CAS-004 Exam Details
-
Exam Code
:CAS-004 -
Exam Name
:CompTIA Advanced Security Practitioner (CASP+) -
Certification
:CompTIA Certifications -
Vendor
:CompTIA -
Total Questions
:740 Q&As -
Last Updated
:Jan 27, 2026
CompTIA CAS-004 Online Questions & Answers
-
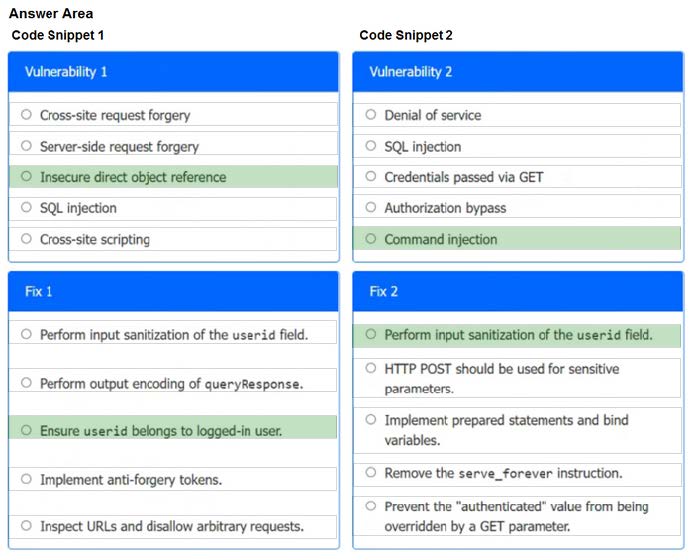
Question 1:
HOTSPOT
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Code Snippet 1
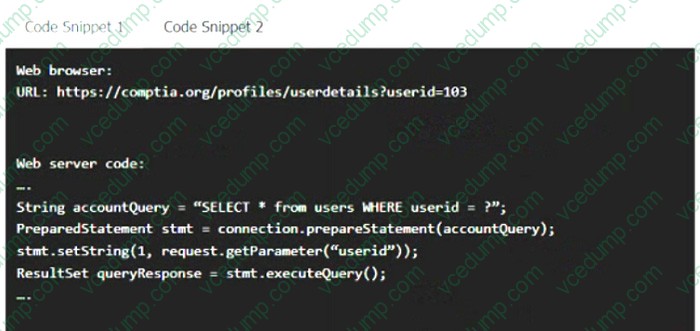
Code Snippet 2
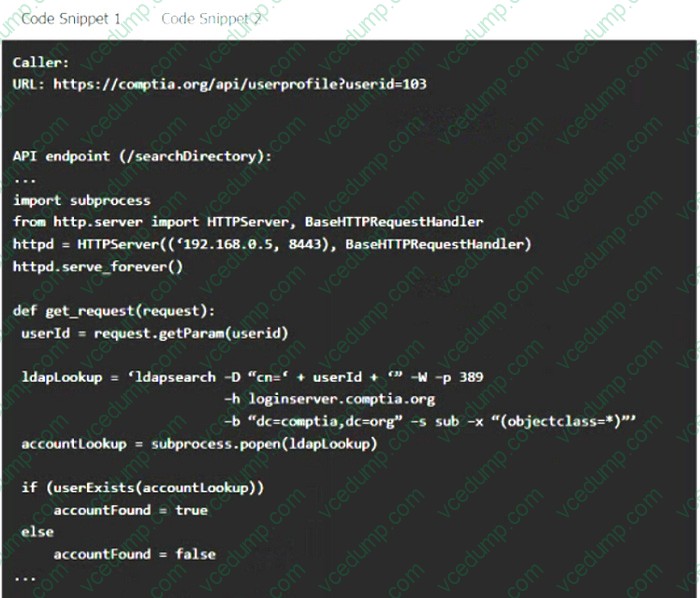
