Exam Details
Exam Code
:JN0-332Exam Name
:Juniper Networks Certified Internet Specialist, SEC (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:519 Q&AsLast Updated
:Jun 06, 2025
Juniper Juniper Certifications JN0-332 Questions & Answers
-
Question 421:
Click the Exhibit button.
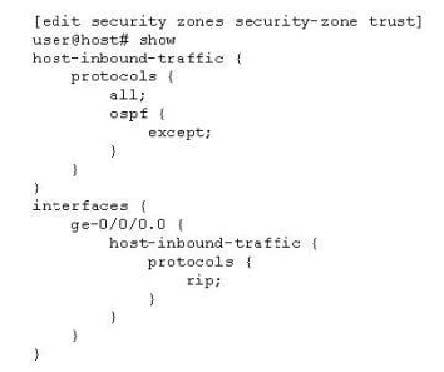
Given the configuration shown in the exhibit, which protocol(s) are allowed to communicate with the device on ge-0/0/0.0?
A. RIP
B. OSPF
C. BGP and RIP
D. RIP and PIM
-
Question 422:
Which two statements about the use of SCREEN options are correct? (Choose two.)
A. SCREEN options offer protection against various attacks.
B. SCREEN options are deployed prior to route and policy processing in first path packet processing.
C. SCREEN options are deployed at the ingress and egress sides of a packet flow.
D. When you deploy SCREEN options, you must take special care to protect OSPF.
-
Question 423:
You have configured a UTM profile called Block-Spam, which has the appropriate antispam configuration to block undesired spam e-mails.
Which configuration would protect an SMTP server in the dmz zone from spam originating in the untrust zone?
A. set security policies from-zone dmz to-zone untrust policy anti-spam then permit application- services utm-policy Block-Spam
B. set security policies from-zone untrust to-zone dmz policy anti-spam then permit application- services utm-policy Block-Spam
C. set security policies from-zone untrust to-zone dmz policy anti-spam then permit application- services anti-spam-policy Block-Spam
D. set security policies from-zone untrust to-zone dmz policy anti-spam then permit application- services Block-Spam
-
Question 424:
Which statement describes the UTM licensing model?
A. Install the license key and all UTM features will be enabled for the life of the product.
B. Install one license key per feature and the license key will be enabled for the life of the product.
C. Install one UTM license key, which will activate all UTM features; the license will need to be renewed when it expires.
D. Install one UTM license key per UTM feature; the licenses will need to be renewed when they expire.
-
Question 425:
Which IDP policy action closes the connection and sends an RST packet to both the client and the server?
A. close-connection
B. terminate-connection
C. close-client-and-server
D. terminate-session
-
Question 426:
What are two components of the Junos software architecture? (Choose two.)
A. Linux kernel
B. routing protocol daemon
C. session-based forwarding module
D. separate routing and security planes
-
Question 427:
Which two statements are true regarding redundancy groups? (Choose two.)
A. When priority settings are equal and the members participating in a cluster are initialized at the same time, the primary role for redundancy group 0 is assigned to node 0.
B. The preempt option determines the primary and secondary roles for redundancy group 0 during a failure and recovery scenario.
C. Redundancy group 0 manages the control plane failover between the nodes of a cluster.
D. The primary role can be shared for redundancy group 0 when the active-active option is enabled.
-
Question 428:
The Junos OS blocks an HTTP request due to a Websense server response. Which form of Web filtering is being used?
A. redirect Web filtering
B. integrated Web filtering
C. categorized Web filtering
D. local Web filtering
-
Question 429:
What are two TCP flag settings that are considered suspicious? (Choose two.)
A. Do-Not-Fragment flag is set.
B. Both SYN and FIN flags are set.
C. Both ACK and PSH flags are set.
D. FIN flag is set and ACK flag is not set.
-
Question 430:
Which three features are part of the branch SRX series UTM suite? (Choose three.)
A. antispam
B. antivirus
C. IPS
D. application firewalling
E. Web filtering
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-332 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.