Exam Details
Exam Code
:JK0-022Exam Name
:CompTIA Security+ CertificationCertification
:CompTIA Security+Vendor
:CompTIATotal Questions
:1149 Q&AsLast Updated
:Feb 05, 2025
CompTIA CompTIA Security+ JK0-022 Questions & Answers
-
Question 281:
Which of the following is described as an attack against an application using a malicious file?
A. Client side attack
B. Spam
C. Impersonation attack
D. Phishing attack
Correct Answer: A
In this question, a malicious file is used to attack an application. If the application is running on a client computer, this would be a client side attack. Attacking a service or application on a server would be a server side attack.
Client-side attacks target vulnerabilities in client applications interacting with a malicious data. The difference is the client is the one initiating the bad connection. Client-side attacks are becoming more popular. This is because server side attacks are not as easy as they once were according to apache.org. Attackers are finding success going after weaknesses in desktop applications such as browsers, media players, common office applications and e-mail clients. To defend against client-side attacks keep-up the most current application patch levels, keep antivirus software updated and keep authorized software to a minimum.
Incorrect Answers:
B: Spam is most often considered to be electronic junk mail or junk newsgroup postings. Some people define spam even more generally as any unsolicited email. However, if a long-lost brother finds your email address and sends you a
message, this could hardly be called spam, even though it is unsolicited. Real spam is generally email advertising for some product sent to a mailing list or newsgroup.
In addition to wasting people's time with unwanted e-mail, spam also eats up a lot of network bandwidth. Consequently, there are many organizations, as well as individuals, who have taken it upon themselves to fight spam with a variety of
techniques. But because the Internet is public, there is really little that can be done to prevent spam, just as it is impossible to prevent junk mail. However, some online services have instituted policies to prevent spammers from spamming
their subscribers. The attack described in this question is not an example of spam. Therefore, this answer is incorrect.
C: Impersonation is where a person, computer, software application or service pretends to be someone it's not. Impersonation is commonly non-maliciously used in client/server applications. However, it can also be used as a security threat.
However, the attack described in this question is not an example of impersonation.
Therefore, this answer is incorrect.
D: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website,
however, is bogus and set up only to steal the information the user enters on the page.
Phishing emails are blindly sent to thousands, if not millions of recipients. By spamming large groups of people, the "phisher" counts on the email being read by a percentage of people who actually have an account with the legitimate
company being spoofed in the email and corresponding webpage. Phishing, also referred to as brand spoofing or carding, is a variation on "fishing," the idea being that bait is thrown out with the hopes that while most will ignore the bait, some
will be tempted into biting. The attack described in this question is not an example of spam. Therefore, this answer is incorrect.
References: http://blog.botrevolt.com/what-are-client-side-attacks/ http://www.webopedia.com/TERM/S/spam.html http://www.webopedia.com/TERM/P/phishing.html
-
Question 282:
Users at a company report that a popular news website keeps taking them to a web page with derogatory content. This is an example of which of the following?
A. Evil twin
B. DNS poisoning
C. Vishing
D. Session hijacking
Correct Answer: B
DNS spoofing (or DNS cache poisoning) is a computer hacking attack, whereby data is introduced into a Domain Name System (DNS) resolver's cache, causing the name server to return an incorrect IP address, diverting traffic to the attacker's computer (or any other computer). A domain name system server translates a human-readable domain name (such as example.com) into a numerical IP address that is used to route communications between nodes. Normally if the server doesn't know a requested translation it will ask another server, and the process continues recursively. To increase performance, a server will typically remember (cache) these translations for a certain amount of time, so that, if it receives another request for the same translation, it can reply without having to ask the other server again. When a DNS server has received a false translation and caches it for performance optimization, it is considered poisoned, and it supplies the false data to clients. If a DNS server is poisoned, it may return an incorrect IP address, diverting traffic to another computer (in this case, the server hosting the web page with derogatory content).
Incorrect Answers:
A: An evil twin, in the context of network security, is a rogue or fake wireless access point (WAP) that appears as a genuine hotspot offered by a legitimate provider. In an evil twin attack, an eavesdropper or hacker fraudulently creates this
rogue hotspot to collect the personal data of unsuspecting users. Sensitive data can be stolen by spying on a connection or using a phishing technique.
For example, a hacker using an evil twin exploit may be positioned near an authentic Wi-Fi access point and discover the service set identifier (SSID) and frequency. The hacker may then send a radio signal using the exact same frequency
and SSID. To end users, the rogue evil twin appears as their legitimate hotspot with the same name.
In wireless transmissions, evil twins are not a new phenomenon. Historically, they were known as honeypots or base station clones. With the advancement of wireless technology and the use of wireless devices in public areas, it is very easy
for novice users to set up evil twin exploits. This is not what is described in this question. Therefore, this answer is incorrect.