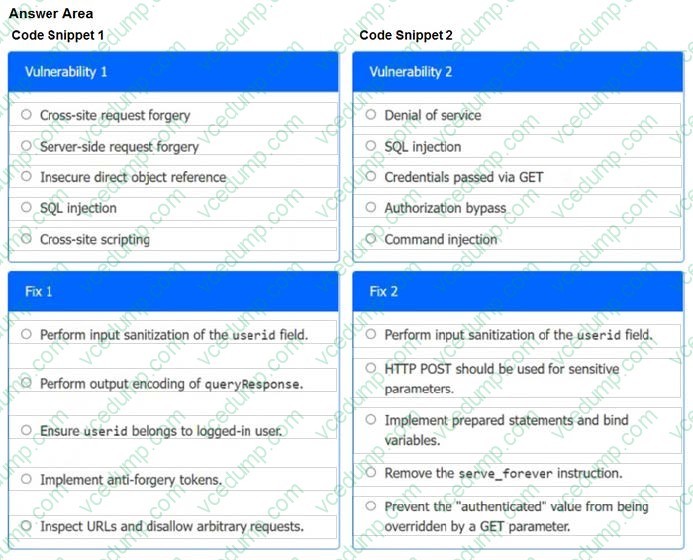
-
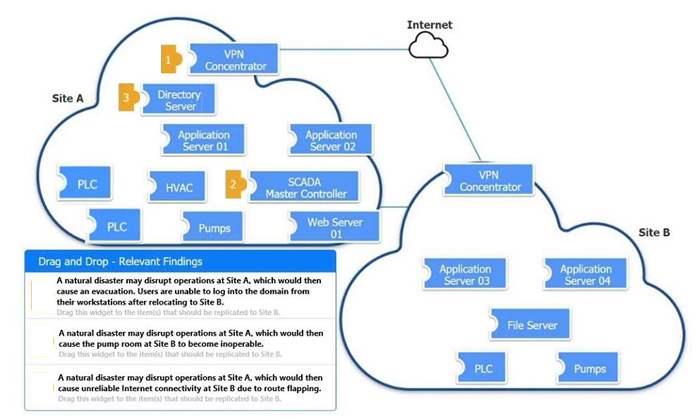
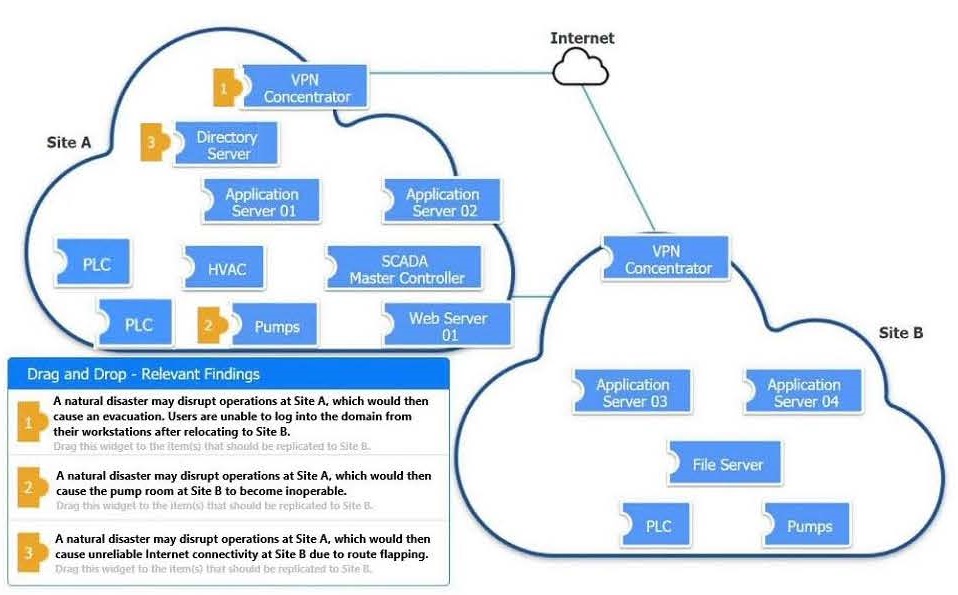
Question 2:
DRAG DROP
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
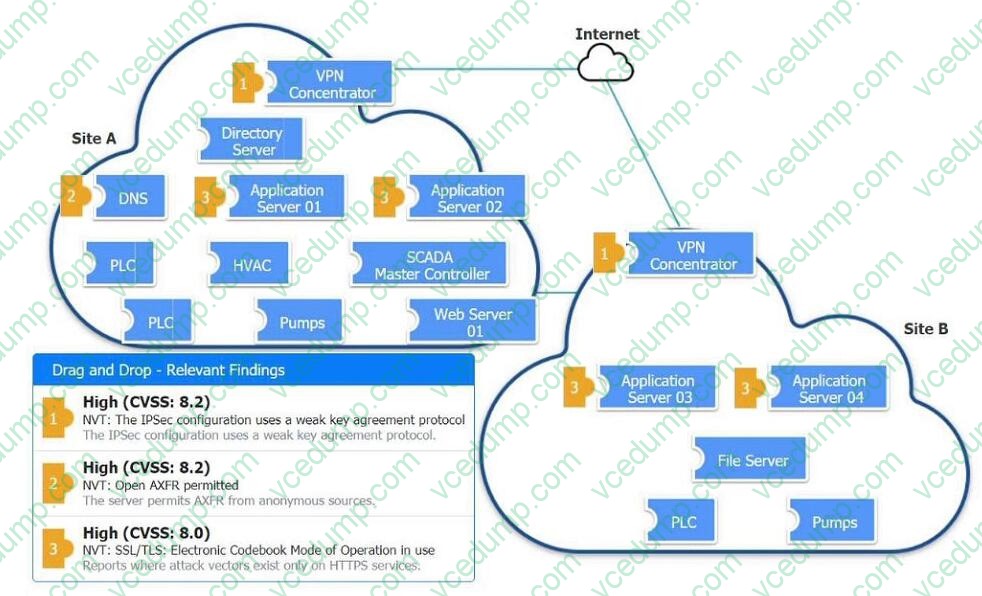
Select and Place:
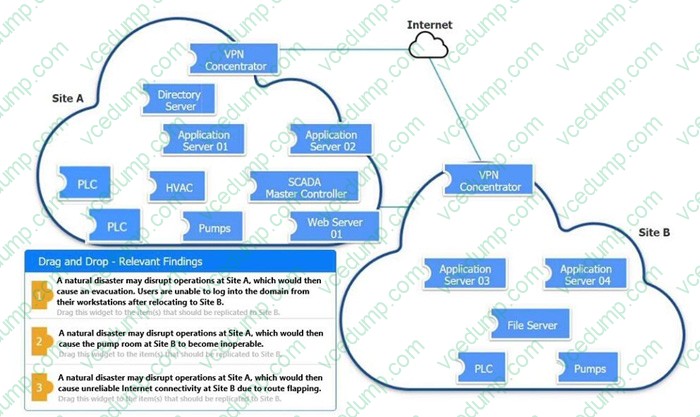
-
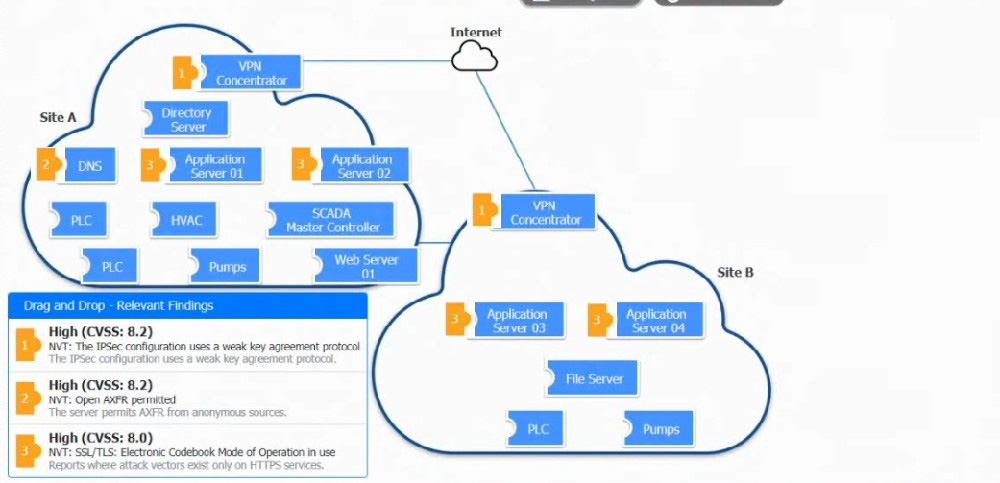
Question 3:
DRAG DROP
A vulnerability scan with the latest definitions was performed across Sites A and B.
INSTRUCTIONS
Match each relevant finding to the affected host.
