Exam Details
Exam Code
:S90-20AExam Name
:SOA Security LabCertification
:SOA CertificationsVendor
:SOATotal Questions
:30 Q&AsLast Updated
:Jun 23, 2025
SOA SOA Certifications S90-20A Questions & Answers
-
Question 21:
Service A provides a data access capability that can be used by a variety of service consumers. The database records accessed by Service A are classified as either private or public. There are two types of service consumers that use Service A: Service consumers with public access permissions (allowed to access only public data records) and service consumers with private access permissions (allowed to access all data records). For performance reasons the Service A architecture uses a single database, named Database A. Each record in Database A is classified as either private or public. After Service A is invoked by a service consumer (1), it authenticates the request message using an identity store and retrieves the corresponding authorization (2, 3). Once authorized, the service consumer's request is submitted to Database A (4), which then returns the requested data (5) If the service consumer has private access permissions, all of the returned data is included in Service A's response message (6). If the service consumer has public access permissions, then Service A first filters the data in order to remove all unauthorized private data records before sending to the response message to the service consumer (6).
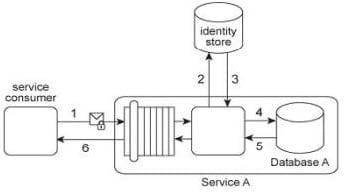
In addition to retrieving data, Service A's data access capability can be used to update database records. An investigation recently revealed an information leakage problem that can occur when service consumers with public access permissions attempt to update the ID value of a database record The ID values of all database records (private or public) must be unique. When a service consumer with public access permissions updates a public database record with an ID value that is already assigned to a private database record, the database returns an error message describing this conflict. This error text reveals confidential information by stating that the ID value submitted by the service consumer with public access permissions already exists within a private database record. What steps can be taken to avoid this problem while preserving the requirement that all database records (private and public) have unique ID values?
A. The Exception Shielding pattern is applied to replace the error description text before a response message is returned to the service consumer. Furthermore, the ID value of all database records is appended with a code indicating whether the database record is private or public
B. The database rules are changed so that the ID value of database records no longer needs to be unique. As a further precaution, the Service A logic is changed to disallow the update of private database records by service consumers with only public access permissions.
C. The service consumer's request message containing the ID value can be encrypted by inserting the private key of the service consumer into the data. Because all service consumers have different private keys, this approach will lead to different encrypted values, even if the plain text ID values are the same. As a result, two data items with the same encrypted unique identifier cannot exist.
D. When Service A detects that a service consumer with public access permissions has submitted an ID value that already exists within a private database record, it stores the service consumer's ID value in a temporary database and returns a response message indicating that the update was successful. A notification message is then sent to a human database administrator who manually contacts the owner of the service consumer in order to explain that the ID value submitted cannot be accepted because it already exists within a private database record.
-
Question 22:
Service A provides a data retrieval capability that can be used by a range of service consumers, including
Service Consumer A. In order to retrieve the necessary data, Service Consumer A first sends a request
message to Service A (1). Service A then exchanges request and response messages with Service B (2,
3), Service C (4, 5), and Service D (6.
7). After receiving all three response messages from Services B. C. and D, Service A assembles the
collected data into a response message that it returns to Service Consumer A (8).
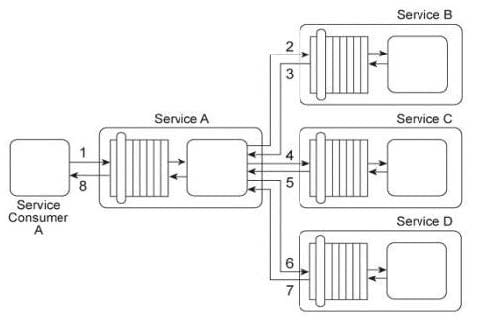
The owner of Service A charges service consumers for each usage of the data retrieval capability. Recently, the owner of Service Consumer A has complained that the data returned by Service A is incorrect, incomplete, and from invalid sources. As evidence, the Service Consumer A owner has presented the owner of Service A with sample messages containing the incorrect and incomplete contents. As a result, the Service Consumer A owner has refused to pay the usage fees. Subsequent to an internal investigation, the owner of Service A determines that the data returned by Service A is consistently correct and complete. There are suspicions that the Service Consumer A owner is altering the original messages and issuing these complaints fraudulently in order to avoid paying the usage fees. How can the owner of Service A prove that Service A is returning correct and complete data and that this data originated from the correct sources?