C: Vishing (voice or VoIP phishing) is an electronic fraud tactic in which individuals are tricked into revealing critical financial or personal information to unauthorized entities. Vishing works like phishing but does not always occur over the
Internet and is carried out using voice technology. A vishing attack can be conducted by voice email, VoIP (voice over IP), or landline or cellular telephone. This is not what is described in this question. Therefore, this answer is incorrect.
D: In computer science, session hijacking, sometimes also known as cookie hijacking is the exploitation of a valid computer session--sometimes also called a session key--to gain unauthorized access to information or services in a computer
system. In particular, it is used to refer to the theft of a magic cookie used to authenticate a user to a remote server. It has particular relevance to web developers, as the HTTP cookies used to maintain a session on many web sites can be
easily stolen by an attacker using an intermediary computer or with access to the saved cookies on the victim's computer. This is not what is described in this question. Therefore, this answer is incorrect.
References: http://en.wikipedia.org/wiki/DNS_spoofing http://www.techopedia.com/definition/5057/evil-twin http://searchunifiedcommunications.techtarget.com/definition/vishing http://en.wikipedia.org/wiki/Session_hijacking
-
Question 283:
A user has unknowingly gone to a fraudulent site. The security analyst notices the following system change on the user's host:
Old `hosts' file:
127.0.0.1 localhost New `hosts' file:
127.0.0.1 localhost
5.5.5.5 www.comptia.com
Which of the following attacks has taken place?
A. Spear phishing
B. Pharming
C. Phishing
D. Vishing
Correct Answer: B
We can see in this question that a fraudulent entry has been added to the user's hosts file. This will point the URL: www.comptia.com to 5.5.5.5 instead of the correct IP address. Similar in nature to e-mail phishing, pharming seeks to obtain personal or private (usually financial related) information through domain spoofing. Rather than being spammed with malicious and mischievous e-mail requests for you to visit spoof Web sites which appear legitimate, pharming 'poisons' a DNS server (or hosts file) by infusing false information into the DNS server, resulting in a user's request being redirected elsewhere. Your browser, however will show you are at the correct Web site, which makes pharming a bit more serious and more difficult to detect. Phishing attempts to scam people one at a time with an e-mail while pharming allows the scammers to target large groups of people at one time through domain spoofing.
Incorrect Answers:
A: Spear phishing is an e-mail spoofing fraud attempt that targets a specific organization, seeking unauthorized access to confidential data. As with the e-mail messages used in regular phishing expeditions, spear phishing messages appear
to come from a trusted source. Phishing messages usually appear to come from a large and well-known company or Web site with a broad membership base, such as eBay or PayPal. In the case of spear phishing, however, the apparent
source of the e-mail is likely to be an individual within the recipient's own company and generally someone in a position of authority. In this question, host file poisoning is used rather than email. Therefore, this answer is incorrect.
C: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website,
however, is bogus and set up only to steal the information the user enters on the page. In this question, host file poisoning is used rather than email. Therefore, this answer is incorrect.
D: Vishing (voice or VoIP phishing) is an electronic fraud tactic in which individuals are tricked into revealing critical financial or personal information to unauthorized entities. Vishing works like phishing but does not always occur over the
Internet and is carried out using voice technology. A vishing attack can be conducted by voice email, VoIP (voice over IP), or landline or cellular telephone. In this question, host file poisoning is used rather than voice. Therefore, this answer is
incorrect.
References: http://www.webopedia.com/TERM/P/pharming.html http://searchsecurity.techtarget.com/definition/spear-phishing http://searchunifiedcommunications.techtarget.com/definition/vishing http://www.webopedia.com/ TERM/P/phishing.html
-
Question 284:
A company's employees were victims of a spear phishing campaign impersonating the CEO. The company would now like to implement a solution to improve the overall security posture by assuring their employees that email originated from the CEO. Which of the following controls could they implement to BEST meet this goal?
A. Spam filter
B. Digital signatures
C. Antivirus software
D. Digital certificates
Correct Answer: B
A digital signature is a mathematical technique used to validate the authenticity and integrity of a message, software, or digital document. The digital equivalent of a handwritten signature or stamped seal, but offering far more inherent security, a digital signature is intended to solve the problem of tampering and impersonation in digital communications. Digital signatures can provide the added assurances of evidence to origin, identity and status of an electronic document, transaction or message, as well as acknowledging informed consent by the signer. Digital signatures are based on public key cryptography, also known as asymmetric cryptography. Using a public key algorithm such as RSA, one can generate two keys that are mathematically linked: one private and one public. To create a digital signature, signing software (such as an email program) creates a one-way hash of the electronic data to be signed. The private key is then used to encrypt the hash. The encrypted hash -- along with other information, such as the hashing algorithm -- is the digital signature. The reason for encrypting the hash instead of the entire message or document is that a hash function can convert an arbitrary input into a fixed length value, which is usually much shorter. This saves time since hashing is much faster than signing.
