Exam Details
Exam Code
:CAS-002Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:733 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-002 Questions & Answers
-
Question 221:
A Chief Information Security Officer (CISO) has been trying to eliminate some IT security risks for several months. These risks are not high profile but still exist. Furthermore, many of these risks have been mitigated with innovative solutions.
However, at this point in time, the budget is insufficient to deal with the risks.
Which of the following risk strategies should be used?
A. Transfer the risks
B. Avoid the risks
C. Accept the risks
D. Mitigate the risks
-
Question 222:
A mid-level company is rewriting its security policies and has halted the rewriting progress because the company's executives believe that its major vendors, who have cultivated a strong personal and professional relationship with the senior level staff, have a good handle on compliance and regulatory standards. Therefore, the executive level managers are allowing vendors to play a large role in writing the policy. Having experienced this type of environment in previous positions, and being aware that vendors may not always put the company's interests first, the IT Director decides that while vendor support is important, it is critical that the company writes the policy objectively. Which of the following is the recommendation the IT Director should present to senior staff?
A. 1) Consult legal, moral, and ethical standards; 2) Draft General Organizational Policy; 3) Specify Functional Implementing Policies; 4) Allow vendors to review and participate in the establishment of focused compliance standards, plans, and procedures
B. 1) Consult legal and regulatory requirements; 2) Draft General Organizational Policy; 3) Specify Functional Implementing Policies; 4) Establish necessary standards, procedures, baselines, and guidelines
C. 1) Draft General Organizational Policy; 2) Establish necessary standards and compliance documentation; 3) Consult legal and industry security experts; 4) Determine acceptable tolerance guidelines
D. 1) Draft a Specific Company Policy Plan; 2) Consult with vendors to review and collaborate with executives; 3) Add industry compliance where needed; 4) Specify Functional Implementing Policies
-
Question 223:
The security administrator at `company.com' is reviewing the network logs and notices a new UDP port pattern where the amount of UDP port 123 packets has increased by 20% above the baseline. The administrator runs a packet capturing tool from a server attached to a SPAN port and notices the following. UDP 192.168.0.1:123 -> 172.60.3.0:123 UDP 192.168.0.36:123 -> time.company.com UDP 192.168.0.112:123 -> 172.60.3.0:123 UDP 192.168.0.91:123 -> time.company.com UDP 192.168.0.211:123 -> 172.60.3.0:123 UDP 192.168.0.237:123 -> time.company.com UDP 192.168.0.78:123 -> 172.60.3.0:123
The corporate HIPS console reports an MD5 hash mismatch on the svchost.exe file of the following computers:
192.168.0.1
192.168.0.112
192.168.0.211
192.168.0.78
Which of the following should the security administrator report to upper management based on the above output?
A. An NTP client side attack successfully exploited some hosts.
B. A DNS cache poisoning successfully exploited some hosts.
C. An NTP server side attack successfully exploited some hosts.
D. A DNS server side attack successfully exploited some hosts.
-
Question 224:
The network administrator has been tracking the cause of network performance problems and decides to take a look at the internal and external router stats.
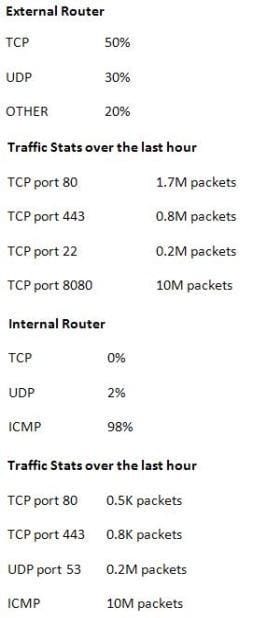
Which of the following should the network administrator do to resolve the performance issue after analyzing the above information?
A. The IP TOS field of business related network traffic should be modified accordingly.
B. The TCP flags of business related traffic should be modified accordingly.
C. An ACL should be placed on the external router to drop incoming ICMP packets.
D. An ACL should be placed on the internal router to drop layer 4 packets to and from port 0.
-
Question 225:
A corporation relies on a server running a trusted operating system to broker data transactions between different security zones on their network. Each zone is a separate domain and the only connection between the networks is via the
trusted server.