A. Apply the Data Origin Authentication and the Data Confidentiality patterns to ensure that request and response messagesexchanged between Service A and Services B. C, and D are digitally signed and encrypted. This guarantees message integrity and confidentiality.
B. Apply the Data Origin Authentication pattern to verily that request and response messages exchanged by Service Consumer A and Service A and exchanged by Service A and Services B, C, and D originated from the claimed sources and have not been altered prior to transmission. Also, enhance the Service A architecture so that all messages sent to its service consumers are logged.
C. Apply the Brokered Authentication pattern to send the security credentials of Service Consumer A to Services B, C, and D.Service A can carry out the brokered authentication logic and therefore act as the intermediary security broker. Upon receiving Service Consumer A's request message, Service A can further verify the credentials against an external certificate authority,if the request is authenticated. Service A can create a signed SAML assertion containing Service Consumer A's credentials and the authorization information. Service A then forwards the original request message and the signed SAML assertion to Services B,C,andD.
D. The service contract of Service A can be extended with an ignorable WS-Policy assertion that states that all request and response messages are logged by Service A and that false complaints will be prosecuted.
-
Question 23:
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement message (2) and then processes the request and sends a request message to Service B (3). This message contains confidential financial data. Service B sends three different request messages together with its security credentials to Services C. D. and E (4, 5, 6). Upon successful authentication, Services C.
D. and E store the data from the message in separate databases (7.8, 9). Services B. C. D, and E belong to Service Inventory A, which further belongs to Organization B. Service Consumer A and Service A belong to Organization A.

Organization B decides to create a new service inventory (Service Inventory B) for services that handle confidential data. Access to these services is restricted by allocating Service Inventory B its own private network. Access to this private network is further restricted by a dedicated firewall. Services C, D and E are moved into Service Inventory B, and as a result. Service B can no longer directly access these services. How can this architecture be changed to allow Service B to access Services C, D and E in a manner that does not jeopardize the security of Service Inventory B while also having a minimal impact on the service composition's performance?
A. The Service Perimeter Guard pattern is applied together with the Brokered Authentication pattern. A new perimeter service is created to intercept all request messages sent to services inside the private network (inside Service Inventory B),before they reach the firewall. The perimeter service also acts as the authentication broker that authenticates request messages sent to Services C, D, and E by evaluating the accompanying security credentials and issuing a security token to be used by Service B when accessing Services C, D, and E.
B. The Service Perimeter Guard pattern is applied together with the Message Screening pattern. A new perimeter service iscreated specifically for Service Inventory B. This service filters all messages before they reach the firewall and further evaluates the IP address of the messages to verify the identity of the message originators. If the originator is successfully authenticated, then the perimeter guard checks the request message for potentially malicious content. If the request message does not contain malicious content, it is sent through the firewall to proceed to Services C, D, and E for further processing.
C. The Brokered Authentication pattern is applied by extending the firewall functionality with a single sign-on mechanism. Because the firewall already restricts accesses to Service Inventory B, adding authentication logic to the firewall optimizes the performance of the overall security architecture. Service B needs to be authenticated by the authentication broker only once in order to get a security token that can be used to access Services C,D,and E. This eliminates the need for Service B to authenticate several times during the same service composition.
D. The Data Confidentiality pattern is applied together with the Direct Authentication pattern. A new utility service is created tovalidate request messages sent to Service Inventory B. Service B must encrypt the message content using the utility service's public key and attach its own digital certificate to the request message. This message is first evaluated by the firewall to filter out requests from disallowed sources and can then be forwarded to the utility service, which then verifies the identity of the message originator (using a digital certificate) and decrypts the request message contents. If the originator is authorized to access Services C, D, and E, the appropriate request messages are sent to these services.
