Exam Details
Exam Code
:CAS-002Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:733 Q&AsLast Updated
:Jan 22, 2024
CompTIA CompTIA Certifications CAS-002 Questions & Answers
-
Question 721:
Several business units have requested the ability to use collaborative web-based meeting places with third party vendors. Generally these require user registration, installation of client-based ActiveX or Java applets, and also the ability for the user to share their desktop in read-only or read-write mode. In order to ensure that information security is not compromised, which of the following controls is BEST suited to this situation?
A. Disallow the use of web-based meetings as this could lead to vulnerable client-side components being installed, or a malicious third party gaining read-write control over an internal workstation.
B. Hire an outside consultant firm to perform both a quantitative and a qualitative risk- based assessment. Based on the outcomes, if any risks are identified then do not allow web-based meetings. If no risks are identified then go forward and allow for these meetings to occur.
C. Allow the use of web-based meetings, but put controls in place to ensure that the use of these meetings is logged and tracked.
D. Evaluate several meeting providers. Ensure that client-side components do not introduce undue security risks. Ensure that the read-write desktop mode can either be prevented or strongly audited.
-
Question 722:
The security administrator is responsible for the confidentiality of all corporate data. The company's servers are located in a datacenter run by a different vendor. The vendor datacenter hosts servers for many different clients, all of whom have access to the datacenter. None of the racks are physically secured. Recently, the company has been the victim of several attacks involving data injection and exfiltatration. The security administrator suspects these attacks are due to several new network based attacks facilitated by having physical access to a system. Which of the following BEST describes how to adapt to the threat?
A. Apply port security to all switches, switch to SCP, and implement IPSec tunnels between devices.
B. Apply two factor authentication, require point to point VPNs, and enable log auditing on all devices.
C. Apply port security to all routers, switch to telnet, and implement point to point VPNs on all servers.
D. Apply three factor authentication, implement IPSec, and enable SNMP.
-
Question 723:
About twice a year a switch fails in a company's network center. Under the maintenance contract, the switch would be replaced in two hours losing the business $1,000 per hour. The cost of a spare switch is $3,000 with a 12-hour delivery time and would eliminate downtime costs if purchased ahead of time. The maintenance contract is $1,500 per year.
Which of the following is true in this scenario?
A. It is more cost-effective to eliminate the maintenance contract and purchase a replacement upon failure.
B. It is more cost-effective to purchase a spare switch prior to an outage and eliminate the maintenance contract.
C. It is more cost-effective to keep the maintenance contract instead of purchasing a spare switch prior to an outage.
D. It is more cost-effective to purchase a spare switch prior to an outage and keep the maintenance contract.
-
Question 724:
An organization is implementing a project to simplify the management of its firewall network flows and implement security controls. The following requirements exist. Drag and drop the BEST security solution to meet the given requirements.
Options may be used once or not
at all. All placeholders must be filled.
