Exam Details
Exam Code
:JN0-332Exam Name
:Juniper Networks Certified Internet Specialist, SEC (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:519 Q&AsLast Updated
:Jun 06, 2025
Juniper Juniper Certifications JN0-332 Questions & Answers
-
Question 411:
A network administrator repeatedly receives support calls about network issues. After investigating the issues, the administrator finds that the source NAT pool is running out of addresses.
To be notified that the pool is close to exhaustion, what should the administrator configure?
A. Use the pool-utilization-alarm raise-threshold under the security nat source stanza.
B. Use a trap-group with a category of services under the SNMP stanza.
C. Use an external script that will run a show command on the SRX Series device to see when the pool is close to exhaustion.
D. Configure a syslog message to trigger a notification when the pool is close to exhaustion.
-
Question 412:
Click the Exhibit button.
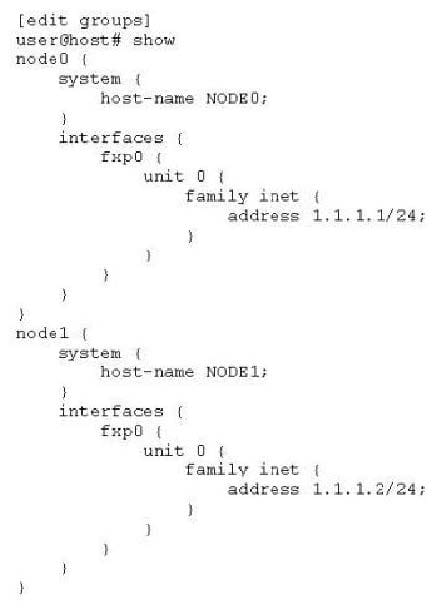
In the exhibit, what is the function of the configuration statements?
A. This section is where you define all chassis clustering configuration.
B. This configuration is required for members of a chassis cluster to talk to each other.
C. You can apply this configuration in the chassis cluster to make configuration easier.
D. This section is where unique node configuration is applied.
-
Question 413:
Which URL will match the URL pattern www.news.com/asia?
A. www.news.com
B. www.news.com/asia/japan
C. www-1.news.com/asia
D. www.news.asia.com
-
Question 414:
Click the Exhibit button.

You are the responder for an IPsec tunnel and you see the error messages shown in the exhibit. What is the problem?
A. One or more of the phase 1 proposals such as authentication algorithm, encryption algorithm, or preshared key does not match.
B. There is no route for 2.2.2.2.
C. There is no IKE definition in the configuration for peer 2.2.2.2.
D. system services ike is not enabled on the interface with IP 1.1.1.2.
-
Question 415:
Which CLI command provides a summary of what the content-filtering engine has blocked?
A. show security utm content-filtering statistics
B. show security flow session
C. show security flow statistics
D. show security utm content-filtering summary
-
Question 416:
Which two statements are true for a security policy? (Choose two.)
A. It controls inter-zone traffic.
B. It controls intra-zone traffic.
C. It is named with a system-defined name.
D. It controls traffic destined to the device's ingress interface.
-
Question 417:
Which zone type will allow transit-traffic?
A. system
B. security
C. default
D. functional
-
Question 418:
Which statement is true regarding a session key in the Diffie-Hellman key-exchange process?
A. A session key value is exchanged across the network.
B. A session key never passes across the network.
C. A session key is used as the key for asymmetric data encryption.
D. A session key is used as the key for symmetric data encryption.
-
Question 419:
Which three situations will trigger an e-mail to be flagged as spam if a branch SRX Series device has been properly configured with antispam inspection enabled for the appropriate security policy? (Choose three.)
A. The server sending the e-mail to the SRX Series device is a known open SMTP relay.
B. The server sending the e-mail to the SRX Series device is running unknown SMTP server software.
C. The server sending the e-mail to the SRX Series device is on an IP address range that is known to be dynamically assigned.
D. The e-mail that the server is sending to the SRX Series device has a virus in its attachment.
E. The server sending the e-mail to the SRX Series device is a known spammer IP address.
-
Question 420:
Which two statements about static NAT are true? (Choose two.)
A. Static NAT can only be used with destination NAT.
B. Static NAT rules take precedence over overlapping dynamic NAT rules.
C. NAT rules take precedence over overlapping static NAT rules.
D. A reverse mapping is automatically created.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-1103
Design, Associate (JNCIA-Design)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-332 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.