-
Question 24:
Service Consumer A submits a request message with security credentials to Service A (1). The identity store that Service A needs to use in order to authenticate the security credentials can only be accessed via a legacy system that resides in a different service inventory. Therefore, to authenticate Service Consumer A, Service A must first forward the security credentials to the legacy system (2). The legacy system then returns the requested identity to Service A (3). Service A authenticates Service Consumer A against the identity received from the legacy system. If the authentication is successful, Service A retrieves the requested data from Database A (4), and returns the data in a response message sent back to Service Consumer A (5). Service A belongs to Service Inventory A which further belongs to Security Domain A and the legacy system belongs to Service Inventory B which further belongs to Security Domain B. (The legacy system is encapsulated by other services within Service Inventory B, which are not shown in the diagram.) These two security domains trust each other. Communication between Service A and the legacy system is kept confidential using transport-layer security.
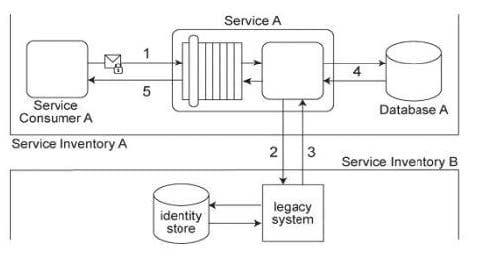
It was recently discovered that a malicious attacker, posing as Service Consumer A, has been accessing Service A. An investigation revealed that these attacks occurred because security credentials supplied by Service Consumer A were transmitted in plaintext. Furthermore, vulnerabilities to replay attacks and malicious intermediaries have been detected. Which of the following statements describes a solution that can counter these types of attacks? Also, list the industry standards required by the proposed solution.
A. Apply the Data Origin Authentication pattern together with the Data Confidentiality pattern in order to establish message-layer security that guarantees the confidentiality and integrity of messages exchanged by Service Consumer A and Service A. Further, a security policy can be created to require that security credentials submitted to Service A must be digitally signed and encrypted and also contain a timestamp to validate the actual time the request was issued. Industry standards that can be used for this solution are WS- Policy, WS-SecurityPolicy, XML- Encryption, and XML-Signature.
B. Apply the Service Perimeter Guard pattern together with the Trusted Subsystem pattern to establish a perimeter service that can perform security functions on behalf of Service A. Theutility service can verify the validity of the request messages from Service Consumer A by authenticating the request message against an identity store. If the request message is authenticated, the utility service then sends it to Service A for further processing. All communications between Service A and Service Consumer A can be encrypted using the public key of the intended recipient, and signed using the private key of the sender. Industry standards that can be used for this solution are XML-Encryption, XML- Signature, and WS-Trust.
C. Apply the Service Perimeter Guard pattern to establish a perimeter service that can perform security functions on behalf ofService A. Next, apply the Data Confidentiality pattern so that the security credential information provided by Service Consumer A with the request message is encrypted with the secret key shared between the perimeter service and Service Consumer A. The perimeter service evaluates the credentials and if successfully authenticated, forwards the request message to Service A. Transport-layer security is used to protect message exchanges between Service A and Service Consumer
D.
E. Apply the Trusted Subsystem pattern together with the Data Origin Authentication pattern in order to establish a utility servicethat performs the security processing on behalf of Service A. Service Consumer A must digitally sign all request messages and encrypt the credential information using the public key of the utility service. The utility service can then verify the security credentials and the digital signature to establish the validity of the request message. If the request message is permitted, the utility service establishes a composite trust domain that encompasses Service Consumer A, Service A, Database A, and the legacy system. Because all communications remain within a single trust domain, malicious intermediaries will not be able to gain access to any exchanged data.
-
Question 25:
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message to Service B (2). Service B forwards the message to have its contents calculated by Service C (3). After receiving the results of the calculations via a response message from Service C (4), Service B then requests additional data by sending a request message to Service D (5). Service D retrieves the necessary data from Database A (6), formats it into an XML document, and sends the response message containing the XML-formatted data to Service B (7). Service B appends this XML document with the calculation results received from Service C, and then records the entire contents of the XML document into Database B (8). Finally, Service B sends a response message to Service A (9) and Service A sends a response message to Service Consumer A (10). Services A, B and D are agnostic services that belong to Organization A and are also being reused in other service compositions. Service C is a publicly accessible calculation service that resides outside of the organizational boundary. Database A is a shared database used by other systems within Organization A and Database B is dedicated to exclusive access by Service
B.
