Exam Details
Exam Code
:S10-210Exam Name
:SNIA Storage Networking Management and AdministrationCertification
:SNIA CertificationsVendor
:SNIATotal Questions
:97 Q&AsLast Updated
:Jul 13, 2025
SNIA SNIA Certifications S10-210 Questions & Answers
-
Question 51:
A server with a dual-ported HBA loses access to storage during switch SFP replacement. You want to prevent this from happening in the future.
Which action should you perform?
A. Use zoning
B. Enable trunking.
C. Use LUN masking
D. Configure multipathing
-
Question 52:
A security audit reveals deficiencies in your company's FC zoning practices. Your manager asks you to make a recommendation to implement the most secure FC zoning possible. Your company is using switches from a single vendor.
What do you recommend?
A. All zones should use frame-based hardware enforcement using pWWN identification exclusively for all configurations.
B. All zones should use software-based enforcement using pWWN identification exclusively for all configurations.
C. All zones should use frame-based hardware enforcement using destination port identification exclusively for all configurations.
D. All zones should use software-based enforcement using destination port identification exclusively for all configurations.
-
Question 53:
Which protocol commonly uses CNA devices?
A. FCIP
B. iFCP
C. FCoE
D. FCR
-
Question 54:
Click the Exhibit button.
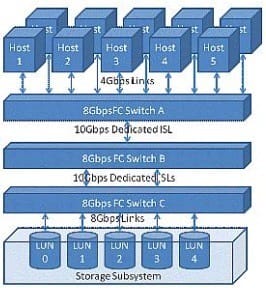
The customer application requires a 50/50 R/W ratio with 100 MBps throughput requirements for each
direction of the link. The application servers will simultaneously sustain these data rates across all LUNs in parallel.
Referring to the exhibit, where will the oversubscribed link(s) occur?
A. Links between hosts and Switch A
B. Inter-switch link between Switch A and Switch B
C. Inter-switch link between Switch B and Switch C
D. Links between Switch C and storage
-
Question 55:
You have been asked to create a LUN on a storage array that is comprised of 7,200 rpm SATA drives. Each drive is rated at 100 IOPS. The LUN should provide a minimum of 1100 IOPS and withstand multiple drive failures using the least number of drives.
How many drives and which RAID level should you use to create this LUN?
A. 11 drives and RAID 0
B. 12 drives and RAID 5
C. 13 drives and RAID 6
D. 22 drives and RAID 1
-
Question 56:
You receive a ticket from a database group which is complaining about slow access to storage on only one particular server, as compared to other servers in an active-active cluster. You verify zoning and LUN masking which are fine. On the FC switch, you verify link speed, errors, and throughput for the FC switch ports used by this server. There are no errors on the ports and the link speed is the same as on the switch ports used by other servers in the cluster. You notice that on one port on the FC switch used by this server, that there is no throughput at all. What is causing the problem?
A. The switch has obsolete firmware.
B. There are too many ports used on the FC switch.
C. Multipathing was not configured for load-balancing.
D. The switch is over-subscribed.
-
Question 57:
Click the Exhibit button.
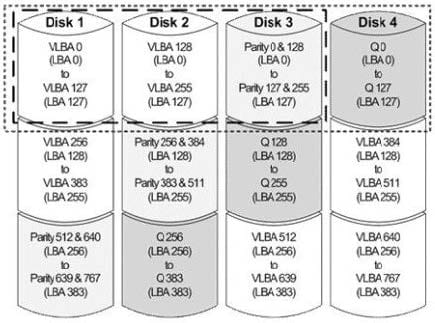
Which RAID level is shown in the exhibit?
A. RAID 4
B. RAID 5
C. RAID 0
D. RAID 6
-
Question 58:
Click the Exhibit button.
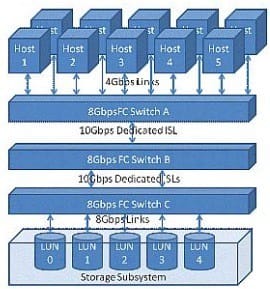
The customer configuration shown in the exhibit is not meeting the throughput needs of a newly installed application. The application's I/O profile consists of 100% 4 kilobyte reads and all servers require a sustained bandwidth of 150 MBps.
Which location within the configuration presents a performance bottleneck?
A. Links between hosts and Switch A
B. Inter-switch link between Switch A and Switch B
C. Inter-switch link between Switch B and Switch C
D. Links between Switch C and storage subsystem
-
Question 59:
Your company uses a cryptographic key system to encrypt tapes. After several years of use and thousands of tapes shipped to off-site locations, an IT audit reveals that encryption keys have been inadvertently stored as ciphertext on file shares to which everyone in the company has read permissions. Which response reflects industry best practice?
A. All data encrypted with the keys exposed as ciphertext should be considered safe.
B. All data encrypted with the keys exposed as ciphertext and not yet sent off-site as an encrypted tape should be re-keyed (decrypted and re-encrypted using a new key).
C. All data encrypted with the keys exposed as ciphertext should be re-keyed (decrypted and re-encrypted using a new key).
D. All data encrypted with the keys exposed as ciphertext should be considered safe as ciphertext is very difficult to use.
-
Question 60:
Some business critical database applications have been suffering from slowly increasing performance issues with one enterprise SAN-attached storage system. In particular, the applications are showing higher than normal read response times.
What should the storage administrator monitor to determine the root cause?
A. Storage utilization
B. Available free space
C. Write response time
D. Cache hit rate
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only SNIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your S10-210 exam preparations and SNIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.