Exam Details
Exam Code
:S90-20AExam Name
:SOA Security LabCertification
:SOA CertificationsVendor
:SOATotal Questions
:30 Q&AsLast Updated
:Jun 23, 2025
SOA SOA Certifications S90-20A Questions & Answers
-
Question 11:
Service A is a publically accessible service that provides free multimedia retrieval capabilities to a range of service consumers. To carry out this functionality, Service A is first invoked by Service Consumer A (1). Based on the nature of the request message received from Service Consumer A, Service A either invokes Service B or Service C. When Service B is invoked by Service A (2A) it retrieves data from publicly available sources (not shown) and responds with the requested data (3A). When Service C is invoked by Service A (2B) it retrieves data from proprietary sources within the IT enterprise (not shown) and responds with the requested data (3B). After receiving a response from Service B or Service C, Service A sends the retrieved data to Service Consumer A (4). Service B does not require service consumers to be authenticated, but Service C does require authentication of service consumers. The service contract for Service A therefore uses WS-Policy alternative policies in order to express the two different authentication requirements to Service Consumer A. When Service Consumer A sends a request message (1), Service A determines whether the request requires the involvement of Service C and then checks to ensure that the necessary security credentials were received as part of the message. If the credentials provided by Service Consumer A are verified. Service A creates a signed SAML assertion and sends it with the request message to Service C (2B) This authentication information is protected by public key encryption However, responses to Service Consumer A's request message (3B, 4) are not encrypted for performance reasons.
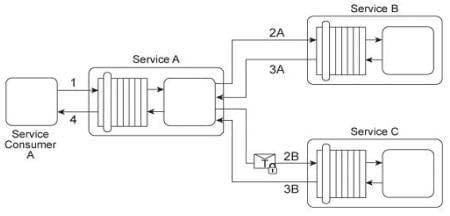
Recently, the usage of Service C has noticeably declined. An investigation has revealed response messages issued by Service C (3B) have been repeatedly intercepted and accessed by unauthorized and malicious intermediaries. As a result, Service Consumer A has lost confidence in the use of Service A for the retrieval of proprietary data because it is being viewed as a security risk. This is especially troubling, because the owner of Service A had planned to start charging a fee for Service A's ability to provide proprietary data via the use of Service C. How can this service composition architecture be changed to address the security problem with minimal impact on runtime performance?
A. Use the existing PKI to provide message-layer security for the response messages originating from Service C. To providemessage confidentiality, Service C can encrypt the response messages using Service Consumer A's public key. This prevents unauthorized intermediaries from accessing the content of response messages.
B. Use the existing PKI to provide two-way authentication of the exchanged messages. After receiving a request from the service consumer, Service A can respond with a signed acknowledgement of the message, encrypted by the public key of Service Consumer A. Only Service Consumer A will be able to decrypt the encrypted acknowledgement. Service Consumer A then responds to the acknowledgement, thereby verifying its identity with Service
A. Because both Service Consumer A and Service A are mutually authenticated, end-to-end transport-layer security is sufficient to provide message confidentiality in order to prevent unauthorized intermediaries from accessing messages originating from Service C.
C. Use the existing PKI to establish secure communication between Service Consumer A and Service C. A symmetric key can be generated for the data being sent from Service C to Service Consumer A Service C can generate a session key that is encrypted with Service Consumer A's public key. Service C can then attach the session key to the response message, which is encrypted using the session key. Because only Service Consumer A can decrypt the encrypted session key, the data transmitted in the message is safe from access by unauthorized intermediaries.
D. Use the existing PKI to specify encryption and digital signature requirements on the messages. Service C can use ServiceConsumer A's public key to generate a symmetric key. Service Consumer A can also generate the same session key from its own public key. Service C can use the session key to encrypt the response message (and the hash value of the response message), concatenate them, and send them to Service Consumer A. Service Consumer A separates the concatenated and encrypted hash value, decrypts it, and then decrypts the encrypted response message. As a result, the confidentiality and integrity of the response message are guaranteed.
-
Question 12:
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement message (2) and then processes the request and sends a request message to Service B (3). This message contains confidential financial data. Service B sends three different request messages together with its security credentials to Services C, D, and E (4, 5, 6). Upon successful authentication, Services C, D, and E store the data from the message in separate databases (7, 8, 9) Services B, C, D, and E belong to Service Inventory A, which further belongs to Organization B. Service Consumer A and Service A belong to Organization A.