Incorrect Answers:
A: A spam filter is used to detect and block spam email. All inbound (and sometimes outbound) email is passed through the spam filter to detect spam emails. The spam emails are then discarded or tagged as potential spam according to the spam filter configuration. A spam filter is not used to guarantee the integrity of an email.
C: Anti-virus software is software installed on a computer to protect against viruses. An anti- virus program will scan files on the hard drive and scan files as they are accessed to see if the files contain a potential threat. Anti-virus software is not used to guarantee the integrity of an email.
D: In cryptography, a digital certificate is an electronic document that uses a digital signature to bind together a public key with an identity for example, the name of an organization, etc. The certificate is used to confirm that a public key belongs to a specific organization. Digital certificates are used to verify the trustworthiness of a website, while digital signatures are used to verify the trustworthiness of information. In the case of digital certificates, an organization may only trust a site if the digital certificates are issued by the organization itself or by a trusted certification source, like Verisign Inc. But, this doesn't necessarily mean that the content of the site can be trusted; a trusted site may be infiltrated by a hacker who modifies the site's content.
References:
http://searchsecurity.techtarget.com/definition/digital-signature http://searchsecurity.techtarget.com/answer/The-difference-between-a-digital-signature-and- digital- certificate
-
Question 285:
Purchasing receives an automated phone call from a bank asking to input and verify credit card information. The phone number displayed on the caller ID matches the bank. Which of the following attack types is this?
A. Hoax
B. Phishing
C. Vishing
D. Whaling
Correct Answer: C
Vishing (voice or VoIP phishing) is an electronic fraud tactic in which individuals are tricked into revealing critical financial or personal information to unauthorized entities. Vishing works like phishing but does not always occur over the Internet
and is carried out using voice technology. A vishing attack can be conducted by voice email, VoIP (voice over IP), or landline or cellular telephone.
The potential victim receives a message, often generated by speech synthesis, indicating that suspicious activity has taken place in a credit card account, bank account, mortgage account or other financial service in their name. The victim is
told to call a specific telephone number and provide information to "verify identity" or to "ensure that fraud does not occur." If the attack is carried out by telephone, caller ID spoofing can cause the victim's set to indicate a legitimate source,
such as a bank or a government agency.
Vishing is difficult for authorities to trace, particularly when conducted using VoIP. Furthermore, like many legitimate customer services, vishing scams are often outsourced to other countries, which may render sovereign law enforcement
powerless. Consumers can protect themselves by suspecting any unsolicited message that suggests they are targets of illegal activity, no matter what the medium or apparent source. Rather than calling a number given in any unsolicited
message, a consumer should directly call the institution named, using a number that is known to be valid, to verify all recent activity and to ensure that the account information has not been tampered with.
Incorrect Answers:
A: A hoax is something that makes a person believe that something is real when it is not. A hoax is usually not malicious or theft. Therefore, this answer is incorrect.
B: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website,
however, is bogus and set up only to steal the information the user enters on the page.
Phishing emails are blindly sent to thousands, if not millions of recipients. By spamming large groups of people, the "phisher" counts on the email being read by a percentage of people who actually have an account with the legitimate
company being spoofed in the email and corresponding webpage. In this question, a telephone call was received so this is an example of vishing rather than phishing. Therefore, this answer is incorrect.
D: Whaling is a specific kind of malicious hacking within the more general category of phishing, which involves hunting for data that can be used by the hacker. In general, phishing efforts are focused on collecting personal data about users.
In whaling, the targets are high-ranking bankers, executives or others in powerful positions or job titles. Hackers who engage in whaling often describe these efforts as "reeling in a big fish," applying a familiar metaphor to the process of
scouring technologies for loopholes and opportunities for data theft. Those who are engaged in whaling may, for example, hack into specific networks where these powerful individuals work or store sensitive data. They may also set up
keylogging or other malware on a work station associated with one of these executives. There are many ways that hackers can pursue whaling, leading C-level or top-level executives in business and government to stay vigilant about the
possibility of cyber threats. In this question, the `attack' was targeted towards the purchasing department rather than company executives. Therefore, this answer is incorrect.
References:
http://searchunifiedcommunications.techtarget.com/definition/vishing http://www.webopedia.com/TERM/P/phishing.html http://www.techopedia.com/definition/28643/whaling
-
Question 286:
Jane, an individual, has recently been calling various financial offices pretending to be another person to gain financial information. Which of the following attacks is being described?
A. Phishing
B. Tailgating
C. Pharming
D. Vishing
Correct Answer: D
Vishing (voice or VoIP phishing) is an electronic fraud tactic in which individuals are tricked into revealing critical financial or personal information to unauthorized entities. Vishing works like phishing but does not always occur over the Internet
and is carried out using voice technology. A vishing attack can be conducted by voice email, VoIP (voice over IP), or landline or cellular telephone.
The potential victim receives a message, often generated by speech synthesis, indicating that suspicious activity has taken place in a credit card account, bank account, mortgage account or other financial service in their name. The victim is
told to call a specific telephone number and provide information to "verify identity" or to "ensure that fraud does not occur." If the attack is carried out by telephone, caller ID spoofing can cause the victim's set to indicate a legitimate source,
such as a bank or a government agency.