Select and Place:

-
Question 725:
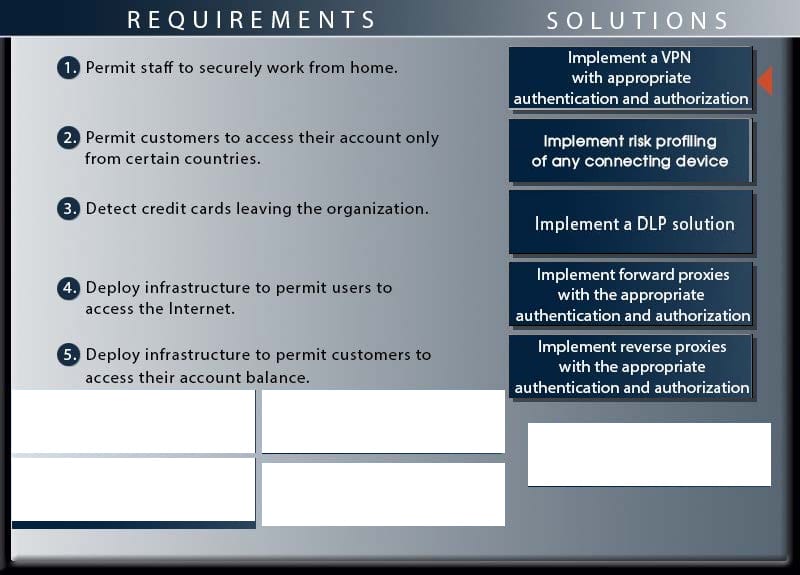
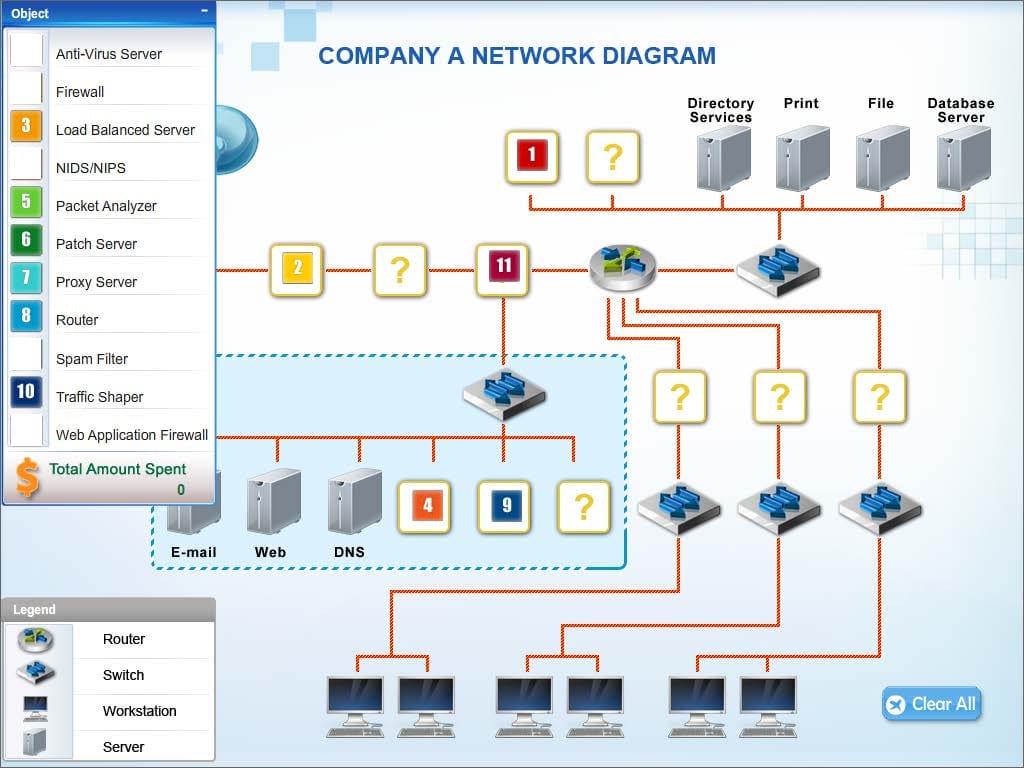
Company A has experienced external attacks on their network and wants to minimize the attacks from reoccurring. Modify the network diagram to prevent SQL injections, XSS attacks, smurf attacks, e-mail spam, downloaded malware, viruses and ping attacks. The company can spend a MAXIMUM of $50,000 USD. A cost list for each item is listed below:
1.
Anti-Virus Server - $10,000
2.
Firewall-$15,000
3.
Load Balanced Server - $10,000
4.
NIDS/NIPS-$10,000
5.
Packet Analyzer - $5,000
6.
Patch Server-$15,000
7.
Proxy Server-$20,000
8.
Router-$10,000
9.
Spam Filter-$5,000
10.
Traffic Shaper - $20,000
11.
Web Application Firewall - $10,000
Instructions: Not all placeholders in the diagram need to be filled and items can only be used once. If you place an object on the network diagram, you can remove it by clicking the (x) in the upper right-hand of the object.