The service contracts of Services A and B both comply with the same XML schema. However, each organization employs different security technologies for their service architectures. To protect the confidential financial data sent by Service A to Service B, each organization decides to independently apply the Data Confidentiality and the Data Origin Authentication patterns to establish message-layer security for external message exchanges. However, when an encrypted and digitally signed test message is sent by Service A to Service B, Service B was unable to decrypt the message. Which of the following statements describes a solution that solves this problem?
A. Although both of the organizations applied the Data Confidentiality and the Data Origin Authentication patterns, the securitytechnologies used for the Service A and Service B architectures may be incompatible. Because there are several technologies and versions of technologies that can be used to apply these patterns, the organizations need to standardize implementation level details of the relevant security technologies.
B. The problem with the test message occurred because Service A used incorrect keys to protect the message sent to Service B. Service A used its own public key to sign the message and then used Service B's public key to encrypt the message content. To correct the problem, Service A must use WS-SecureConversation to agree on a secret session key to be used to encrypt messages exchanged between Services A and B. Because this session key is only known by Services A and B, encrypting the messages with this key also provides authentication of the origin of the data.
C. Although both of the organizations successfully applied the Data Confidentiality and the Data Origin Authentication patterns, the order in which the patterns were applied is incorrect. The application of the Data Origin Authentication pattern must always follow the application of the Data Confidentiality pattern to ensure that the message confidentiality from a third party authenticates the origin of the message.
D. The problem with the test message occurred because Service A needed the private key of Service B to digitally sign themessage. An attacker pretending to be Service B likely sent a fake private/public keys pair to Service A. Using these fake keys to encrypt and digitally sign the message made the message incompatible for Service B. Because the fake private key was also used to sign the hash, it explains the source of the problem.
-
Question 13:
Services A, B and C belong to Service Inventory A. Services D, E and F belong to Service Inventory B. Service C acts as an authentication broker for Service Inventory A. Service F acts as an authentication broker for Service Inventory B. Both of the authentication brokers use Kerberos- based authentication technologies. Upon receiving a request message from a service consumer, Services C and F authenticate the request using a local identity store and then use a separate Ticket Granting Service (not shown) to issue the Kerberos ticket to the service consumer.
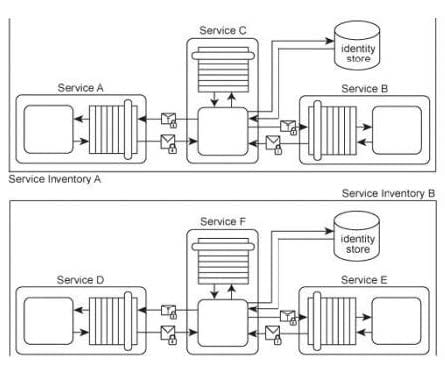
Currently, tickets issued in one service inventory are not valid in the other. For example, if Service A wants to communicate with Services D or E, it must request a ticket from the Service Inventory B authentication broker (Service F). Because Service Inventory A and B trust each other, the current cross-inventory authentication is considered unnecessarily redundant. How can these service inventory architectures be improved to avoid redundant authentication?
A. Create a single, enterprise-wide service inventory by merging Service Inventories A and B. Instead of the current Kerberos-based brokered authentication, the merged service inventory can use X.509 digital certificates to remove the burden from the local authentication brokers. Designate either Service C or Service F as the central authentication service with the responsibility to validate service consumer X.509 digital certificates. After successful validation, the authentication service can issue a signed SAML token to be used within the entire service inventory.
B. The same Kerberos tickets can be used across both service inventories by updating the security policies of the services that require Kerberos tickets. Because each authentication broker issues Kerberos tickets, the only difference between these tickets is the identity of the issuer. Forexample, because services in Service Inventory A already accept Kerberos tickets issued by Service C, Service F just needs to be included in the security policies of these services. Similarly, services in Service Inventory B that accept Kerberos tickets issued by Service F need to include the acceptance of Kerberos tickets issued by Service C in their security policies.