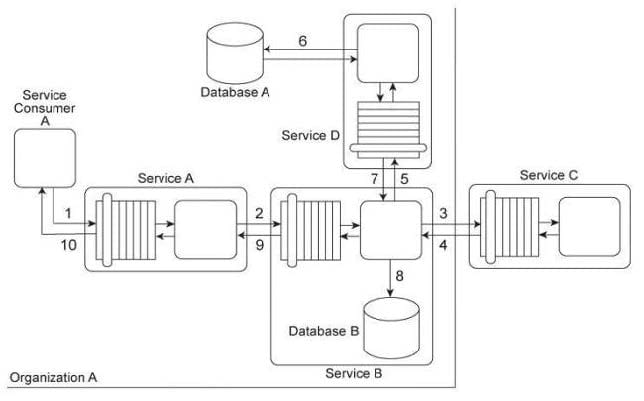
Recently, Service D received request messages containing improperly formatted database retrieval requests. All of these request messages contained data that originated from Service C. There is a strong suspicion that an attacker from outside of the organization has been attempting to carry out SOL injection attacks. Furthermore, it has been decided that each service that writes data to a database must keep a separate log file that records a timestamp of each database record change. Because of a data privacy disclosure requirement used by Organization A, the service contracts of these services need to indicate that this logging activity may occur. How can the service composition architecture be improved to avoid SQL injection attacks originating from Service C - and - how can the data privacy disclosure requirement be fulfilled?
A. Apply the Service Perimeter Guard pattern together with the Message Screening pattern in order to establish a perimeter service with message screening logic. Position the perimeter service between Service C and Service B. The message screening logic rejects or filters out potentially harmful content
in messages sent from Service C, prior to being forwarded to Service B. Secondly, update the service
contracts for Services B and D with an optional WS-Policy assertion that provides service consumers
with the option of complying to the logging requirements.
B. Apply the Data Origin Authentication pattern to authenticate data received from Service C. Service C digitally signs any datasent in response messages to Service B. Service B can then verify that the data has not been modified during transit and that it originated from Service C. Secondly, update the service contracts for Services B and D with an ignorable WS-Policy assertion that communicates the possibility of the logging activity.
C. Apply the Data Origin Authentication pattern to authenticate data received from Service C. Service C digitally signs any datasent in response messages to Service B. Service B can then verify that the data has not been modified during transit and that it originated from Service C. Secondly, update the service contracts for Services B and D with an ignorable WS-Policy assertion that communicates the possibility of the logging activity. The service contracts for Services B and D are updated with an optional WS- Policy assertion that provides service consumers with the option of complying to the logging requirements.
D. Apply the Message Screening pattern in order to establish a service agent with message screening logic. Position the service agent between Service C and Service B. The service agent's message screening logic can reject or filter out potentially harmful content in messages sent from Service C, before being processed by Service B. Secondly, update the service contracts for Services B and D with an ignorable WS-Policy assertion that communicates the possibility of the logging activity.
-
Question 26:
Service A has two specific service consumers, Service Consumer A and Service Consumer B (1). Both service consumers are required to provide security credentials in order for Service A to perform authentication using an identity store (2). If a service consumer's request message is successfully authenticated, Service A processes the request by exchanging messages with Service B (3) and then Service C (4). With each of these message exchanges, Service A collects data necessary to perform a query against historical data stored in a proprietary legacy system. Service A's request to the legacy system must be authenticated (5). The legacy system only provides access control using a single account. If the request from Service A is permitted, it will be able to access all of the data stored in the legacy system. If the request is not permitted, none of the data stored in the legacy system can be accessed. Upon successfully retrieving the requested data (6), Service A generates a response message that is sent back to either Service Consumer A or
A. The legacy system is also used independently by Service D without requiring any authentication. Furthermore, the legacy system has no auditing feature and therefore cannot record when data access from Service A or Service D occurs. If the legacy system encounters an error when processing a request, it generates descriptive error codes.