After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
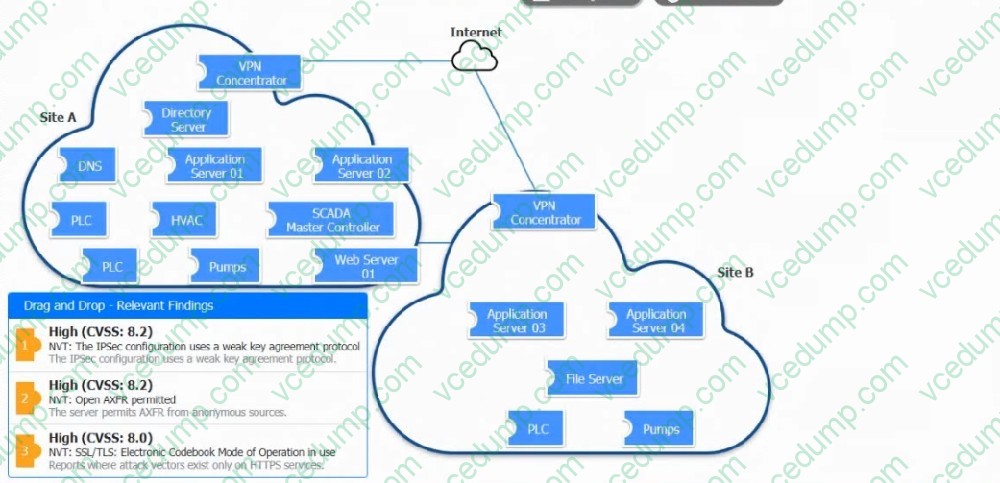
-
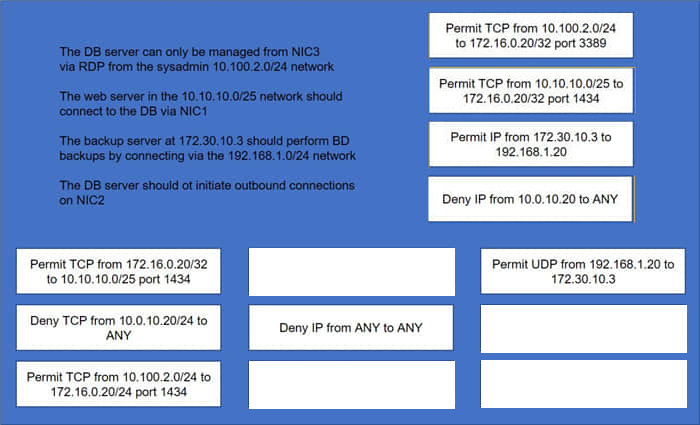
Question 4:
DRAG DROP
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.
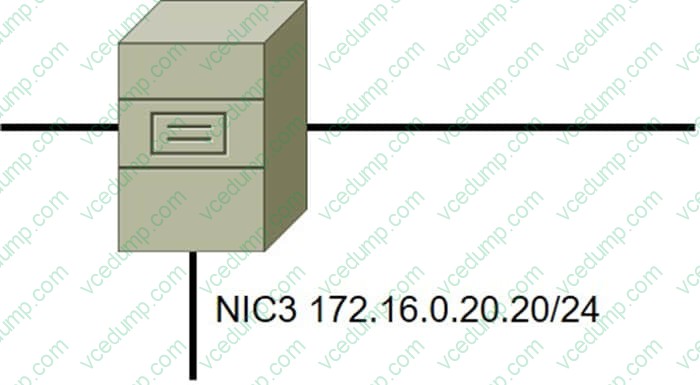
Select and Place:
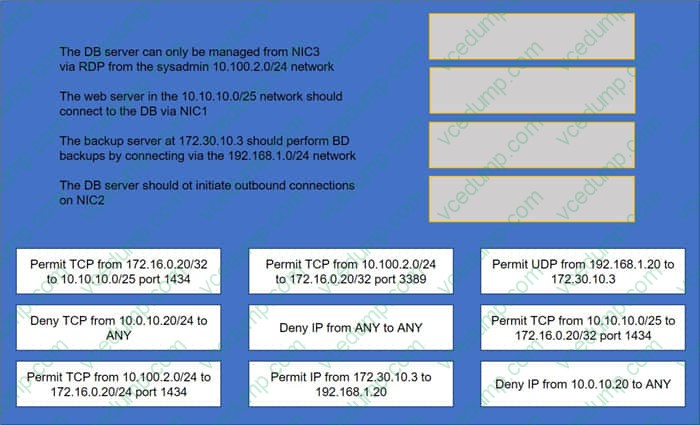
-
Question 5:
SIMULATION
During the course of normal SOC operations, three anomalous events occurred and were flagged as potential IoCs. Evidence for each of these potential IoCs is provided.
INSTRUCTIONS
Review each of the events and select the appropriate analysis and remediation options for each IoC.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
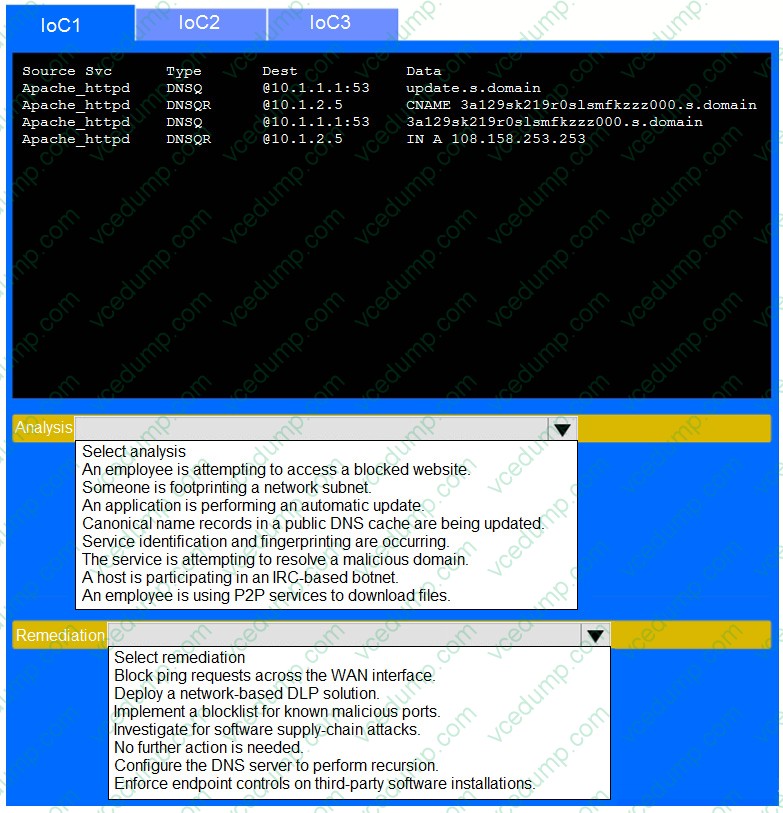
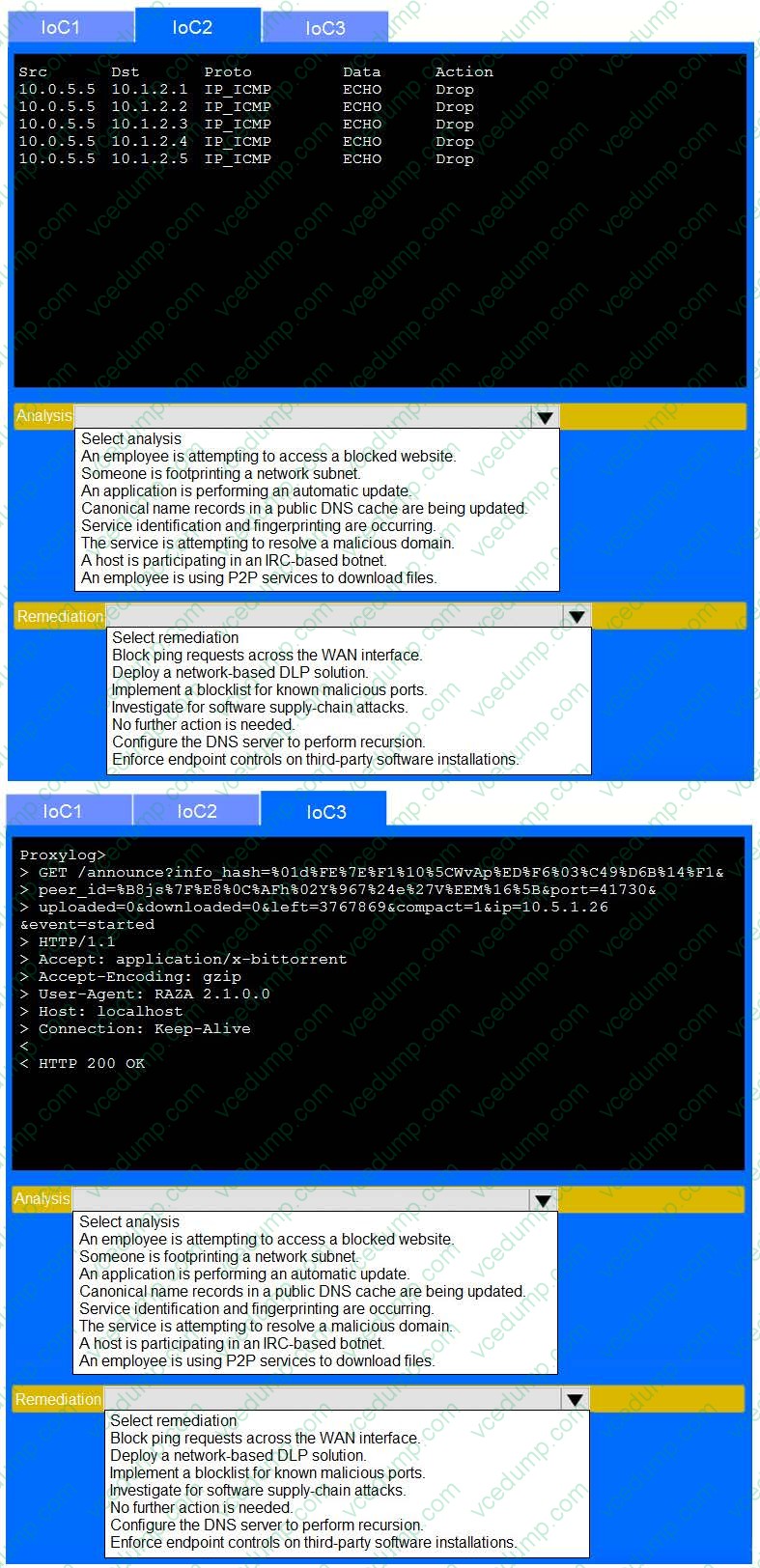
-
Question 6:
SIMULATION
You are about to enter the virtual environment.
Once you have completed the item in the virtual environment, you will NOT be allowed to return to this item.