Vishing is difficult for authorities to trace, particularly when conducted using VoIP. Furthermore, like many legitimate customer services, vishing scams are often outsourced to other countries, which may render sovereign law enforcement powerless.
Consumers can protect themselves by suspecting any unsolicited message that suggests they are targets of illegal activity, no matter what the medium or apparent source. Rather than calling a number given in any unsolicited message, a consumer should directly call the institution named, using a number that is known to be valid, to verify all recent activity and to ensure that the account information has not been tampered with.
Incorrect Answers:
A: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website,
however, is bogus and set up only to steal the information the user enters on the page.
Phishing emails are blindly sent to thousands, if not millions of recipients. By spamming large groups of people, the "phisher" counts on the email being read by a percentage of people who actually have an account with the legitimate
company being spoofed in the email and corresponding webpage. In this question, Jane uses the telephone so this is an example of vishing rather than phishing. Therefore, this answer is incorrect.
B: Tailgating in IT security would be an unauthorized person following and authorized person into a building or room such as a datacenter. If a building has a card reader where an authorized person can hold up a card to the reader to unlock
the door, someone tailgating could follow the authorized person into the building by walking through the door before it closes and locks. This is not what is described in the question. Therefore, this answer is incorrect.
C: Similar in nature to e-mail phishing, pharming seeks to obtain personal or private (usually financial related) information through domain spoofing. Rather than being spammed with malicious and mischievous e-mail requests for you to visit
spoof Web sites which appear legitimate, pharming 'poisons' a DNS server by infusing false information into the DNS server, resulting in a user's request being redirected elsewhere. Your browser, however will show you are at the correct
Web site, which makes pharming a bit more serious and more difficult to detect. Phishing attempts to scam people one at a time with an e-mail while pharming allows the scammers to target large groups of people at one time through domain
spoofing. This is not what is described in the question. Therefore, this answer is incorrect.
References:
http://searchunifiedcommunications.techtarget.com/definition/vishing http://www.webopedia.com/TERM/P/phishing.html http://www.webopedia.com/TERM/P/pharming.html
-
Question 287:
A security administrator notices large amounts of traffic within the network heading out to an external website. The website seems to be a fake bank site with a phone number that when called, asks for sensitive information. After further investigation, the security administrator notices that a fake link was sent to several users. This is an example of which of the following attacks?
A. Vishing
B. Phishing
C. Whaling
D. SPAM
E. SPIM
Correct Answer: B
Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security, or bank account numbers, that the legitimate organization already has. The website,
however, is bogus and set up only to steal the information the user enters on the page.
Phishing emails are blindly sent to thousands, if not millions of recipients. By spamming large groups of people, the "phisher" counts on the email being read by a percentage of people who actually have an account with the legitimate
company being spoofed in the email and corresponding webpage. Phishing, also referred to as brand spoofing or carding, is a variation on "fishing," the idea being that bait is thrown out with the hopes that while most will ignore the bait, some
will be tempted into biting.
Incorrect Answers:
A: Vishing is the telephone equivalent of phishing. Vishing is the act of using the telephone in an attempt to scam the user into surrendering private information that will be used for identity theft. The scammer calls the victim, usually pretending to be a legitimate business and fools the victim into thinking he or she will profit. The question states that a fake link was sent to several users (probably by email). Therefore, this is not the correct answer.
C: Whaling is a specific kind of malicious hacking within the more general category of phishing, which involves hunting for data that can be used by the hacker. In general, phishing efforts are focused on collecting personal data about users. In whaling, the targets are high-ranking bankers, executives or others in powerful positions or job titles. Hackers who engage in whaling often describe these efforts as "reeling in a big fish," applying a familiar metaphor to the process of scouring technologies for loopholes and opportunities for data theft. Those who are engaged in whaling may, for example, hack into specific networks where these powerful individuals work or store sensitive data. They may also set up keylogging or other malware on a work station associated with one of these executives. There are many ways that hackers can pursue whaling, leading C-level or top-level executives in business and government to stay vigilant about the possibility of cyber threats. The question states that a fake link was sent to several users (probably by email). As the email was sent to general users rather than upper management, this is not the correct answer.
D: Spam is most often considered to be electronic junk mail or junk newsgroup postings. Some people define spam even more generally as any unsolicited email. However, if a long-lost brother finds your email address and sends you a message, this could hardly be called spam, even though it is unsolicited. Real spam is generally email advertising for some product sent to a mailing list or newsgroup. In addition to wasting people's time with unwanted e-mail, spam also eats up a lot of network bandwidth. Consequently, there are many organizations, as well as individuals, who have taken it upon themselves to fight spam with a variety of techniques. But because the Internet is public, there is really little that can be done to prevent spam, just as it is impossible to prevent junk mail. However, some online services have instituted policies to prevent spammers from spamming their subscribers. Spam is usually marketing for legitimate businesses, not fake imitation web sites. Therefore, this is not the correct answer.