C. A trust relationship needs to be established between the two authentication brokers. This trust relationship can enable the authentication brokers to accept Kerberos tickets issued by each other.
D. Replace Services C and F with a single authentication broker so that one single token can be used with services across both service inventories. This can be achieved by merging the content of the two identity stores.
-
Question 14:
Service A provides a data retrieval capability that can be used by a range of service consumers, including
Service Consumer A, In order to retrieve the necessary data. Service Consumer A first sends a request
message to Service A (1). Service A then exchanges request and response messages with Service B (2,
3). Service C (4, 5), and Service D (6.
7). After receiving all three response messages from Services B. C. and D, Service A assembles the
collected data into a response message that it returns to Service Consumer A (8).

The Service A data retrieval capability has been suffering from poor performance, which has reduced its usefulness to Service Consumer A. Upon studying the service composition architecture, it is determined that the performance problem can be partially attributed to redundant validation by service contracts for compliance to security policies. Services B and C have service contracts that contain the same two security policies. And, Service D has a service contract that contains a security policy that is also part of Service A's service contract. What changes can be made to the service contracts in order to improve the performance of the service composition while preserving the security policy compliance requirements?
A. Apply the Policy Centralization pattern in order to establish a single security policy for the entire service composition. Theredundant policies residing in the service contracts of Services A. B, C and D need to be removed and grouped together into one master policy definition enforced by Service A. This way, redundant policy validation is eliminated, thereby improving runtime performance.
B. Apply the Policy Centralization pattern in order to establish two centralized policy definitions and ensure that policy enforcement logic is correspondingly centralized. The first policy definition includes the redundant security policies from Services A and D and the second policy definition contains the redundant security policies from Services B and
C.
D. All policies are analyzed for similarities, which are then extracted and, by applying the Policy Centralization pattern, combined into a single policy definition. This "meta-policy" is then positioned to perform validation of the response message generated by Service A, prior to receipt by Service Consumer A. If validation fails, an alternative error message is sent to Service Consumer A instead.
E. Apply the Standardized Service Contract principle in order to remove redundancy within service contracts by ensuring that all four service contracts comply with the same policy standards. This further requires the application of the Service Abstraction principle to guarantee that policy definitions are sufficiently streamlined for performance reasons.
-
Question 15:
Service Consumer A sends a request message with a Username token to Service A (1). Service B authenticates the request by verifying the security credentials from the Username token with a shared identity store (2), To process Service Consumer A's request message. Service A must use Services B, C, and D. Each of these three services also requires the Username token (3. 6, 9) in order to authenticate Service Consumer A by using the same shared identity store (4, 7, 10). Upon each successful authentication, each of the three services (B, C, and D) issues a response message back to Service A (5, 8, 11). Upon receiving and processing the data in all three response messages, Service A sends its own response message to Service Consumer A (12).

There are plans implement a single sign-on security mechanism in this service composition architecture. The service contracts for Services A, C, and D can be modified with minimal impact in order to provide support for the additional messaging requirements of the single sign-on mechanism. However, Service B's service contract is tightly coupled to its implementation and, as a result, this type of change to its service contract is not possible as it would require too many modifications to the underlying service implementation. Given the fact that Service B's service contract cannot be changed to support single sign-on, how can a single sign-on mechanism still be implemented across all services?
A. Apply the Brokered Authentication pattern so that Service A acts as an authentication broker that issues a SAML token on behalf of Service Consumer A, and forwards this token to Services C and D. Create a new utility service is positioned between Service A and Service
B. This utility service perform a conversion of the SAML token to a Username token, and then forwards the Username token to Service B so that Service B can still perform authentication of incoming requests using its own security mechanism.
C. Apply the Brokered Authentication pattern to establish Service A as an authentication broker that issues a SAML token for Service Consumer A and forwards Service Consumer A's token to other services. Apply the Trusted Subsystem pattern to create a utility service that acts as a trusted subsystem for Service B. This utility service is able to perform authentication using the SAML token from Service A and can then generate a Username token by embedding its own credentials when accessing Service B. This way, Service B can perform authentication of requestmessages as it does now, but it can still participate in the single sign-on message exchanges without requiring changes to its service contract.