Click Next to continue.
DO NOT perform the following actions within the virtual environment. Making any of these changes will cause the virtual environment to fail and prevent proper scoring.
1. Disabling ssh
2. Disabling systemd
3. Altering the network adapter 172.162.0.0
4. Changing the password in the lab admin account
Once you have completed the item in the virtual environment. you will NOT be allowed to return to this item.
This system was recently patched following the exploitation of a vulnerability by an attacker to enable data exfiltration.
Despite the vulnerability being patched, it is likely that a malicious TCP service is still running and the adversary has achieved persistence by creating a systemd service.
Examples of commands to use:
1. kill, killall
2. lsof
3. man, --help (use for assistance)
4. netstat (useful flags: a, n, g, u)
5. ps (useful flag: a)
6. systemctl (to control systemd)
Please note: the list of commands shown above is not exhaustive. All native commands are available.
INSTRUSTIONS
Using the following credentials:
1. Username: labXXXadmin
2. Password: XXXyyYzz!
Investigate to identify indicators of compromise and then remediate them. You will need to make at least two changes:
1. End the compromised process that is using a malicious TCP service.
2. Remove the malicious persistence agent by disabling the service’s ability to start on boot.
-
Question 7:
SIMULATION
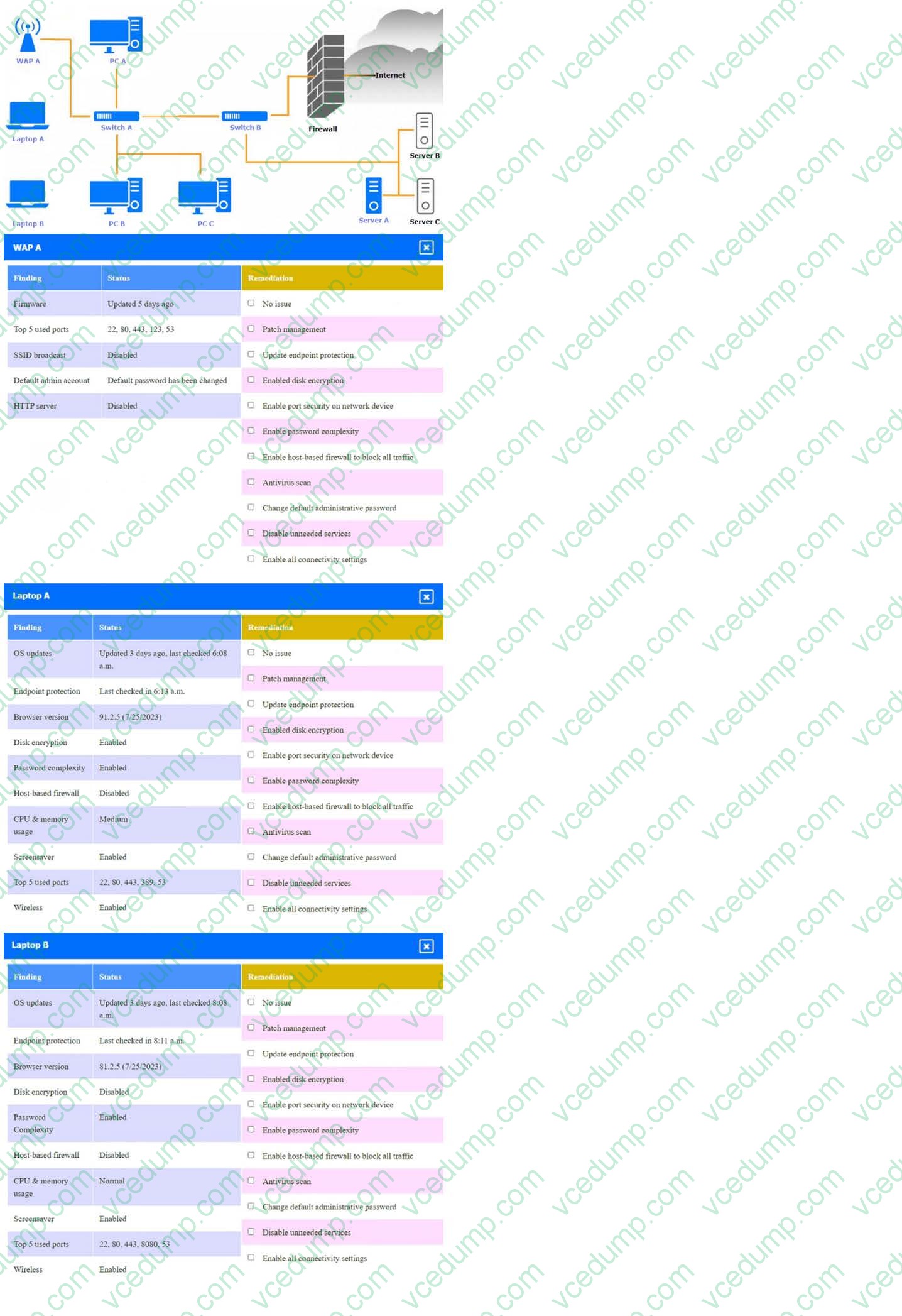
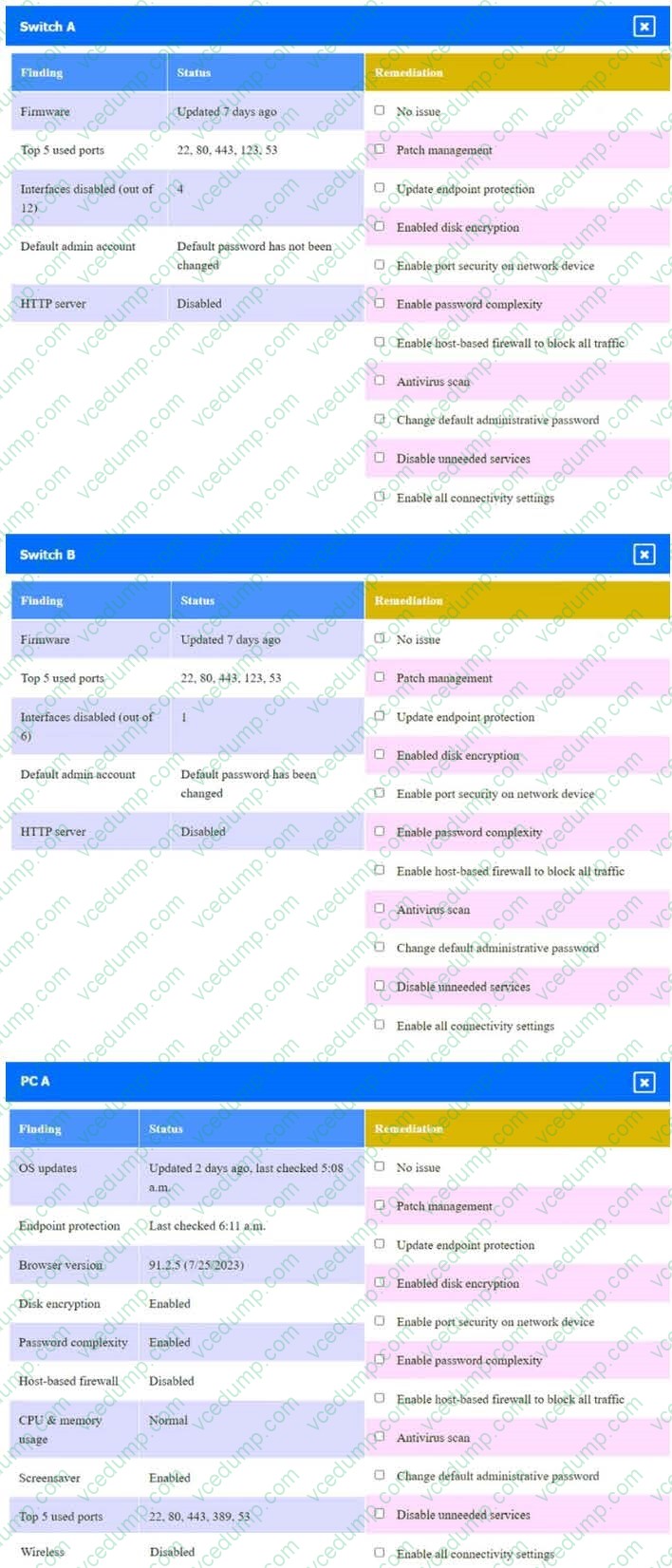
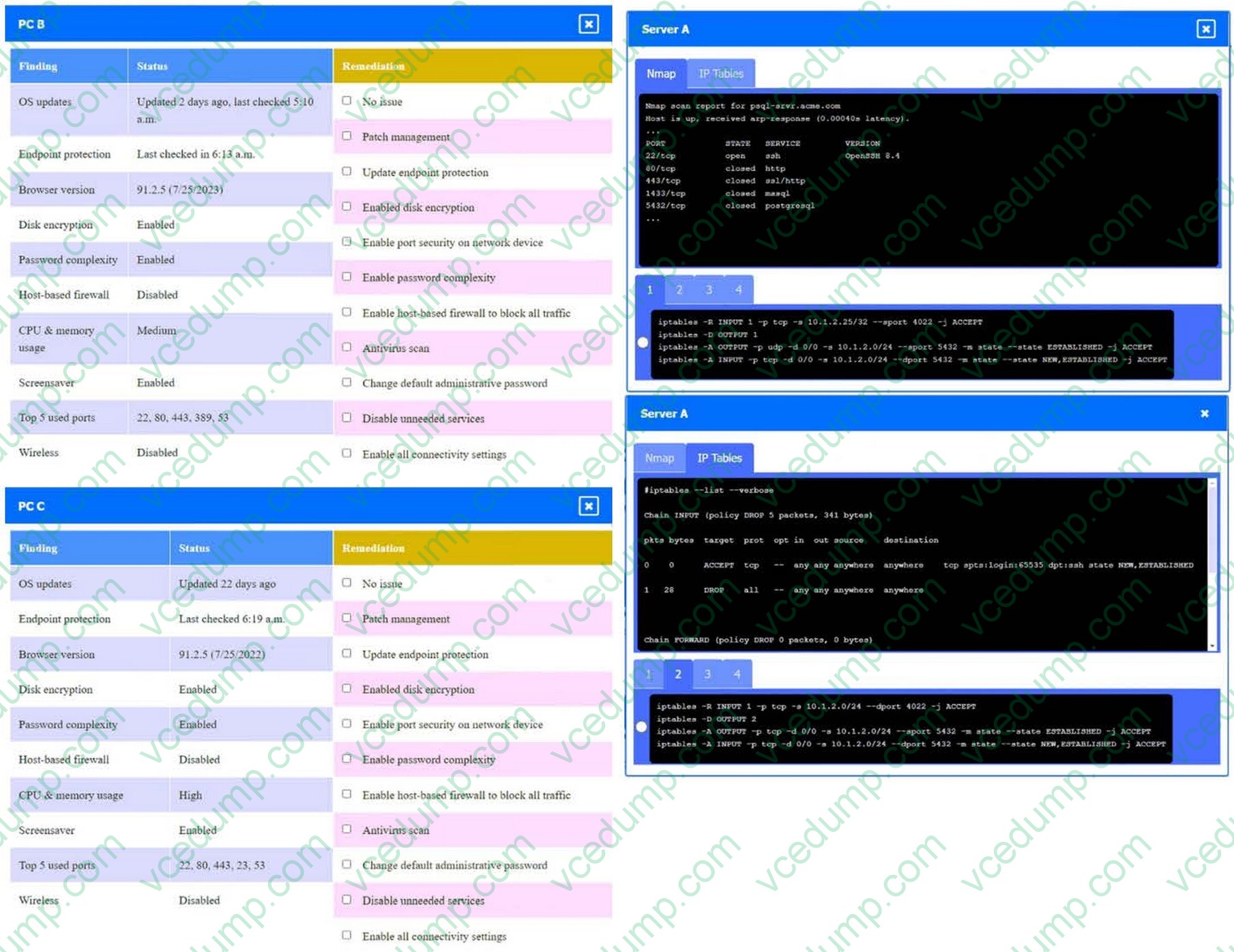
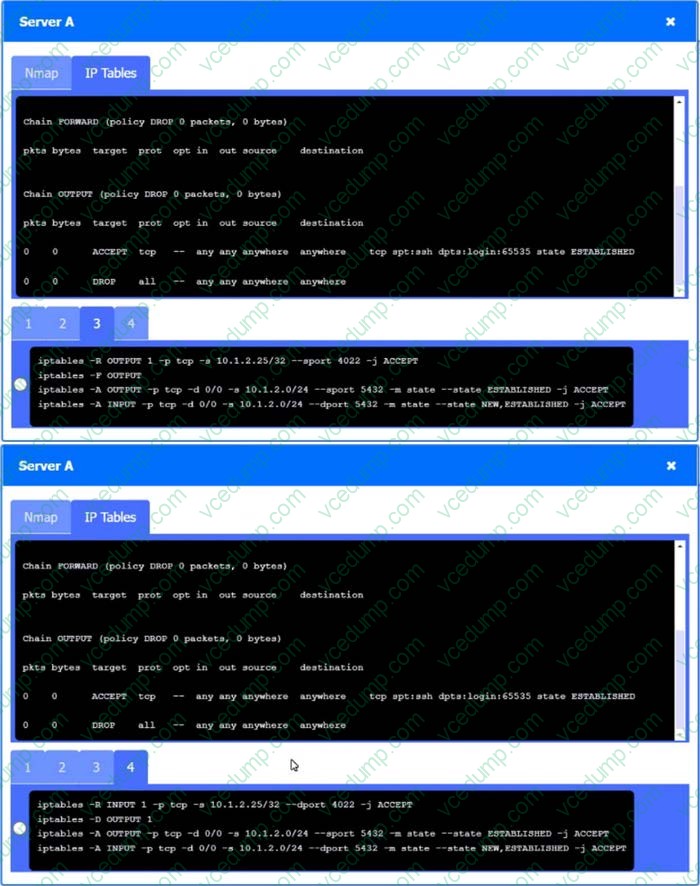
A security engineer needs to review the configurations of several devices on the network to meet the following requirements:
1. The PostgreSQL server must only allow connectivity in the 10.1.2.0/24 subnet.
2. The SSH daemon on the database server must be configured to listen to port 4022.