E: SPIM is a term sometimes used to refer to spam over IM (Instant Messaging). It's also called just spam, instant spam, or IM marketing. No matter what the name, it consists of unwanted messages transmitted through some form of instant messaging service, which can include Short Message Service (SMS). The question states that a fake link was sent to several users (probably by email). Therefore, this is not the correct answer.
References: http://www.webopedia.com/TERM/P/phishing.html http://www.webopedia.com/TERM/V/vishing.html http://www.techopedia.com/definition/28643/whaling http://www.webopedia.com/TERM/S/spam.html
-
Question 288:
Several users' computers are no longer responding normally and sending out spam email to the users' entire contact list. This is an example of which of the following?
A. Trojan virus
B. Botnet
C. Worm outbreak
D. Logic bomb
Correct Answer: C
A worm is similar to a virus but is typically less malicious. A virus will usually cause damage to the system or files whereas a worm will usually just spread itself either using the network or by sending emails.
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike
a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a
targeted computer.
Incorrect Answers:
A: In computers, a Trojan horse is a program in which malicious or harmful code is contained inside apparently harmless programming or data in such a way that it can get control and do its chosen form of damage, such as ruining the file allocation table on your hard disk. In one celebrated case, a Trojan horse was a program that was supposed to find and destroy computer viruses. A Trojan horse may be widely redistributed as part of a computer virus. In this question, no actual damage was done to the computers. Emails were sent to spread the worm. Therefore, this answer is incorrect.
B: A botnet is a collection of Internet-connected programs communicating with other similar programs in order to perform tasks. This can be as mundane as keeping control of an Internet Relay Chat (IRC) channel, or it could be used to send spam email or participate in distributed denial-of-service attacks. The word botnet is a combination of the words robot and network. The term is usually used with a negative or malicious connotation. Computers can be co-opted into a botnet when they execute malicious software. This can be accomplished by luring users into making a drive-by download, exploiting web browser vulnerabilities, or by tricking the user into running a Trojan horse program, which may come from an email attachment. This malware will typically install modules that allow the computer to be commanded and controlled by the botnet's operator. Many computer users are unaware that their computer is infected with bots. Depending on how it is written, a Trojan may then delete itself, or may remain present to update and maintain the modules. Botnets can be used to send spam emails but this would be done by someone controlling the computers to target an individual or entity with the spam. A worm would use its own programming to send emails to everyone in a contact list with the aim of spreading itself. Therefore, this answer is incorrect.
D: A logic bomb is a piece of code intentionally inserted into a software system that will set off a malicious function when specified conditions are met. For example, a programmer may hide a piece of code that starts deleting files should they ever be terminated from the company. Software that is inherently malicious, such as viruses and worms, often contain logic bombs that execute a certain payload at a pre-defined time or when some other condition is met. This technique can be used by a virus or worm to gain momentum and spread before being noticed. Some viruses attack their host systems on specific dates, such as Friday the 13th or April Fool's Day. Trojans that activate on certain dates are often called "time bombs". To be considered a logic bomb, the payload should be unwanted and unknown to the user of the software. As an example, trial programs with code that disables certain functionality after a set time are not normally regarded as logic bombs. A logic bomb may contain a worm but it is the worm that is sending the emails. Therefore, this answer is incorrect.
References: http://en.wikipedia.org/wiki/Computer_worm http://searchsecurity.techtarget.com/definition/Trojan-horse http://en.wikipedia.org/wiki/Botnet http://en.wikipedia.org/wiki/Logic_bomb
-
Question 289:
Mike, a user, states that he is receiving several unwanted emails about home loans. Which of the following is this an example of?
A. Spear phishing
B. Hoaxes
C. Spoofing
D. Spam
Correct Answer: D
Spam is most often considered to be electronic junk mail or junk newsgroup postings. Some people define spam even more generally as any unsolicited email. However, if a long-lost brother finds your email address and sends you a message, this could hardly be called spam, even though it is unsolicited. Real spam is generally email advertising for some product sent to a mailing list or newsgroup. In addition to wasting people's time with unwanted e-mail, spam also eats up a lot of network bandwidth. Consequently, there are many organizations, as well as individuals, who have taken it upon themselves to fight spam with a variety of techniques. But because the Internet is public, there is really little that can be done to prevent spam, just as it is impossible to prevent junk mail. However, some online services have instituted policies to prevent spammers from spamming their subscribers. There is some debate about why it is called spam, but the generally accepted version is that it comes from the Monty Python song, "Spam spam spam spam, spam spam spam spam, lovely spam, wonderful spam". Like the song, spam is an endless repetition of worthless text. Another school of thought maintains that it comes from the computer group lab at the University of Southern California who gave it the name because it has many of the same characteristics as the lunch meat Spam: Nobody wants it or ever asks for it. No one ever eats it; it is the first item to be pushed to the side when eating the entree. Sometimes it is actually tasty, like 1% of junk mail that is really useful to some people. The term spam can also be used to describe any "unwanted" email from a company or website -- typically at some point a user would have agreed to receive the email via subscription list opt-in -- a newer term called graymail is used to describe this particular type of spam.