Select and Place:

-
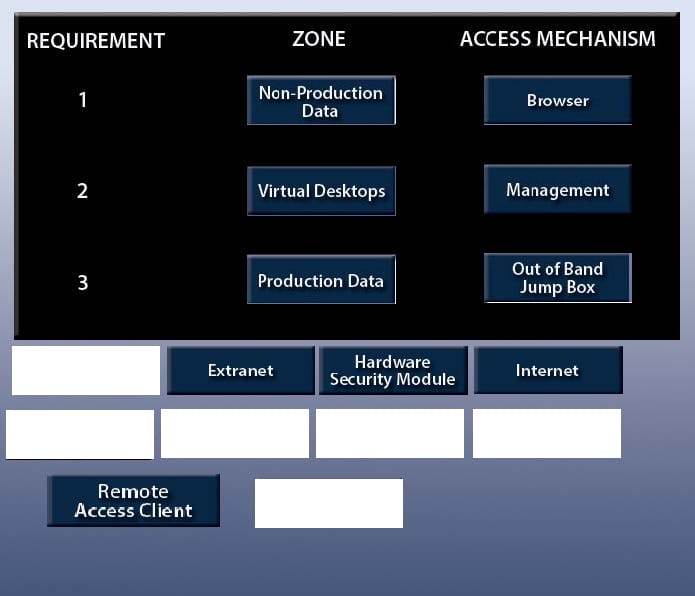
Question 726:
A manufacturer is planning to build a segregated network. There are requirements to segregate development and test infrastructure from production and the need to support multiple entry points into the network depending on the service being accessed. There are also strict rules in place to only permit user access from within the same zone. Currently, the following access requirements have been identified:
1.
Developers have the ability to perform technical validation of development applications.
2.
End users have the ability to access internal web applications.
3.
Third-party vendors have the ability to support applications.
In order to meet segregation and access requirements, drag and drop the appropriate network zone that the user would be accessing and the access mechanism to meet the above criteria. Options may be used once or not at all. All placeholders must be filled.
Select and Place:

-
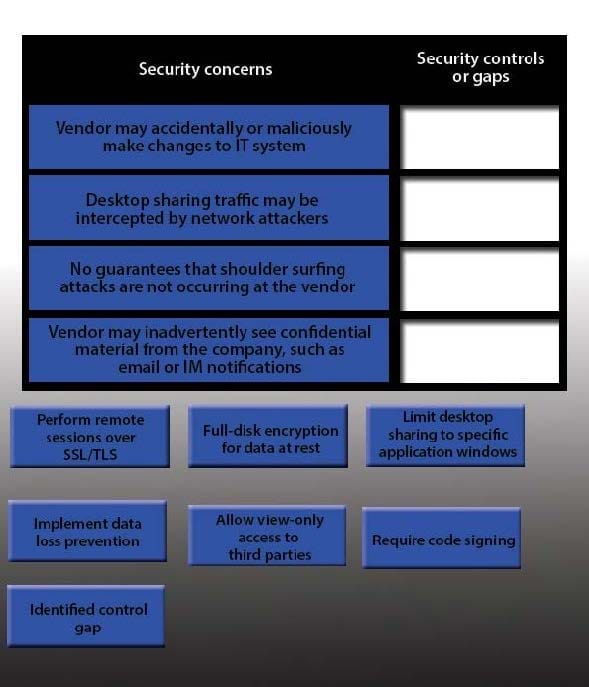
Question 727:
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern. Options may be used once or not at all.