3. The SSH daemon must only accept connections from a single workstation.
4. All host-based firewalls must be disabled on all workstations.
5. All devices must have the latest updates from within the past eight days.
6. All HDDs must be configured to secure data at rest.
7. Cleartext services are not allowed.
8. All devices must be hardened when possible.
INSTRUCTIONS
Click on the various workstations and network devices to review the posture assessment results. Remediate any possible issues or indicate that no issue is found.
Click on Server A to review output data. Select commands in the appropriate tab to remediate connectivity problems to the PostgreSQL database via SSH.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
-
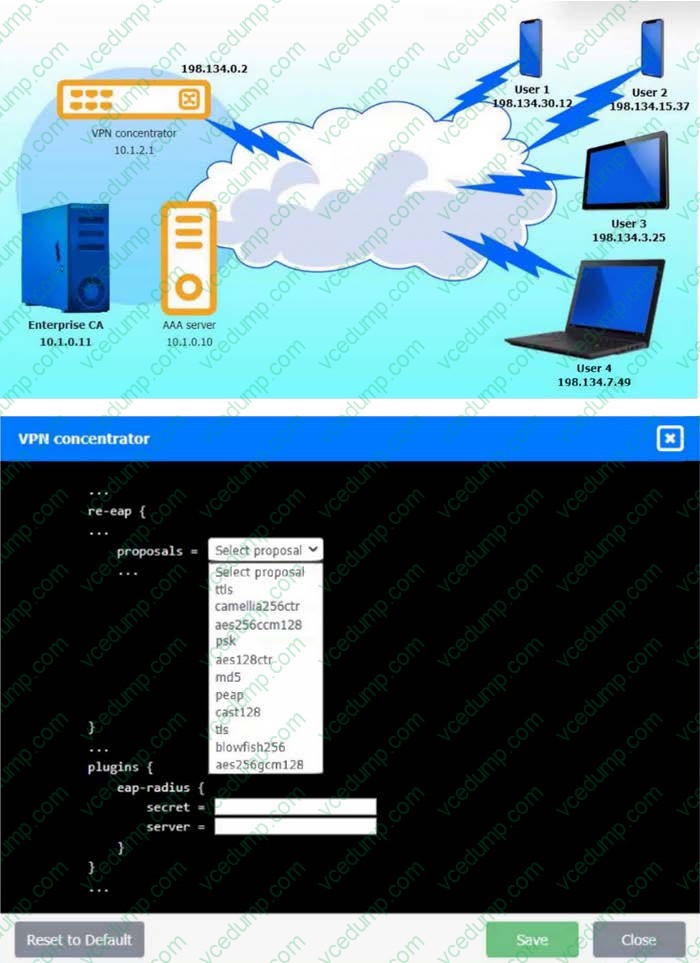
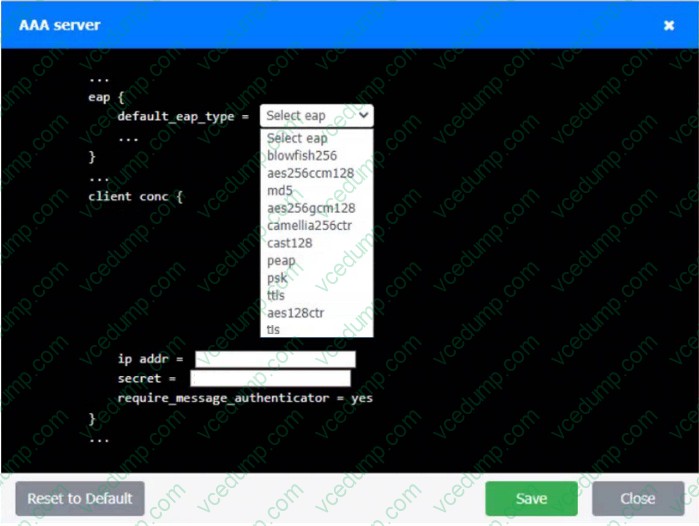
Question 8:
SIMULATION
An IPSec solution is being deployed. The configuration files for both the VPN concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