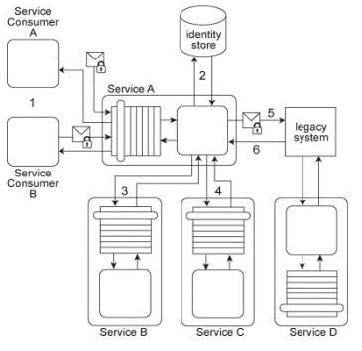
This service composition architecture needs to be upgraded in order to fulfill the following new security requirements: 1. Service Consumers A and B have different permission levels, and therefore, response messages sent to a service consumer must only contain data for which the service consumer is authorized. 2. All data access requests made to the legacy system must be logged. 3. Services B and C must be provided with the identity of Service A's service consumer in order to provide Service A with the requested data. 4. Response messages generated by Service A cannot contain confidential error information about the legacy system. Which of the following statements provides solutions that satisfy these requirements?
B. To correctly enforce access privileges, Services B and C must share the identity store with Service A and directly authenticate Service Consumer A or B. Furthermore, Services B and C must each maintain two policies: one for Service Consumer A and one for Service Consumer B. After receiving a request message from a Service A. Services B and C must evaluate the validity of the request by using the identity store and the appropriate policy. Service Consumers A and B are required to submit the necessary security credentials to the legacy system as part of the request message sent to Service A. After verifying the credentials, the legacy systemeitherperforms the necessary processing orsends the response to Service A or denies access and sends an error message directly to Service Consumer A or B. The Message Screening pattern is applied to Service A so that it can perform message screening logic in order to filter out unauthorized data coming from the legacy system.
C. Apply the Trusted Subsystem pattern by introducing a new utility service that encapsulates data access to the legacy system. After Service A authenticates a service consumer it creates a signed SAML assertion containing authentication and authorization information. The SAML assertions are used by Service A to convey the identity information of Service Consumer A or B to Services B and C. The utility service filters response messages to the service consumer based on the information in the SAML assertions. The utility service keeps a log of the all data access requests made to the legacy system. The Exception Shielding pattern is further applied to the utility service in order to prevent the leakage of confidential error information.
D. Apply the Service Perimeter Guard pattern to provide selective access privileges to Service Consumers A and B. The resulting perimeter service shares the identity store with Service A, which it uses to authenticate each request message. If authentication is successful, the request message is forwarded to Service A. Service A then also authenticates the service consumer and retrieves the service consumer's security profile from the identity store upon successful authentication. Each service consumer's security profile includes its authorized level of access. Service consumer authentication is subsequently performed using digital certificates. The Exception Shielding pattern is further applied to the perimeter service in order to prevent the leakage of confidential error information.
E. Apply the Trusted Subsystem pattern by introducing a new utility service that encapsulates data access to the legacy system. The utility service evaluates request messages by authenticating the service consumer against the identity store and also verifying the digital signature of each request. If the request is permitted, Service A forwards the service consumer's credentials to Services B and C, and to the legacy system.
The response messages from Services B and C are returned to Service A, while responses from the
legacy system are processed by the utility service. Logic is added to the utility service so that it can log
access requests made to the legacy system.
-
Question 27:
Service A provides a customized report generating capability. Due to infrastructure limitations, the number of service consumers permitted to access Service A concurrently is strictly controlled. Service A validates request messages based on the supplied credentials (1). If the authentication of the request message is successful, Service A sends a message to Service B (2) to retrieve the required data from Database A (3). Service A stores the response from Service B (4) in memory and then issues a request message to Service C (5). Service C retrieves a different set of data from Database A (6) and sends the result back to Service A (7). Service A consolidates the data received from Services B and C and sends the generated report in the response message to its service consumer (8).