Incorrect Answers:
A: Spear phishing is an e-mail spoofing fraud attempt that targets a specific organization, seeking unauthorized access to confidential data. As with the e-mail messages used in regular phishing expeditions, spear phishing messages appear
to come from a trusted source. Phishing messages usually appear to come from a large and well-known company or Web site with a broad membership base, such as eBay or PayPal. In the case of spear phishing, however, the apparent
source of the e-mail is likely to be an individual within the recipient's own company and generally someone in a position of authority. In this question, the emails are trying to sell home loans rather than trying to access confidential data.
Therefore, this answer is incorrect.
B: A hoax is something that makes a person believe that something is real when it is not. In this question, the emails are likely to be genuine in terms of selling home loans. Therefore, this answer is incorrect.
C: There are several kinds of spoofing including email, caller ID, MAC address, and uniform resource locator (URL) spoof attacks. All types of spoofing are designed to imitate something or someone.
Email spoofing (or phishing), used by dishonest advertisers and outright thieves, occurs when email is sent with falsified "From:" entry to try and trick victims that the message is from a friend, their bank, or some other legitimate source. Any
email that claims it requires your password or any personal information could be a trick.
In a caller ID attack, the spoofer will falsify the phone number he/she is calling from. In this question, the emails are likely to be genuine in terms of selling home loans and not from `spoofed' addresses. Therefore, this answer is incorrect.
References: http://www.webopedia.com/TERM/S/spam.html http://searchsecurity.techtarget.com/definition/spear-phishing
