Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Jun 20, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 301:
You are manually conducting Idle Scanning using Hping2. During your scanning you notice that almost every query increments the IPID regardless of the port being queried. One or two of the queries cause the IPID to increment by more than one value. Why do you think this occurs?
A. The zombie you are using is not truly idle.
B. A stateful inspection firewall is resetting your queries.
C. Hping2 cannot be used for idle scanning.
D. These ports are actually open on the target system.
-
Question 302:
While reviewing the result of scanning run against a target network you come across the following:
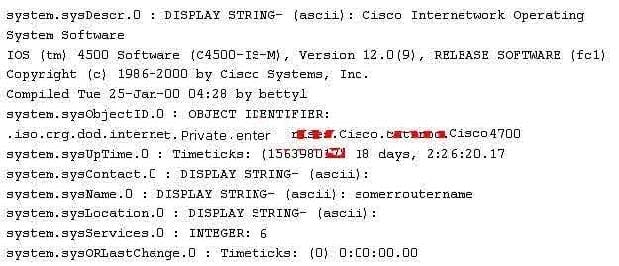
Which among the following can be used to get this output?
A. A Bo2k system query.
B. nmap protocol scan
C. A sniffer
D. An SNMP walk
-
Question 303:
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
A. SYN scan
B. ACK scan
C. RST scan
D. Connect scan
E. FIN scan
-
Question 304:
Name two software tools used for OS guessing? (Choose two.
A. Nmap
B. Snadboy
C. Queso
D. UserInfo
E. NetBus
-
Question 305:
Sandra is the security administrator of XYZ.com. One day she notices that the XYZ.com Oracle database server has been compromised and customer information along with financial data has been stolen. The financial loss will be estimated in millions of dollars if the database gets into the hands of competitors. Sandra wants to report this crime to the law enforcement agencies immediately.
Which organization coordinates computer crime investigations throughout the United States?
A. NDCA
B. NICP
C. CIRP
D. NPC
E. CIA
-
Question 306:
Which of the following Nmap commands would be used to perform a stack fingerprinting?
A. Nmap -O -p80
B. Nmap -hU -Q
C. Nmap -sT -p
D. Nmap -u -o -w2
E. Nmap -sS -0p target
-
Question 307:
Exhibit
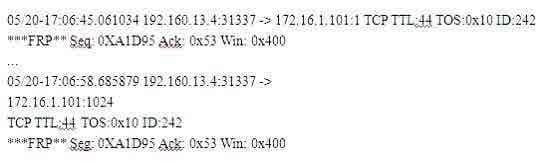
(Note: the student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.)
Snort has been used to capture packets on the network. On studying the packets, the penetration tester finds it to be abnormal. If you were the penetration tester, why would you find this abnormal?
What is odd about this attack? Choose the best answer.
A. This is not a spoofed packet as the IP stack has increasing numbers for the three flags.
B. This is back orifice activity as the scan comes form port 31337.
C. The attacker wants to avoid creating a sub-carries connection that is not normally valid.
D. These packets were crafted by a tool, they were not created by a standard IP stack.
-
Question 308:
What does a type 3 code 13 represent?(Choose two.
A. Echo request
B. Destination unreachable
C. Network unreachable
D. Administratively prohibited
E. Port unreachable
F. Time exceeded
-
Question 309:
Destination unreachable administratively prohibited messages can inform the hacker to what?
A. That a circuit level proxy has been installed and is filtering traffic
B. That his/her scans are being blocked by a honeypot or jail
C. That the packets are being malformed by the scanning software
D. That a router or other packet-filtering device is blocking traffic
E. That the network is functioning normally
-
Question 310:
John is using a special tool on his Linux platform that has a signature database and is therefore able to detect hundred of vulnerabilities in UNIX, Windows, and commonly-used web CGI scripts. Additionally, the database detects DDoS zombies and Trojans. What would be the name of this multifunctional tool?
A. nmap
B. hping
C. nessus
D. make
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.