Exam Details
Exam Code
:CEH-001Exam Name
:Certified Ethical Hacker (CEH)Certification
:GAQM CertificationsVendor
:GAQMTotal Questions
:878 Q&AsLast Updated
:Jun 20, 2025
GAQM GAQM Certifications CEH-001 Questions & Answers
-
Question 181:
What happens during a SYN flood attack?
A. TCP connection requests floods a target machine is flooded with randomized source address and ports for the TCP ports.
B. A TCP SYN packet, which is a connection initiation, is sent to a target machine, giving the target host's address as both source and destination, and is using the same port on the target host as both source and destination.
C. A TCP packet is received with the FIN bit set but with no ACK bit set in the flags field.
D. A TCP packet is received with both the SYN and the FIN bits set in the flags field.
-
Question 182:
Which one of the following network attacks takes advantages of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
A. Teardrop
B. Smurf
C. Ping of Death
D. SYN flood
E. SNMP Attack
-
Question 183:
A denial of Service (DoS) attack works on the following principle:
A. MS-DOS and PC-DOS operating system utilize a weaknesses that can be compromised and permit them to launch an attack easily.
B. All CLIENT systems have TCP/IP stack implementation weakness that can be compromised and permit them to lunch an attack easily.
C. Overloaded buffer systems can easily address error conditions and respond appropriately.
D. Host systems cannot respond to real traffic, if they have an overwhelming number of incomplete connections (SYN/RCVD State).
E. A server stops accepting connections from certain networks one those network become flooded.
-
Question 184:
Global deployment of RFC 2827 would help mitigate what classification of attack?
A. Sniffing attack
B. Denial of service attack
C. Spoofing attack
D. Reconnaissance attack
E. Prot Scan attack
-
Question 185:
What happens when one experiences a ping of death?
A. This is when an IP datagram is received with the "protocol" field in the IP header set to 1 (ICMP) and the "type" field in the ICMP header is set to 18 (Address Mask Reply).
B. This is when an IP datagram is received with the "protocol" field in the IP header set to 1 (ICMP), the Last Fragment bit is set, and (IP offset ` 8) + (IP data length) >65535. In other words, the IP offset (which represents the starting position of this fragment in the original packet, and which is in 8-byte units) plus the rest of the packet is greater than the maximum size for an IP packet.
C. This is when an IP datagram is received with the "protocol" field in the IP header set to 1 (ICMP) and the source equal to destination address.
D. This is when an the IP header is set to 1 (ICMP) and the "type" field in the ICMP header is set to 5 (Redirect).
-
Question 186:
Which one of the following instigates a SYN flood attack?
A. Generating excessive broadcast packets.
B. Creating a high number of half-open connections.
C. Inserting repetitive Internet Relay Chat (IRC) messages.
D. A large number of Internet Control Message Protocol (ICMP) traces.
-
Question 187:
Exhibit: You have captured some packets in Ethereal. You want to view only packets sent from 10.0.0.22. What filter will you apply?
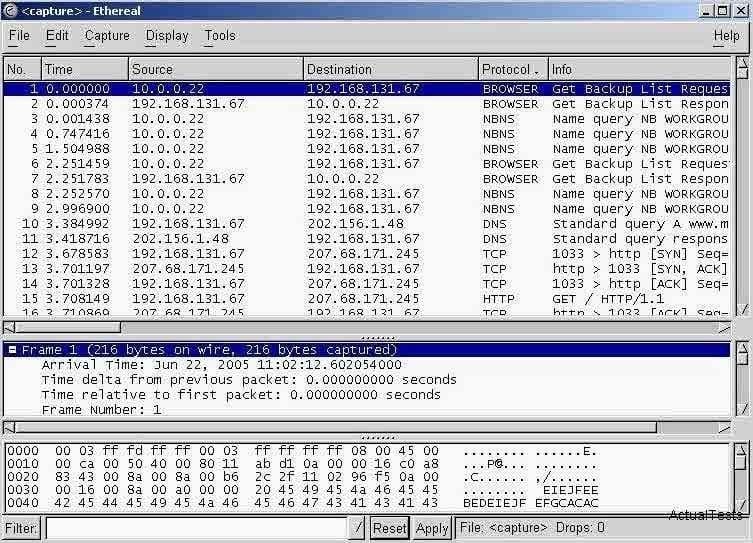
A. ip = 10.0.0.22
B. ip.src == 10.0.0.22
C. ip.equals 10.0.0.22
D. ip.address = 10.0.0.22
-
Question 188:
Tess King, the evil hacker, is purposely sending fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65, 536 bytes. From the information given, what type of attack is Tess King attempting to perform?
A. Syn flood
B. Smurf
C. Ping of death
D. Fraggle
-
Question 189:
Bob wants to prevent attackers from sniffing his passwords on the wired network. Which of the following lists the best options?
A. RSA, LSA, POP
B. SSID, WEP, Kerberos
C. SMB, SMTP, Smart card
D. Kerberos, Smart card, Stanford SRP
-
Question 190:
Which tool/utility can help you extract the application layer data from each TCP connection from a log file into separate files?
A. Snort
B. argus
C. TCPflow
D. Tcpdump
Related Exams:
APM-001
Certified Associate in Project Management (APM)BMP-001
Certified Business Management Professional (BMP)BPM-001
Certified Business Process Manager (BPM)CAMT-001
IMTQN Certified Advanced Mobile Tester (CAMT)CBAF-001
Certified Business Analyst - FoundationCBCP-002
Certified Business Continuity Professional (CBCP)CCCP-001
Certified Cloud Computing Professional (CCCP)CDCP-001
Certified Data Centre Professional (CDCP)CEH-001
Certified Ethical Hacker (CEH)CFA-001
Certified Forensic Analyst (CFA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GAQM exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CEH-001 exam preparations and GAQM certification application, do not hesitate to visit our Vcedump.com to find your solutions here.