Select and Place:
-
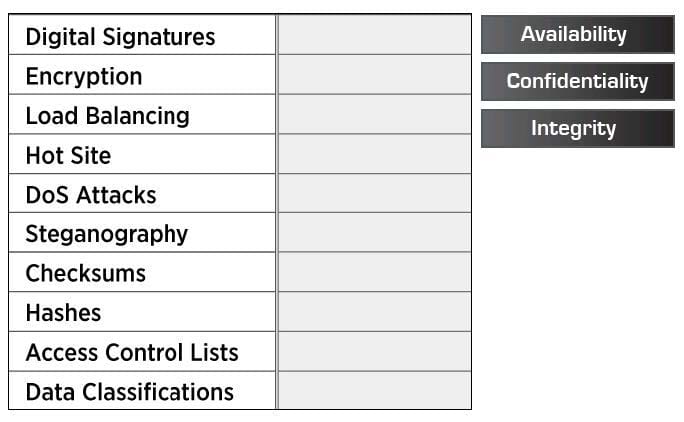
Question 728:
Drag and Drop the following information types on to the appropriate CIA category.
Select and Place:
-
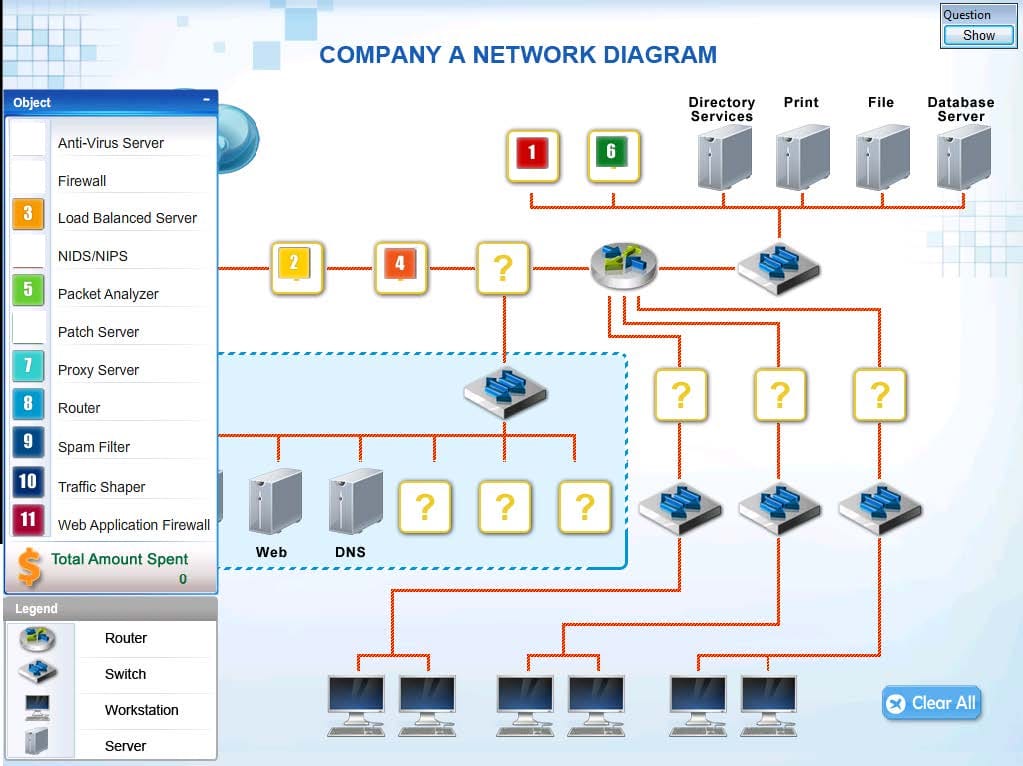
Question 729:
Company A has experienced external attacks on their network and wants to minimize the attacks from reoccurring. Modify the network diagram to prevent SQL injections. XSS attacks, smurf attacks, e-mail spam, downloaded malware. viruses and ping attacks. The company can spend a MAXIMUM of 550.000 USD. A cost list for each item is listed below
1. Anti-Virus Server- $10,000 2 Firewall-$15,000 3 Load Balanced Server - $10,000 4 NIDS/NIPS-$10,000
5. Packet Analyzer-55.000 6 Patch Server-$15,000 7 Proxy Server-$20,000 8. Router - S10.000 9 Spam Filter - S5 000 10 Traffic Shaper - $20,000
11. Web Application Firewall - $10,000
Instructions: Not all placeholders in the diagram need to be filled and items can only be used once.