D. Apply the Brokered Authentication pattern so that Service A acts as an authentication broker that issues a SAML token for Service Consumer A and forwards Service Consumer A's token to Services C and D. Create a second service contract for Service B that supports single sign-on. This way, Service B can still perform authentication of incoming requests using the old service contract while allowing for the processing of SAML tokens using the new service contract.
E. Replace the Username tokens with X.509 digital certificates. This allows for the single sign-on mechanism to be implemented without requiring changes to any of the service contracts.
-
Question 16:
Services A, B, and C reside in Service Inventory A and Services D, E, and F reside in Service Inventory B. Service B is an authentication broker that issues WS-Trust based SAML tokens to Services A and C upon receiving security credentials from Services A and C. Service E is an authentication broker that issues WS-Trust based SAML tokens to Services D and F upon receiving security credentials from Services D and E. Service B uses the Service Inventory A identify store to validate the security credentials of Services A and
C. Service E uses the Service Inventory B identity store to validate the security credentials of Services D and F.
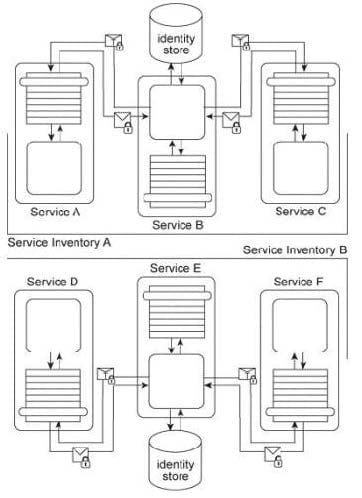
To date, the two service inventories have existed independently from each other. However, a requirement has emerged that the services in Service Inventory A need to be able to use the services in Service Inventory B, and vice versa. How can cross-service inventory message exchanges be enabled with minimal changes to the existing service inventory architectures and without introducing new security mechanisms?
A. Because SAML tokens cannot be used across multiple security domains, authentication brokers C and E need to be replaced with one single authentication broker so that one token issuer is used for all services across both of the service inventories.
B. The current security mechanism already fulfills the requirement because SAML tokens can be used across multiple securitydomains. The only change required is for each authentication broker to be configured so that it issues service inventory-specific assertions for SAML tokens originating from other service inventories.
C. The individual domain service inventories need to be combined into one enterprise service inventory. The Service Perimeter Guard pattern can be applied to establish a contact point for request messages originating from outside the service inventory. Within the service inventory, services no longer need to be authenticated because they are all part of the same trust boundary.
D. The Trusted Subsystem pattern is applied to encapsulate Services B and E using a central utility service that balances request and response messages exchanged between Services B and E, depending on which service inventory the messages originate from. The utility service also contains transformation logic to ensure that the SAML tokens issued by Services B and E are compatible. This guarantees that an issued SAML token can be used across Service Inventories A and B without further need for runtime conversion.
-
Question 17:
Services A, B and C belong to Service Inventory A. Services D, E and F belong to Service Inventory B. Service C acts as an authentication broker for Service Inventory A. Service F acts as an authentication broker for Service Inventory B. Both of the authentication brokers use Kerberos- based authentication technologies. Upon receiving a request message from a service consumer, Services C and F authenticate the request using a local identity store and then use a separate Ticket Granting Service (not shown) to issue the Kerberos ticket to the service consumer.
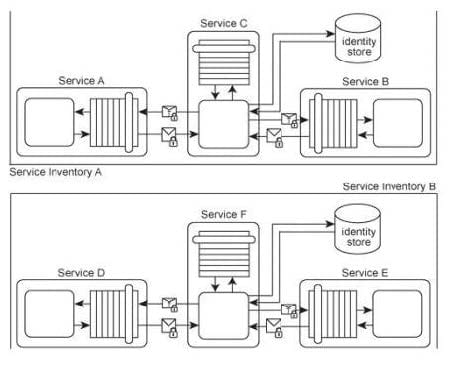
A recent security audit of the two service inventories revealed that both authentication brokers have been victims of attacks. In Service Inventory A, the attacker has been intercepting and modifying the credential information sent by Service C (the ticket requester) to the Ticket Granting Service. As a result, the requests have been invalidated and incorrectly rejected by the Ticket Granting Service. In Service Inventory B, the attacker has been obtaining service consumer credentials and has used them to request and receive valid tickets from the Ticket Granting Service. The attacker has then used these tickets to enable malicious service consumers to gain access to other services within the service inventory. How can the two service inventory security architectures be improved in order to counter these attacks?