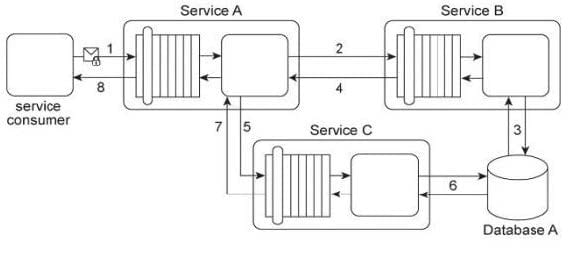
This service composition was recently shut down after it was discovered that Database A had been successfully attacked twice in a row. The first type of attack consisted of a series of coordinated request messages sent by the same malicious service consumer, with the intention of triggering a range of exception conditions within the database in order to generate various error messages. The second type of attack consisted of a service consumer sending request messages with malicious input with the intention of gaining control over the database server. This attack resulted in the deletion of database records and tables. An investigation revealed that both attacks were carried out by malicious service consumers that were authorized. How can the service composition security architecture be improved to prevent these types of attacks?
A. Apply the Data Confidentiality pattern together with the Data Origin Authentication pattern. This establishes message-levelsecurity so that all messages are encrypted and digitally signed. Secondly, the Service A logic must be enhanced so that it can keep track of the trustworthiness of its service consumers If a request message originated from a trustworthy service consumer, then the request message is processed as normal. If the request message originates from a non- trustworthy service consumer, then the request message is rejected and an error message is returned to the service consumer.
B. Apply the Service Perimeter Guard pattern together with the Trusted Subsystem pattern. This establishes a perimeter service between Database A and any service that requires access to it (including Services B and C). The perimeter service evaluates incoming data requests and filters out those that can introduce a security risk. Only request messages issued by authorized services and
service consumers are forwarded to Database
C. Responses originating from Database A are further evaluated by the trusted subsystem to remove any unauthorized data. The two patterns together ensure that only authorized data is returned to the service consumer and that no request messages present a security threat to Database A.
D. Apply the Exception Shielding pattern together with the Message Screening pattern. This establishes new logic within Service A that screens incoming request messages for data-driven attacks (such as SQL injection and XPath injection attacks), and also evaluates whether exception details returned by Database A contains potentially confidential or unsafe information. Any inappropriate exception information is replaced with sanitized content.
E. Apply the Trusted Subsystem pattern to protect Database A from data-driven attacks and to evaluate whether databaseresponses contain inappropriate data. The trusted subsystem maintains a snapshot of Database A and executes the original service consumer's request message against the snapshot. The processing logic that accesses the snapshot has limited privileges in order to prevent malicious attacks from overtaking the database. If no security violation is detected during the processing of the snapshot, then the original service consumer's request is forwarded to Database A. If an error message is generated during the processing of the snapshot, then it is returned to the original service consumer and the request is not forwarded to Database A.Because the error message was generated on the snapshot, it cannot contain unsafe information about Database A.
-
Question 28:
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message with security credentials to Service B (2). Service B authenticates the request and, if the authentication is successful, writes data from the request message into Database B (3). Service B then sends a request message to Service C (4), which is not required to issue a response message. Service B then sends a response message back to Service A (5). After processing Service B's response, Service A sends another request message with security credentials to Service B (6). After successfully authenticating this second request message from Service A, Service B sends a request message to Service D (7). Service D is also not required to issue a response message. Finally, Service B sends a response message to Service A (8), after which Service A records the response message contents in Database A (9) before sending its own response message to Service Consumer A (10).
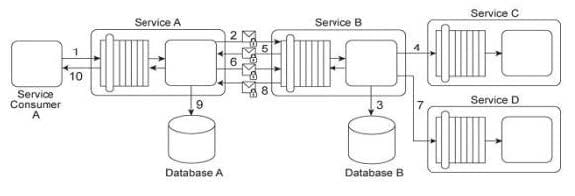
Services A and B use digital certificates to support message integrity and authentication. With every message exchange between the two services (2, 5, 6, 8), the digital certificates are used. It has been determined that both Databases A and B are vulnerable to malicious attackers that may try to directly access sensitive data records. Furthermore, performance logs have revealed that the current exchange of digital certificates between Services A and B is unacceptably slow. How can the integrity and authenticity of messages exchanged between Services A and B be maintained, but with improved runtime performance
-
and - how can Databases A and B be protected with minimal additional impact on performance?
A.