Select and Place:

-
Question 730:
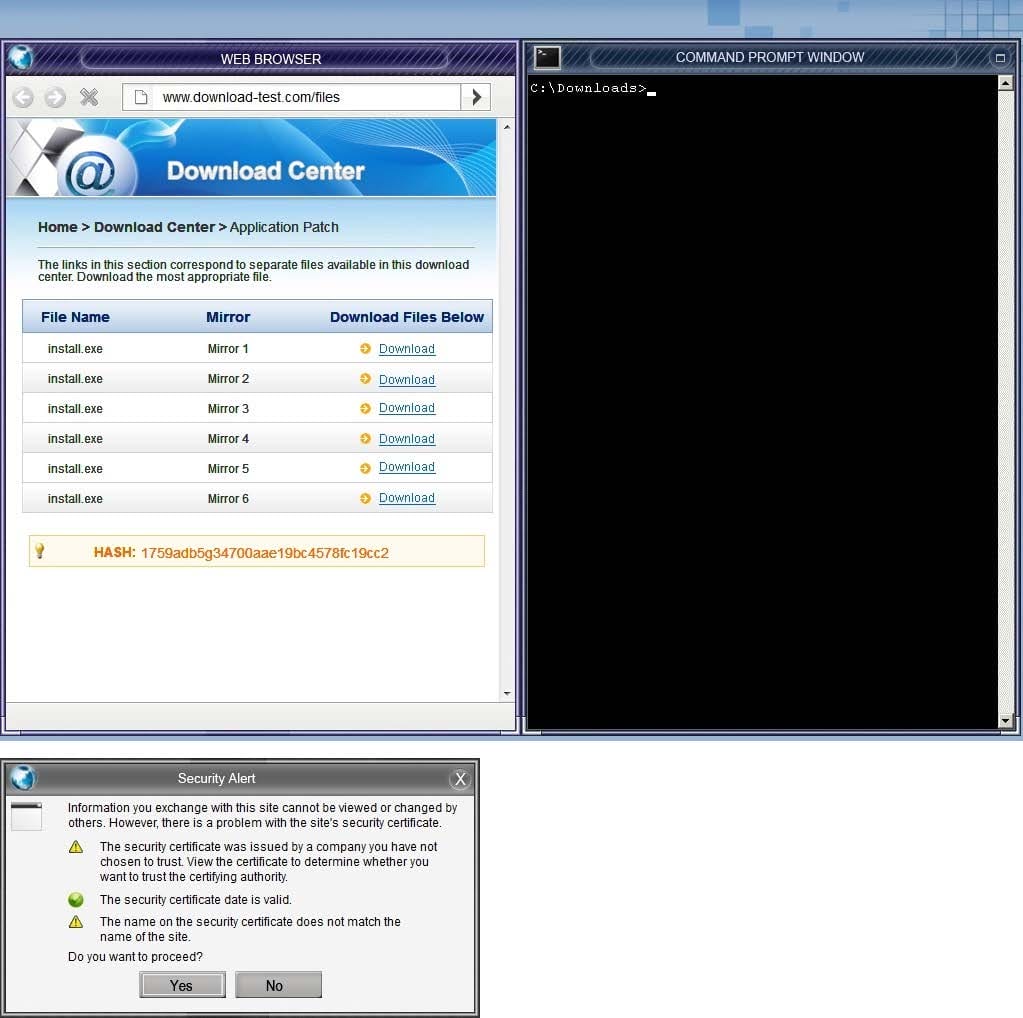
CORRECT TEXT
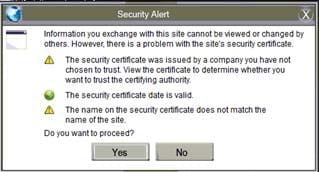
An administrator wants to install a patch to an application. Given the scenario, download, verify and install the patch in the most secure manner.
Instructions: The last install that is completed will be the final submission.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.