A. The Data Confidentiality pattern can be applied to messages exchanged by the services in Service Inventory A. The Data Origin Authentication pattern can be applied to messages exchanged by services in Service Inventory B.
B. The Service Perimeter Guard pattern can be applied to Service Inventory A in order to establish a perimeter service responsible for validating and filtering all incoming request messages on behalf of Service C. The Data Origin Authentication pattern can be applied to messages exchanged by services in Service Inventory B. This will ensure the integrity of messages by verifying their origins to the message recipients.
C. WS-SecureConversation can be used to secure the communication between the authentication broker and service consumers in Service Inventory A. This ensures that Services A and B will contact Service C to request a security context token that will be used to generates a session key for the encryption of the ticket submitted to Service C.The Data Origin Authentication pattern can be applied to messages exchanged by services in Service Inventory B. This will ensure the integrity of messages try verifying their origins to the message recipients.
D. WS-Trust can be used to establish secure communication between the authentication broker and the service consumers. After receiving the request message and the corresponding credentials from service consumers, the authentication broker can validate their identity, and if successful, a signed SAML assertion containing all authentication information will be issued. The SAML assertion will then be used to authenticate the service consumers during subsequent communications. Because the messages are signed and encrypted, malicious service consumers cannot access the data. This approach can be applied to counter the threats in both Service Inventories A and B.
-
Question 18:
Service Consumer A sends a request message with an authentication token to Service A, but before the message reaches Service A, it is intercepted by Service Agent A (1). Service Agent A validates the security credentials and also validates whether the message is compliant with Security Policy A. If either validation fails, Service Agent A rejects the request message and writes an error log to Database A (2A). If both validations succeed, the request message is sent to Service A (2B). Service A retrieves additional data from a legacy system (3) and then submits a request message to Service B Before arriving at Service B, the request message is intercepted by Service Agent B (4) which validates its compliance with Security Policy SIB then Service Agent C (5) which validates its compliance with Security Policy B. If either of these validations fails, an error message is sent back to Service A. that then forwards it to Service Agent A so that it the error can be logged in Database A (2A). If both validations succeed, the request message is sent to Service B (6). Service B subsequently stores the data from the message in Database B (7). Service A and Service Agent A reside in Service Inventory A. Service B and Service Agents B and C reside in Service Inventory B. Security Policy SIB is used by all services that reside in Service Inventory B. Service B can also be invoked by other service consumers from Service Inventory B. Request messages sent by these service consumers must also be compliant with Security Policies SIB and B.
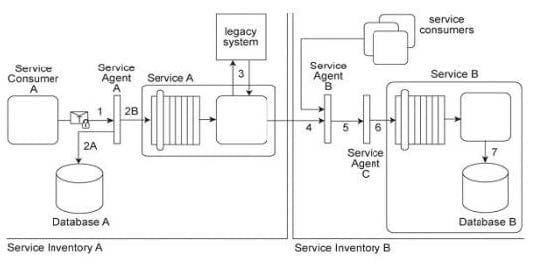
Access to the legacy system in Service Inventory A is currently only possible via Service A, which means messages must be validated for compliance with Security Policy A. A new requirement has emerged to allow services from Service Inventory B to access the legacy system via a new perimeter service that will be dedicated to processing request messages from services residing in Service Inventory B. Because the legacy system has no security features, all security processing will need to be carried out by the perimeter service. However, there are parts of Security Policy A that are specific to Service A and do not apply to the legacy system or the perimeter service. Furthermore, response messages sent by the perimeter service to services from Service Inventory B will still need to be validated for compliance to Security Policy B and Security Policy SIB. How can the Policy Centralization pattern be correctly applied without compromising the policy compliance requirements of services in both service inventories?
A. In order for Security Policy A to be centralized so that it can be shared by Service A and the new perimeter service, messages sent to the perimeter service from services in Service Inventory B will need to continue complying with Security Policy A, even if it requires that the messages contain content that does not relate to accessing the legacy system. In order to centralize SecurityPolicy B it will need to be combined with Security Policy SIB, which means that the functionality within Service Agents B and C can be combined into a single service agent.
