Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Aug 23, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 31:
During the intelligence gathering phase of a penetration test, you come across a press release by a security products vendor stating that they have signed a multi- million dollar agreement with the company you are targeting. The contract was for vulnerability assessment tools and network based IDS systems. While researching on that particular brand of IDS you notice that its default installation allows it to perform sniffing and attack analysis on one NIC and caters to its management and reporting on another NIC. The sniffing interface is completely unbound from the TCP/IP stack by default. Assuming the defaults were used, how can you detect these sniffing interfaces?
A. Use a ping flood against the IP of the sniffing NIC and look for latency in the responses.
B. Send your attack traffic and look for it to be dropped by the IDS.
C. Set your IP to that of the IDS and look for it as it attempts to knock your computer off the network.
D. The sniffing interface cannot be detected.
-
Question 32:
Which of the following are potential attacks on cryptography? (Select 3)
A. One-Time-Pad Attack
B. Chosen-Ciphertext Attack
C. Man-in-the-Middle Attack
D. Known-Ciphertext Attack
E. Replay Attack
-
Question 33:
ETHER: Destination address : 0000BA5EBA11 ETHER: Source address :
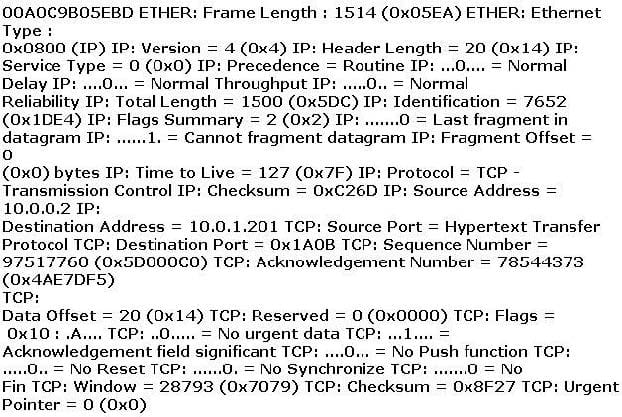
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application. Which of the following strategies can be used to defeat detection by a network-based IDS application?
A. Create a SYN flood
B. Create a network tunnel
C. Create multiple false positives
D. Create a ping flood
-
Question 34:
You perform the above traceroute and notice that hops 19 and 20 both show the same IP address.

This probably indicates what?
A. A host based IDS
B. A Honeypot
C. A stateful inspection firewall
D. An application proxying firewall
-
Question 35:
Which of the following is not an effective countermeasure against replay attacks?
A. Digital signatures
B. Time Stamps
C. System identification
D. Sequence numbers
-
Question 36:
To scan a host downstream from a security gateway, Firewalking:
A. Sends a UDP-based packet that it knows will be blocked by the firewall to determine how specifically the firewall responds to such packets
B. Uses the TTL function to send packets with a TTL value set to expire one hop past the identified security gateway
C. Sends an ICMP ''administratively prohibited'' packet to determine if the gateway will drop the packet without comment.
D. Assesses the security rules that relate to the target system before it sends packets to any hops on the route to the gateway
-
Question 37:
You may be able to identify the IP addresses and machine names for the firewall, and the names of internal mail servers by:
A. Sending a mail message to a valid address on the target network, and examining the header information generated by the IMAP servers
B. Examining the SMTP header information generated by using the x command parameter of DIG
C. Examining the SMTP header information generated in response to an e-mail message sent to an invalid address
D. Sending a mail message to an invalid address on the target network, and examining the header information generated by the POP servers
-
Question 38:
If you come across a sheepdip machaine at your client site, what would you infer?
A. A sheepdip computer is used only for virus checking.
B. A sheepdip computer is another name for honeypop.
C. A sheepdip coordinates several honeypots.
D. A sheepdip computer defers a denial of service attack.
-
Question 39:
What type of attack changes its signature and/or payload to avoid detection by antivirus programs?
A. Polymorphic
B. Rootkit
C. Boot sector
D. File infecting
-
Question 40:
What is a sheepdip?
A. It is another name for Honeynet
B. It is a machine used to coordinate honeynets
C. It is the process of checking physical media for virus before they are used in a computer
D. None of the above
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.