-
Question 290:
Which of the following BEST describes the type of attack that is occurring? (Select TWO).
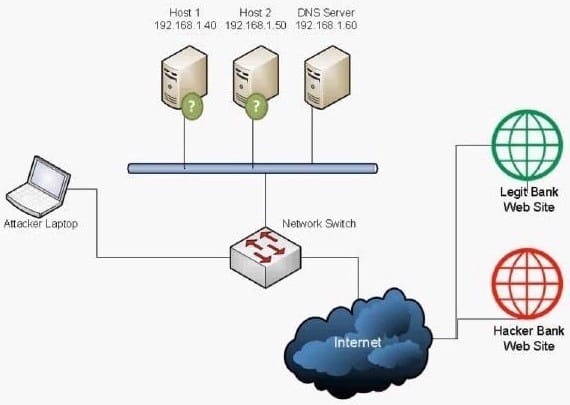
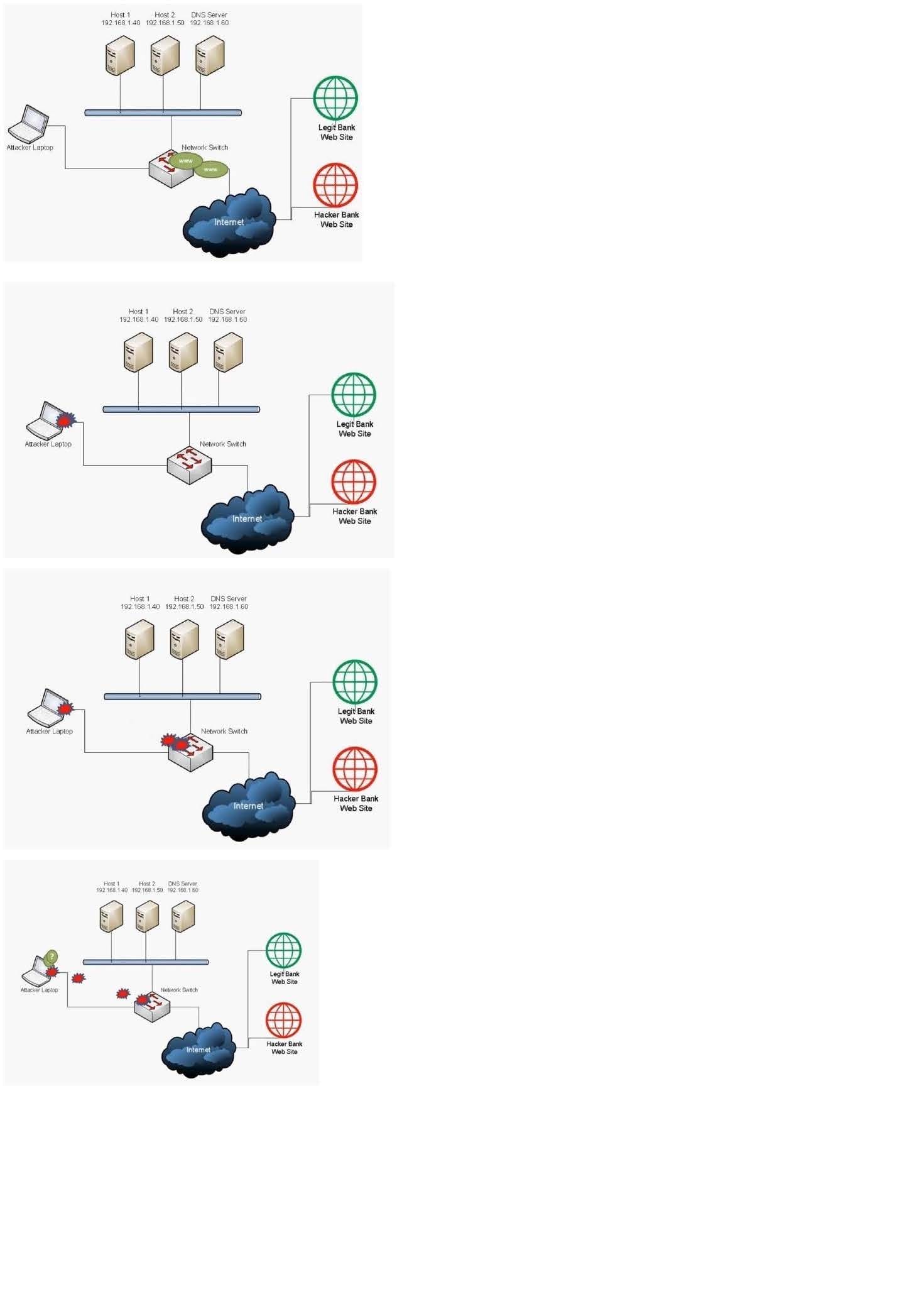
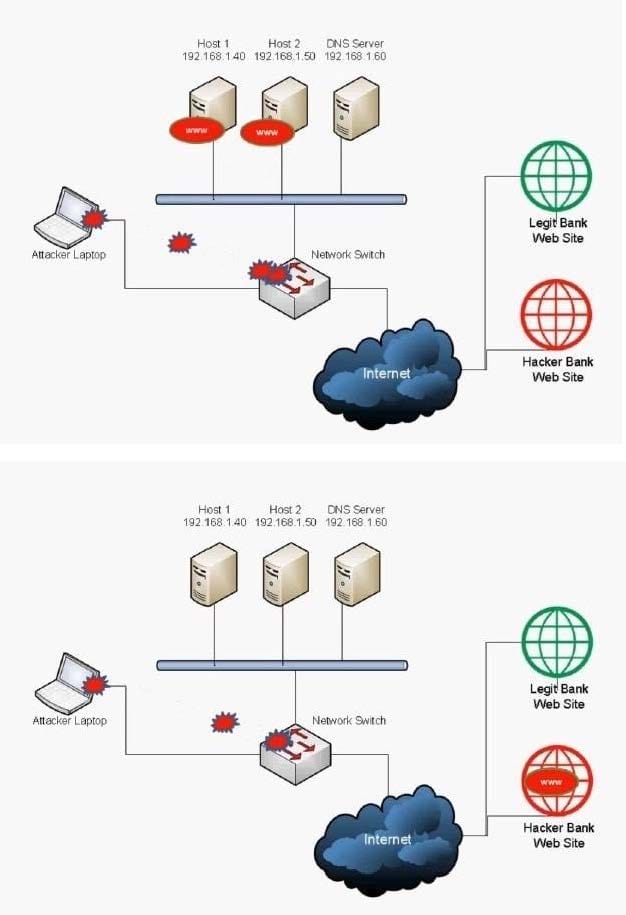
A. DNS spoofing
B. Man-in-the-middle
C. Backdoor
D. Replay
E. ARP attack
F. Spear phishing
G. Xmas attack
Correct Answer: AE
We have a legit bank web site and a hacker bank web site. The hacker has a laptop connected to the network. The hacker is redirecting bank web site users to the hacker bank web site instead of the legit bank web site. This can be done using two methods: DNS Spoofing and ARP Attack (ARP Poisoning).
A: DNS spoofing (or DNS cache poisoning) is a computer hacking attack, whereby data is introduced into a Domain Name System (DNS) resolver's cache, causing the name server to return an incorrect IP address, diverting traffic to the
attacker's computer (or any other computer). A domain name system server translates a human-readable domain name (such as example.com) into a numerical IP address that is used to route communications between nodes. Normally if the
server doesn't know a requested translation it will ask another server, and the process continues recursively. To increase performance, a server will typically remember (cache) these translations for a certain amount of time, so that, if it
receives another request for the same translation, it can reply without having to ask the other server again.
When a DNS server has received a false translation and caches it for performance optimization, it is considered poisoned, and it supplies the false data to clients. If a DNS server is poisoned, it may return an incorrect IP address, diverting
traffic to another computer (in this case, the hacker bank web site server).
