Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Jun 29, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 611:
What is the broadcast address for the subnet 190.86.168.0/22?
A. 190.86.168.255
B. 190.86.255.255
C. 190.86.171.255
D. 190.86.169.255
-
Question 612:
Which of the following are valid types of rootkits? (Choose three.)
A. Hypervisor level
B. Network level
C. Kernel level
D. Application level
E. Physical level
F. Data access level
-
Question 613:
Which vital role does the U.S. Computer Security Incident Response Team (CSIRT) provide?
A. Incident response services to any user, company, government agency, or organization in partnership with the Department of Homeland Security
B. Maintenance of the nation's Internet infrastructure, builds out new Internet infrastructure, and decommissions old Internet infrastructure
C. Registration of critical penetration testing for the Department of Homeland Security and public and private sectors
D. Measurement of key vulnerability assessments on behalf of the Department of Defense (DOD) and State Department, as well as private sectors
-
Question 614:
Which of the following is a common Service Oriented Architecture (SOA) vulnerability?
A. Cross-site scripting
B. SQL injection
C. VPath injection
D. XML denial of service issues
-
Question 615:
A company has five different subnets: 192.168.1.0, 192.168.2.0, 192.168.3.0, 192.168.4.0 and 192.168.5.0. How can NMAP be used to scan these adjacent Class C networks?
A. NMAP -P 192.168.1-5.
B. NMAP -P 192.168.0.0/16
C. NMAP -P 192.168.1.0, 2.0, 3.0, 4.0, 5.0
D. NMAP -P 192.168.1/17
-
Question 616:
What command would you type to OS fingerprint a server using the command line?
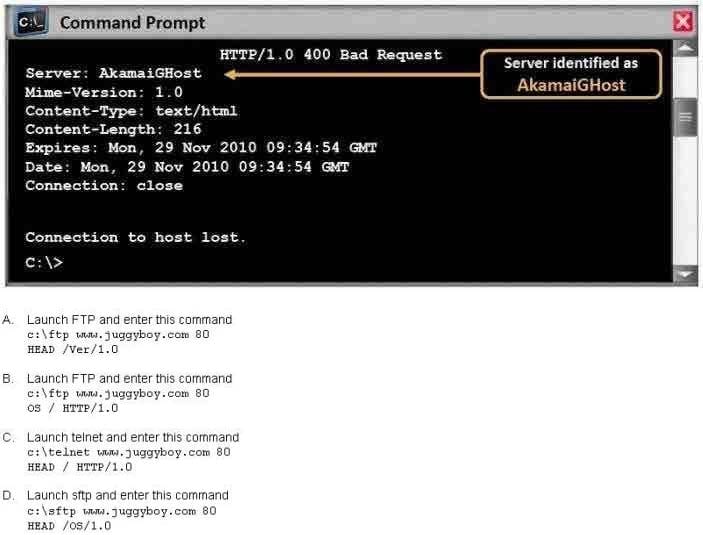
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 617:
What do you call a pre-computed hash?
A. Sun tables
B. Apple tables
C. Rainbow tables
D. Moon tables
-
Question 618:
Why attackers use proxy servers?
A. To ensure the exploits used in the attacks always flip reverse vectors
B. Faster bandwidth performance and increase in attack speed
C. Interrupt the remote victim's network traffic and reroute the packets to attackers machine
D. To hide the source IP address so that an attacker can hack without any legal corollary
-
Question 619:
The SNMP Read-Only Community String is like a password. The string is sent along with each SNMP Get-Request and allows (or denies) access to a device. Most network vendors ship their equipment with a default password of "public". This is the so-called "default public community string". How would you keep intruders from getting sensitive information regarding the network devices using SNMP? (Select 2 answers)
A. Enable SNMPv3 which encrypts username/password authentication
B. Use your company name as the public community string replacing the default 'public'
C. Enable IP filtering to limit access to SNMP device
D. The default configuration provided by device vendors is highly secure and you don't need to change anything
-
Question 620:
You are writing security policy that hardens and prevents Footprinting attempt by Hackers. Which of the following countermeasures will NOT be effective against this attack?
A. Configure routers to restrict the responses to Footprinting requests
B. Configure Web Servers to avoid information leakage and disable unwanted protocols
C. Lock the ports with suitable Firewall configuration
D. Use an IDS that can be configured to refuse suspicious traffic and pick up Footprinting patterns
E. Evaluate the information before publishing it on the Website/Intranet
F. Monitor every employee computer with Spy cameras, keyloggers and spy on them
G. Perform Footprinting techniques and remove any sensitive information found on DMZ sites
H. Prevent search engines from caching a Webpage and use anonymous registration services
I. Disable directory and use split-DNS
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.