Apply the Brokered Authentication pattern to establish an authentication broker that uses WS- Trust based SAML tokens for message exchanges between Services A and B. This eliminates the need for Service A to be repeatedly authenticated by Service B. Use the public key of Service A to encrypt Database A and use the public key of Service B to encrypt Database B.
B.
Apply the Brokered Authentication pattern to establish an authentication broker that uses WS-SecureConversation securitycontext tokens (SCTs) to generate and transmit a symmetric session key. The session key is used to encrypt and digitally sign messages exchanged between Services A and B. For each database the Trusted Subsystem pattern is applied to require authenticated access to the database and to prevent attackers from accessing the database directly
C.
Apply the Direct Authentication pattern to establish mutual authentication between Services A and B
using a shared identity store. Service A attaches a Username token to the first request message sent to Service B and Service B authenticates the request message using the shared identity store. Similarly, when Service B submits a response message to Service A. it attaches its own Username token that Service A then authenticates by also using the same shared identitystore. Database A is encrypted using the Service A password as a secret encryption key and Database B is encrypted using the Service B password as a secret encryption key.
D. Apply the Brokered Authentication pattern to establish an authentication broker that uses WS- Trust based SAML tokens for message exchanges between Services A and B. This eliminates the need for Service A to be repeatedly authenticated by Service B. Database A is encrypted using the Service A password as a secret encryption key and Database B is encrypted using the Service B password as a secret encryption key.
-
Question 29:
Service A exchanges messages with Service B multiple times during the same runtime service activity. Communication between Services A and B has been secured using transport-layer security. With each service request message sent to Service B (1A. IB), Service A includes an X.509 certificate, signed by an external Certificate Authority (CA). Service B validates the certificate by retrieving the public key of the CA (2A. 2B) and verifying the digital signature of the X.509 certificate. Service B then performs a certificate revocation check against a separate external CA repository (3A, 3B). No intermediary service agents reside between Service A and Service B.
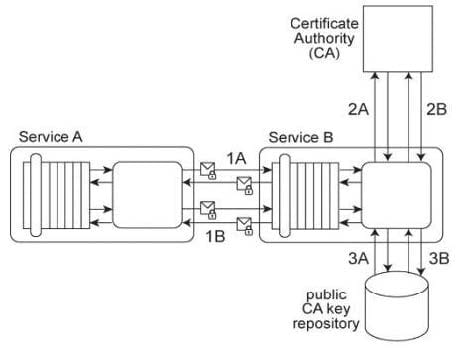
To fulfill a new security requirement, Service A needs to be able to verify that the response message sent by Service B has not been modified during transit. Secondly, the runtime performance between Services A and B has been unacceptably poor and therefore must be improved without losing the ability to verify Service A's security credentials. It has been determined that the latency is being caused by redundant security processing carried out by Service B. Which of the following statements describes a solution that fulfills these requirements?
A. Apply the Trusted Subsystem pattern to introduce a utility service that performs the security processing instead of Service B. The utility service can verify the security credentials of request messages from Service A and digitally sign messages sent to Service A to enable verification of message integrity. Furthermore, the utility service can perform the verification of security credentials submitted by Service A only once per runtime service activity. After the first messageexchange, it can issue a SAML token to Service A that gets stored within the current session. Service A can then use this session-based token with subsequent message exchange. Because SAML tokens have a very small validity period (in contrast to X.509 certificates), there is no need to perform a revocation check with every message exchange.
B. Service B needs to be redesigned so that it performs the verification of request messages from Service A only for the first message exchange during the runtime service activity. Thereafter, it can issue a SAML token to Service A that gets stored within the current session. Service A then uses this sessionbased token with subsequent message exchanges. Because SAML tokens have a very small validity
period (in contrast to X.509 certificates), there is no need to perform a
revocation check with every message exchange.
C. WS-SecurityPolicy transport binding assertions can be used to improve performance via transport-layer security The use of symmetric keys can keep the encryption and decryption overhead to a minimum, which will further reduce the latency between Service A and Service B. By encrypting the messages, attackers cannot modify message contents, so no additional actions for integrity verification are needed.