B. A single centralized security policy can be created by combining Security Policy A, Security Policy B. and Security Policy SIB into a single security policy that is shared by services in both Service Inventory A and Service Inventory B. This means that the new perimeter service can share the same new security policy with Service A. This further simplifies message exchange processing because request messages sent by services in Service Inventory B to the new perimeter service need to comply to the same security policy as the response messages sent back by the perimeter service to the services in Service Inventory B.
C. The parts of Security Policy A that are required for access to the new perimeter service need to be removed and placed into a new security policy that is shared by Service A and the perimeter service. Messages sent by services accessing the perimeter service from Service Inventory B will need to be compliant with the new security policy. Because the perimeter service is dedicated to message exchange with services from Service Inventory B, response messages sent by the perimeter service can be designed for compliance to Security Policy B and Security Policy SIB.
D. Due to the amount of overlap among Security Policy A, Security Policy B, and Security Policy SIB, the Policy Centralization pattern cannot be correctly applied to enable the described message exchange between the perimeter service in Service Inventory A and services in Service Inventory B.
-
Question 19:
Service Consumer A sends a request message with a Username token to Service A (1). Service B authenticates the request by verifying the security credentials from the Username token with a shared identity store (2). To process Service Consumer A's request message, Service A must use Services B, C, and D. Each of these three services also requires the Username token (3. 6, 9) in order to authenticate Service Consumer A by using the same shared identity store (4, 7, 10). Upon each successful authentication, each of the three services (B, C, and D) issues a response message back to Service A (5, 8, 11). Upon receiving and processing the data in all three response messages, Service A sends its own response message to Service Consumer A (12).
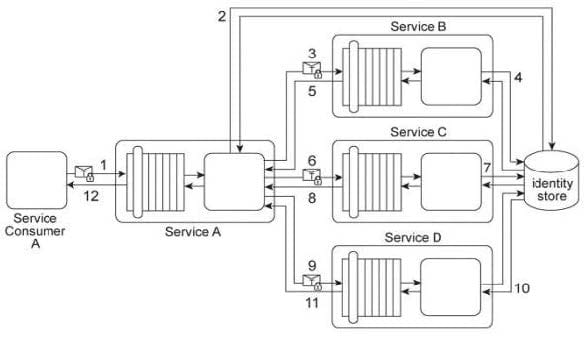
You are asked to redesign this service composition architecture so that it can still carry out the described message exchanges while requiring that Service Consumer A only be authenticated once using the identity store. Which of the following statements describes an accurate solution?
A. A single sign-on mechanism is implemented. The Brokered Authentication pattern is applied, resulting in Service A becoming the authentication broker. The authentication broker authenticates the security credentials received from Service Consumer A against the identity store. After successful authentication, the authentication broker issues a signed SAML token for Service Consumer A. The SAML token is subsequently provided to Services B.C. and D by Service A, on behalf of Service Consumer A.
B. A single sign-on mechanism is implemented. The Brokered Authentication pattern is applied together with the Data OriginAuthentication pattern. A separate authentication broker utility service is added in between Service Consumer A and Service A. This requires that Service A send its Username token only once to Service B. Service B then acts as a secondary authentication broker and authenticates Service Consumer A and Service A using the identity store. If the authentication is successful,Service B generates a shared secret key to be used as a session key during communication with Services C and
C. Because the session key is only known by these services, it can be used authenticates the services to each other.
D. A single sign-on mechanism is implemented. The Brokered Authentication pattern is applied together with the Data Origin Authentication pattern. Service A is redesigned to use holder-of-key based subject
confirmation SAML assertions. This way, Service A only needs to send its Username token once to
Service B. Service B then acts as the authentication broker by issuing a SAML token to Service A and
then further sends the SAML token to Services C and D on behalf of Service Consumer A and Service
A.
Service B signs the SAML assertion in order to ensure its authenticity and integrity during message
exchanges with Services C and D.
E. The Direct Authentication pattern is applied together with an authentication process that uses digital certificates and digital signatures instead of Username tokens. The digital certificate of Service Consumer A is attached to all subsequent request messages issued by Services A, B, C and D and these request messages are further signed by a private key.
