Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:742 Q&AsLast Updated
:May 22, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 251:
Company A acquired Company B. During an initial assessment, the companies discover they are using the same SSO system. To help users with the transition. Company A is requiring the following:
1.
Before the merger is complete, users from both companies should use a single set of usernames and passwords.
2.
Users in the same departments should have the same set of rights and privileges, but they should have different sets of rights and privileges if they have different IPs.
3.
Users from Company B should be able to access Company A's available resources.
Which of the following are the BEST solutions? (Choose two.)
A. Installing new Group Policy Object policies
B. Establishing one-way trust from Company B to Company A
C. Enabling SAML
D. Implementing attribute-based access control
E. Installing Company A's Kerberos systems in Company B's network
F. Updating login scripts
-
Question 252:
A firewall administrator needs to ensure all traffic across the company network is inspected. The administrator gathers data and finds the following information regarding the typical traffic in the network:
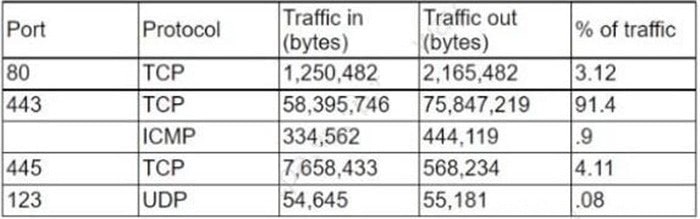
Which of the following is the BEST solution to ensure the administrator can complete the assigned task?
A. A full-tunnel VPN
B. Web content filtering
C. An endpoint DLP solution
D. SSL/TLS decryption
-
Question 253:
A security solution uses a sandbox environment to execute zero-day software and collect indicators of compromise. Which of the following should the organization do to BEST take advantage of this solution?
A. Develop an Nmap plug-in to detect the indicator of compromise.
B. Update the organization's group policy.
C. Include the signature in the vulnerability scanning tool.
D. Deliver an updated threat signature throughout the EDR system.
-
Question 254:
An organization's senior security architect would like to develop cyberdefensive strategies based on standardized adversary techniques, tactics, and procedures commonly observed. Which of the following would BEST support this objective?
A. OSINT analysis
B. The Diamond Model of Intrusion Analysis
C. MITRE ATTandCK
D. Deepfake generation
E. Closed-source intelligence reporting
-
Question 255:
An organization is looking to establish more robust security measures by implementing PKI. Which of the following should the security analyst implement when considering mutual authentication?
A. Perfect forward secrecy on both endpoints
B. Shared secret for both endpoints
C. Public keys on both endpoints
D. A common public key on each endpoint
E. A common private key on each endpoint
-
Question 256:
Prior to a risk assessment inspection, the Chief Information Officer tasked the systems administrator with analyzing and reporting any configuration issues on the information systems, and then verifying existing security settings. Which of the following would be BEST to use?
A. SCAP
B. CVSS
C. XCCDF
D. CMDB
-
Question 257:
Which of the following is used to assess compliance with internal and external requirements?
A. RACI matrix
B. Audit report
C. After-action report
D. Business continuity plan
-
Question 258:
A company wants to implement a new website that will be accessible via browsers with no mobile applications available. The new website will allow customers to submit sensitive medical information securely and receive online medical advice. The company already has multiple other websites where it provides various public health data and information. The new website must implement the following:
1.
The highest form of web identity validation
2.
Encryption of all web transactions
3.
The strongest encryption in-transit
4.
Logical separation based on data sensitivity
Other things that should be considered include:
1.
The company operates multiple other websites that use encryption.
2.
The company wants to minimize total expenditure.
3.
The company wants to minimize complexity.
Which of the following should the company implement on its new website? (Choose two.)
A. Wildcard certificate
B. EV certificate
C. Mutual authentication
D. Certificate pinning
E. SSO
F. HSTS
-
Question 259:
After installing an unapproved application on a personal device, a Chief Executive Officer reported an incident to a security analyst. This device is not controlled by the MDM solution, as stated in the BVOD policy. However, the device contained critical confidential information. The cyber incident response team performed the analysis on the device and found the following log:
Wed 12 Dec 2020 10:00:03 Unknown sources is now enabled on this device.
Which of the following is the MOST likely reason for the successful attack?
A. Lack of MDM controls
B. Jailbreaking
C. Sideloading
D. Lack of application segmentation
-
Question 260:
A network administrator for a completely air-gapped and closed system has noticed that anomalous external files have been uploaded to one of the critical servers. The administrator has reviewed logs in the SIEM that were collected from security appliances, network infrastructure devices, and endpoints. Which of the following processes, if executed, would be MOST likely to expose an attacker?
A. Reviewing video from IP cameras within the facility
B. Reconfiguring the SIEM connectors to collect data from the perimeter network hosts
C. Implementing integrity checks on endpoint computing devices
D. Looking for privileged credential reuse on the network
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.