D. The Data Origin Authentication pattern can be applied together with the Service Perimeter Guard pattern to establish a perimeter service that can verify incoming request messages sent to Service B and to filter response messages sent to Service A. The repository containing the verification information about the Certificate Authorities can be replicated in the trust domain of the perimeter service. When access is requested by Service A, the perimeter service evaluates submitted security credentials by checking them against the locally replicated repository. Furthermore, it can encrypt messages sent to Service A by Service B. and attach a signed hash value.
-
Question 30:
Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial data from Database A (2). Service A then sends a request message with the retrieved data to Service B (3). Service B exchanges messages with Service C (4) and Service D (5), which perform a series of calculations on the data and return the results to Service A. Service A uses these results to update Database A (7) and finally sends a response message to Service Consumer A (8). Component B has direct, independent access to Database A and is fully trusted by Database A. Both Component B and Database A reside within Organization A. Service Consumer A and Services A, B, C, and D are external to the organizational boundary of Organization A.
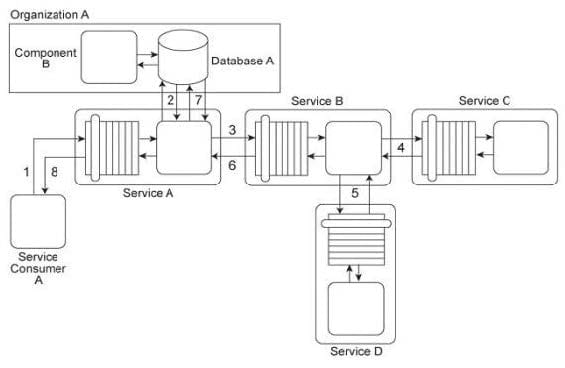
Component B is considered a mission critical program that requires guaranteed access to and fast response from Database A. Service A was recently the victim of a denial of service attack, which resulted in Database A becoming unavailable for extended periods of time (which further compromised Component B). Additionally, Services B, C, and D have repeatedly been victims of malicious intermediary attacks, which have further destabilized the performance of Service A. How can this architecture be improved to prevent these attacks?
A. A utility service is created to encapsulate Database A and to assume responsibility for authenticating all access to the database by Service A and any other service consumers. Due to the mission critical requirements of Component B, the utility service further contains logic that strictly limits the amount of concurrent requests made to Database A from outside the organizational boundary. The Data Confidentiality and Data Origin Authentication patterns are applied to all message exchanged within the external service composition in order to establish message-layer security.
B. Service Consumer A generates a private/public key pair and sends this public key and identity information to Service A. Service A generates its own private/public key pair and sends it back to Service Consumer A. Service Consumer A uses the public key of Service A to encrypt a randomly generated session key and then sign the encrypted session key with the private key. The encrypted, signed session key is sent to Service A. Now, this session key can be used for secure message-layer communication between Service Consumer A and Service A. The Service Perimeter Guard pattern is applied to establish a perimeter service that encapsulates Database A in order to authenticate all external access requests.
C. Services B, C, and D randomly generate Session Key K, and use this key to encrypt request and response messages with symmetric encryption. Session Key K is further encrypted itself asymmetrically. When each service acts as a service consumer by invoking another service, it decrypts the encrypted Session Key K and the invoked service uses the key to decrypt the encrypted response.
Database A is replicated so that only the replicated version of the database can be accessed by
Service A and other external service consumers.
D. The Direct Authentication pattern is applied so that when Service Consumer A submits security credentials, Service A will be able to evaluate the credentials in order to authenticate the request message. If the request message is permitted, Service A invokes the other services and accesses Database A. Database A is replicated so that only the replicated version of the database can be accessed by Service A and other external service consumers.
Related Exams:
S90-01A
Fundamental SOA & Service-Oriented Computing (S90-01A)S90-02A
SOA Technology Concepts (S90-02A)S90-03A
SOA Design & Architecture (S90-03A)S90-08A
Advanced SOA Design & Architecture (S90-08A)S90-09A
SOA Design & Architecture Lab (S90-09A)S90.08B
SOA Design & Architecture Lab with Services & Microservices
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only SOA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your S90-20A exam preparations and SOA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.