1. The EAP method must use mutual certificate-based authentication (with issued client certificates).
2. The IKEv2 cipher suite must be configured to the MOST secure authenticated mode of operation.
3. The secret must contain at least one uppercase character, one lowercase character, one numeric character, and one special character, and it must meet a minimum length requirement of eight characters.
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration. Fill in the appropriate fields and make selections from the drop-down menus.
If at any time you would like to bung back the initial state of the simulation, please click the Reset All button.
-
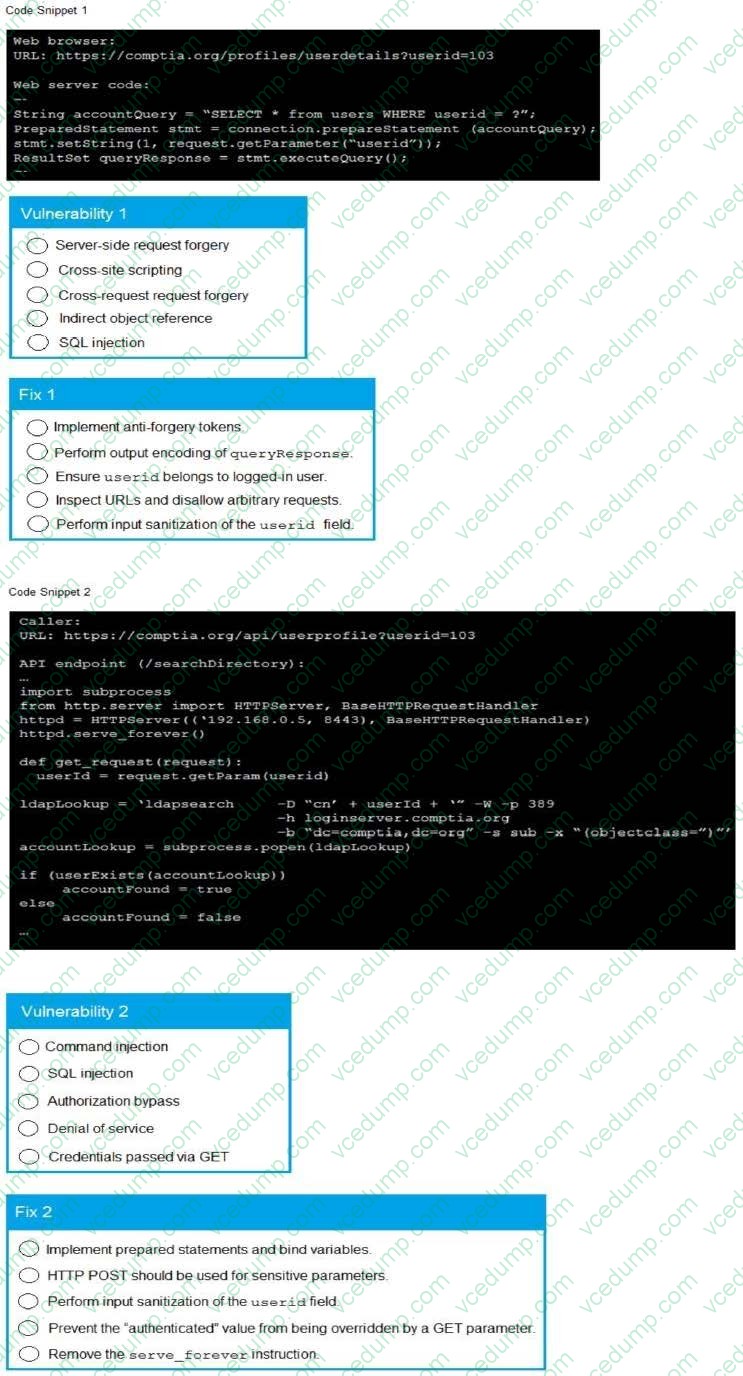
Question 9:
SIMULATION
A product development team has submitted code snippets for review pnor to release INSTRUCTIONS.
Analyze the code snippets and then select one vulnerability and one fix for each code snippet If at any time you would like to bang back the initial state of the simulation, please click the Reset All button.
