t -e cmd.exe
-
Question 835:
Which of the following statements would NOT be a proper definition for a Trojan Horse?
A. An authorized program that has been designed to capture keyboard keystroke while the user is unaware of such activity being performed
B. An unauthorized program contained within a legitimate program. This unauthorized program performs functions unknown (and probably unwanted) by the user
C. A legitimate program that has been altered by the placement of unauthorized code within it; this code performs functions unknown (and probably unwanted) by the user
D. Any program that appears to perform a desirable and necessary function but that (because of unauthorized code within it that is unknown to the user) performs functions unknown (and definitely unwanted) by the user
-
Question 836:
This attack uses social engineering techniques to trick users into accessing a fake Web site and divulging personal information. Attackers send a legitimate- looking e-mail asking users to update their information on the company's Web site, but the URLs in the e-mail actually point to a false Web site.
A. Wiresharp attack
B. Switch and bait attack
C. Phishing attack
D. Man-in-the-Middle attack
-
Question 837:
Syslog is a standard for logging program messages. It allows separation of the software that generates messages from the system that stores them and the software that reports and analyzes them. It also provides devices, which would otherwise be unable to communicate a means to notify administrators of problems or performance.
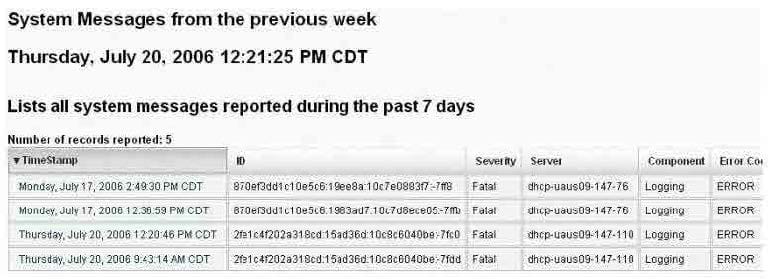
What default port Syslog daemon listens on?
A. 242
B. 312
C. 416
D. 514
-
Question 838:
How many bits encryption does SHA-1 use?
A. 64 bits
B. 128 bits
C. 256 bits
D. 160 bits
-
Question 839:
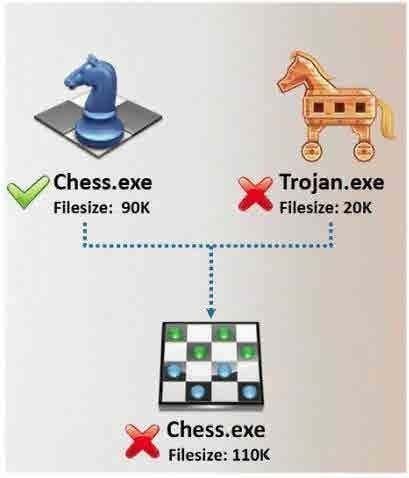
In Trojan terminology, what is required to create the executable file chess.exe as shown below?
A. Mixer
B. Converter
C. Wrapper
D. Zipper
-
Question 840:
Google uses a unique cookie for each browser used by an individual user on a computer. This cookie contains information that allows Google to identify records about that user on its database. This cookie is submitted every time a user launches a Google search, visits a site using AdSense etc. The information stored in Google's database, identified by the cookie, includes
Everything you search for using Google Every web page you visit that has Google Adsense ads
How would you prevent Google from storing your search keywords?
A. Block Google Cookie by applying Privacy and Security settings in your web browser
B. Disable the Google cookie using Google Advanced Search settings on Google Search page
C. Do not use Google but use another search engine Bing which will not collect and store your search keywords
D. Use MAC OS X instead of Windows 7. Mac OS has higher level of privacy controls by default.
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.