-
Question 20:
Service A is a publically accessible service that provides free multimedia retrieval capabilities to a range of service consumers. To carry out this functionality, Service A is first invoked by Service Consumer A (1). Based on the nature of the request message received from Service Consumer A, Service A either invokes Service B or Service C. When Service B is invoked by Service A (2A) it retrieves data from publicly available sources (not shown) and responds with the requested data (3A). When Service C is invoked by Service A (2B) it retrieves data from proprietary sources within the IT enterprise (not shown) and responds with the requested data (3B). After receiving a response from Service B or Service C, Service A sends the retrieved data to Service Consumer A (4). Service B does not require service consumers to be authenticated, but Service C does require authentication of service consumers. The service contract for Service A therefore uses WS-Policy alternative policies in order to express the two different authentication requirements to Service Consumer
A. When Service Consumer A sends a request message (1), Service A determines whether the request requires the involvement of Service C and then checks to ensure that the necessary security credentials were received as part of the message. If the credentials provided by Service Consumer A are verified. Service A creates a signed SAML assertion and sends it with the request message to Service C (2B) This authentication information is protected by public key encryption However, responses to Service Consumer A's request message (3B, 4) are not encrypted for performance reasons.
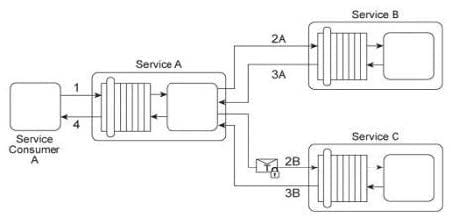
The owner of Service C is planning two changes to the service architecture: 1. A fee will be charged to Service Consumer A (or any service consumer) using Service C. 2. The response messages issued by Service C need to be secured in order to prevent unauthorized access. An analysis of Service C's usage statistics reveals that a group of service consumers specifically request the retrieval of multimedia data on a frequent basis. To promote the usage of Service C to these types of service consumers, the owner of Service C plans to offer a special discount by allowing unlimited multimedia retrievals for a fixed monthly price. Service consumers that do not subscribe to this promotion will need to pay for each request individually. It is anticipated that the new promotion will significantly increase the usage of Service C. The owner of Service C therefore wants to ensure that the security added to the response messages has a minimal impact on Service C's runtime performance. What steps can be taken to fulfill these requirements?
A. Use symmetric session keys so that for each response message, Service C generates a session key and encrypts theresponse message using this session key. The session key is then encrypted (using the service consumer's public key) and attached to the encrypted response. A single session key can then be used by Service C for communication with all service consumers that subscribe to the promotion.
B. Because the services in this service composition already rely on public key encryption to provide authentication, Service C can provide message confidentiality by encrypting the response message with Service Consumer A's public key. This will ensure that only the intended recipient, in possession of the corresponding private key, can decrypt the response message. To further reduce the performance impact of encryption, Service C can generate a new public-private key pair to be used by service consumers subscribed to the promotion. By securely distributing the private key to each of these service consumers, Service C only needs to encrypt the response messages once with the public key.
C. Design Service C to generate a message digest of the response message and encrypt it with the service consumer's publickey. Because the message digest is typically small, the performance of public key encryption is acceptable. This approach also ensures that only the service consumer can decrypt the response message using the corresponding private key.
D. Design the service composition architecture so that the encryption of the response messages is performed by Service B and Service C. To reduce the performance impact, a policy can be added to Service A's service contract in order to require the encryption of all response messages, regardless of the type of service consumer making the request. Further, a new utility service can be added to the service composition. This service can be responsible for obtaining the public key of the service consumer and forwarding the key along with the request message to the appropriate service (Service B or Service C). The service receiving the message can
then encrypt the response message with the received public key. Service A can then forward the
encrypted response to the service consumer.
This approach ensures that only authorized service consumers will be able to access response
messages.
Related Exams:
S90-01A
Fundamental SOA & Service-Oriented Computing (S90-01A)S90-02A
SOA Technology Concepts (S90-02A)S90-03A
SOA Design & Architecture (S90-03A)S90-08A
Advanced SOA Design & Architecture (S90-08A)S90-09A
SOA Design & Architecture Lab (S90-09A)S90.08B
SOA Design & Architecture Lab with Services & Microservices
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only SOA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your S90-20A exam preparations and SOA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.