-
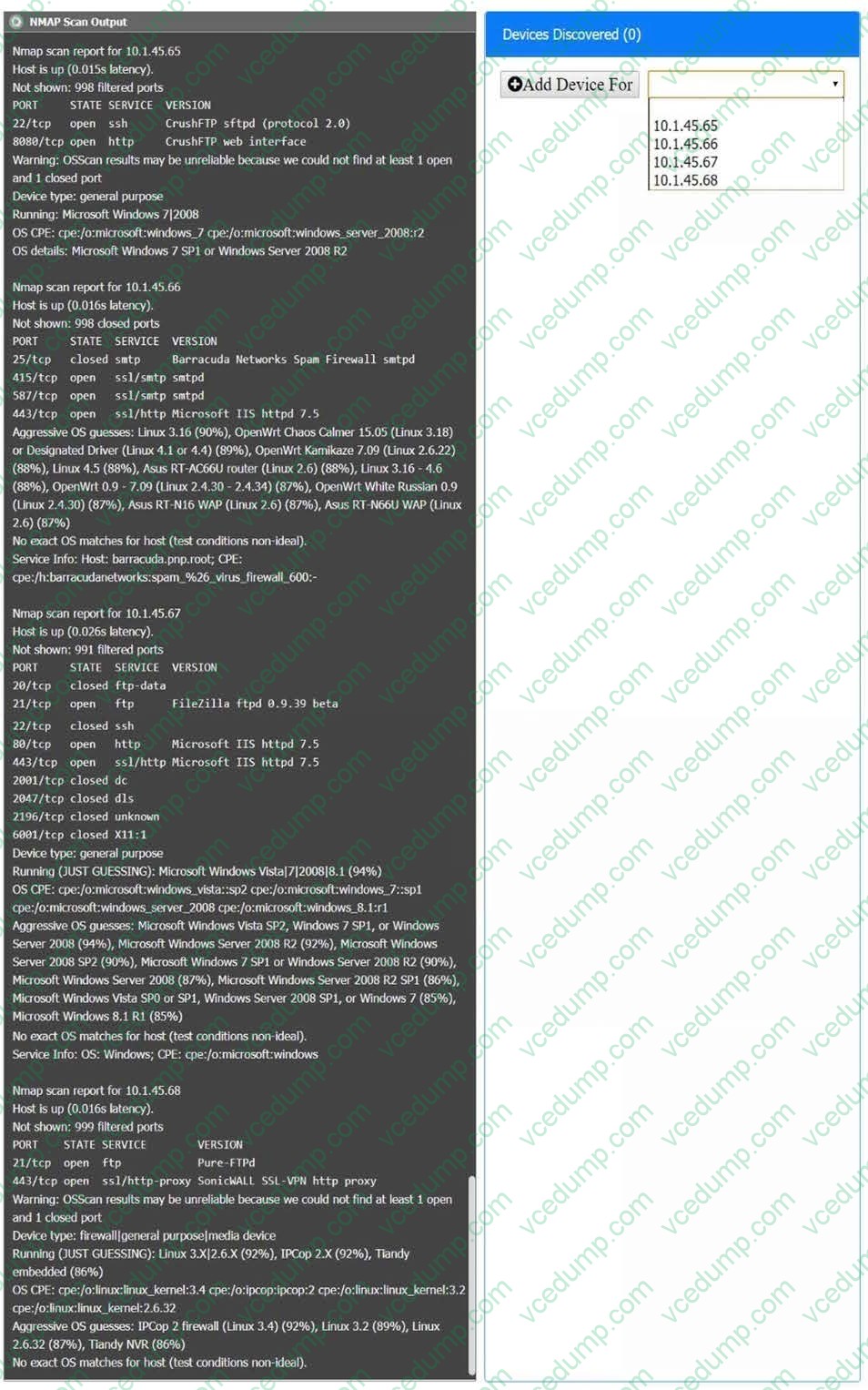
Question 10:
SIMULATION
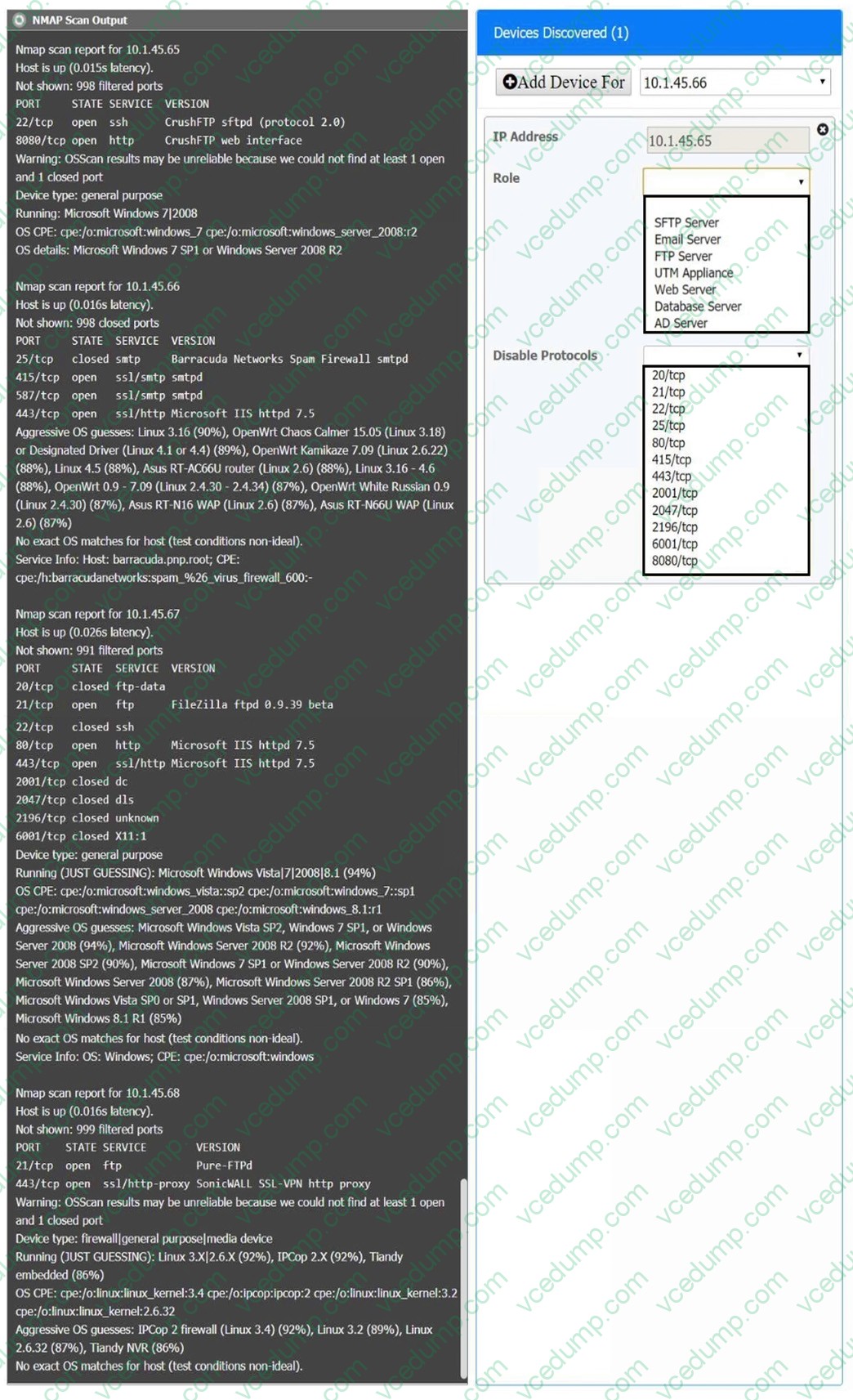
You are a security analyst tasked with interpreting an Nmap scan output from Company A’s privileged network.
The company’s hardening guidelines indicate the following:
1. There should be one primary server or service per device.
2. Only default ports should be used.
3. Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed. For each device found, add a device entry to the Devices Discovered list, with the following information:
1. The IP address of the device
2. The primary server or service of the device
3. The protocol(s) that should be disabled based on the hardening guidelines
To select multiple protocols, use CTRL+CLICK.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Related Exams:
-
220-1001
CompTIA A+ Certification: Core 1 -
220-1002
CompTIA A+ Certification: Core 2 -
220-1101
CompTIA A+ Certification: Core 1 -
220-1102
CompTIA A+ Certification: Core 2 -
220-1201
CompTIA A+ Certification: Core 1 -
220-1202
CompTIA A+ Certification: Core 2 -
220-902
CompTIA A+ Certification -
CAS-004
CompTIA Advanced Security Practitioner (CASP+) -
CAS-005
CompTIA SecurityX -
CLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.