The three zones at the corporation are as followeD.
Zone A connects to a network, which is also connected to the Internet through a router.
Zone B to a closed research and development network.
Zone C to an intermediary switch supporting a SAN, dedicated to long- term audit log and file storage, so the corporation meets compliance requirements.
A firewall is deployed on the inside edge of the Internet connected router.
Which of the following is the BEST location to place other security equipment?
A. HIPS on all hosts in Zone A and B, and an antivirus and patch server in Zone C.
B. A WAF on the switch in Zone C, an additional firewall in Zone A, and an antivirus server in Zone B.
C. A NIPS on the switch in Zone C, an antivirus server in Zone A, and a patch server in Zone B.
D. A NIDS on the switch in Zone C, a WAF in Zone A, and a firewall in Zone B.
-
Question 226:
Which of the following implementations of a continuous monitoring risk mitigation strategy is correct?
A. Audit successful and failed events, transfer logs to a centralized server, institute computer assisted audit reduction, and email alerts to NOC staff hourly.
B. Audit successful and critical failed events, transfer logs to a centralized server once a month, tailor logged event thresholds to meet organization goals, and display alerts in real time when thresholds are approached.
C. Audit successful and failed events, transfer logs to a centralized server, institute computer assisted audit reduction, tailor logged event thresholds to meet organization goals, and display alerts in real time when thresholds are exceeded.
D. Audit failed events only, transfer logs to a centralized server, implement manual audit reduction, tailor logged event thresholds to meet organization goals, and display alerts in real time when thresholds are approached and exceeded.
-
Question 227:
When planning a complex system architecture, it is important to build in mechanisms to secure log information, facilitate audit log reduction, and event correlation. Besides synchronizing system time across all devices through NTP, which of the following is also a common design consideration for remote locations?
A. Two factor authentication for all incident responders
B. A central SYSLOG server for collecting all logs
C. A distributed SIEM with centralized sensors
D. A SIEM server with distributed sensors
-
Question 228:
The Chief Information Officer (CIO) of Company XYZ has returned from a large IT conference where one of the topics was defending against zero day attacks - specifically deploying third party patches to vulnerable software. Two months prior, the majority of the company systems were compromised because of a zero day exploit. Due to budget constraints the company only has operational systems. The CIO wants the Security Manager to research the use of these patches. Which of the following is the GREATEST concern with the use of a third party patch to mitigate another un-patched vulnerability?
A. The company does not have an adequate test environment to validate the impact of the third party patch, introducing unknown risks.
B. The third party patch may introduce additional unforeseen risks and void the software licenses for the patched applications.
C. The company's patch management solution only supports patches and updates released directly by the vendor.
D. Another period of vulnerability will be introduced because of the need to remove the third party patch prior to installing any vendor patch.
-
Question 229:
After a recent outbreak of malware attacks, the Chief Information Officer (CIO) tasks the new security manager with determining how to keep these attacks from reoccurring. The company has a standard image for all laptops/workstations and uses a host-based firewall and anti-virus. Which of the following should the security manager suggest to INCREASE each system's security level?
A. Upgrade all system's to use a HIPS and require daily anti-virus scans.
B. Conduct a vulnerability assessment of the standard image and remediate findings.
C. Upgrade the existing NIDS to NIPS and deploy the system across all network segments.
D. Rebuild the standard image and require daily anti-virus scans of all PCs and laptops.
-
Question 230:
Company GHI consolidated their network distribution so twelve network VLANs would be available over dual fiber links to a modular L2 switch in each of the company's six IDFs. The IDF modular switches have redundant switch fabrics and power supplies. Which of the following threats will have the GREATEST impact on the network and what is the appropriate remediation step?
A. Threat: 802.1q trunking attack Remediation: Enable only necessary VLANs for each port
B. Threat: Bridge loop Remediation: Enable spanning tree
C. Threat: VLAN hopping Remediation: Enable only necessary VLANs for each port
D. Threat: VLAN hopping Remediation: Enable ACLs on the IDF switch
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.