E: Address Resolution Protocol poisoning (ARP poisoning) is a form of attack in which an attacker changes the Media Access Control (MAC) address and attacks an Ethernet LAN by changing the target computer's ARP cache with a forged
ARP request and reply packets. This modifies the layer -Ethernet MAC address into the hacker's known MAC address to monitor it. Because the ARP replies are forged, the target computer unintentionally sends the frames to the hacker's
computer first instead of sending it to the original destination. As a result, both the user's data and privacy are compromised. An effective ARP poisoning attempt is undetectable to the user.
ARP poisoning is also known as ARP cache poisoning or ARP poison routing (APR).
Incorrect Answers:
B: In cryptography and computer security, a man-in-the-middle attack (often abbreviated to MITM, MitM, MIM, MiM or MITMA) is an attack where the attacker secretly relays and possibly alters the communication between two parties who
believe they are directly communicating with each other. One example is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking
directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is
straightforward in many circumstances; for example, an attacker within reception range of an unencrypted Wi-Fi wireless access point, can insert himself as a man-in-the-middle. This is not the attack illustrated in this question. Therefore, this
answer is incorrect.
C: A backdoor in a computer system (or cryptosystem or algorithm) is a method of bypassing normal authentication, securing unauthorized remote access to a computer, obtaining access to plaintext, and so on, while attempting to remain
undetected. The backdoor may take the form of an installed program (e.g., Back Orifice) or may subvert the system through a rootkit. A backdoor in a login system might take the form of a hard coded user and password combination which
gives access to the system.
Although the number of backdoors in systems using proprietary software (software whose source code is not publicly available) is not widely credited, they are nevertheless frequently exposed. Programmers have even succeeded in secretly
installing large amounts of benign code as Easter eggs in programs, although such cases may involve official forbearance, if not actual permission. This is not the attack illustrated in this question. Therefore, this answer is incorrect.
D: A replay attack (also known as playback attack) is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts
the data and retransmits it, possibly as part of a masquerade attack by IP packet substitution (such as stream cipher attack). For example: Suppose Alice wants to prove her identity to Bob. Bob requests her password as proof of identity,
which Alice dutifully provides (possibly after some transformation like a hash function); meanwhile, Eve is eavesdropping on the conversation and keeps the password (or the hash). After the interchange is over, Eve (posing as Alice) connects
to Bob; when asked for a proof of identity, Eve sends Alice's password (or hash) read from the last session, which Bob accepts thus granting access to Eve. This is not the attack illustrated in this question. Therefore, this answer is incorrect.
F: Spear phishing is an e-mail spoofing fraud attempt that targets a specific organization, seeking unauthorized access to confidential data. As with the e-mail messages used in regular phishing expeditions, spear phishing messages appear
to come from a trusted source. Phishing messages usually appear to come from a large and well-known company or Web site with a broad membership base, such as eBay or PayPal. In the case of spear phishing, however, the apparent
source of the e-mail is likely to be an individual within the recipient's own company and generally someone in a position of authority. This is not the attack illustrated in this question.
Therefore, this answer is incorrect.
G: In information technology, a Christmas tree packet is a packet with every single option set for whatever protocol is in use. The term derives from a fanciful image of each little option bit in a header being represented by a different-colored
light bulb, all turned on, as in, "the packet was lit up like a Christmas tree." It can also be known as a kamikaze packet, nastygram or a lamp test segment.
Christmas tree packets can be used as a method of divining the underlying nature of a TCP/IP stack by sending the packets and awaiting and analyzing the responses. When used as part of scanning a system, the TCP header of a Christmas
tree packets has the flags SYN, FIN, URG and PSH set. Many operating systems implement their compliance with the Internet Protocol standard (RFC 791) in varying or incomplete ways. By observing how a host responds to an odd packet,
such as a Christmas tree packet, assumptions can be made regarding the host's operating system. Versions of Microsoft Windows, BSD/OS, HP-UX, Cisco IOS, MVS, and IRIX display behaviors that differ from the RFC standard when
queried with said packets. A large number of Christmas tree packets can also be used to conduct a DoS attack by exploiting the fact that Christmas tree packets require much more processing by routers and end-hosts than the 'usual' packets
do.
Christmas tree packets can be easily detected by intrusion-detection systems or more advanced firewalls. From a network security point of view, Christmas tree packets are always suspicious and indicate a high probability of network
reconnaissance activities. This is not the attack illustrated in this question. Therefore, this answer is incorrect.
References: http://en.wikipedia.org/wiki/DNS_spoofing http://www.techopedia.com/definition/27471/address-resolution-protocol-poisoning-arp- poisoning http://en.wikipedia.org/wiki/Man-in-the-middle_attack http://en.wikipedia.org/wiki/Backdoor_%28computing%29 http://en.wikipedia.org/wiki/Replay_attack http://searchsecurity.techtarget.com/definition/spear-phishing http://en.wikipedia.org/wiki/Christmas_tree_packet
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JK0-022 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.