Exam Details
Exam Code
:GSLCExam Name
:GIAC Security Leadership Certification (GSLC)Certification
:GIAC Information SecurityVendor
:GIACTotal Questions
:701 Q&AsLast Updated
:Oct 25, 2024
GIAC GIAC Information Security GSLC Questions & Answers
-
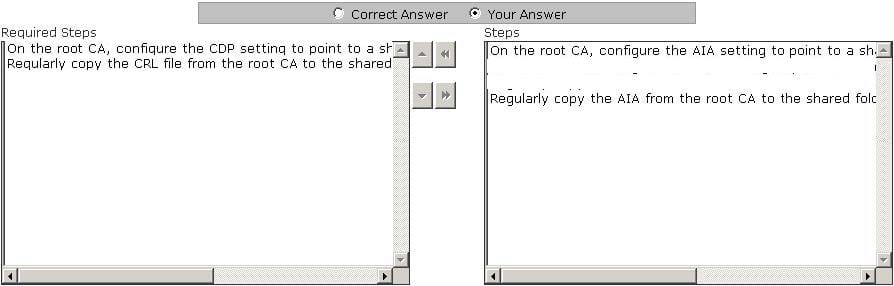
Question 681:
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. All client computers on the
network run Windows XP Professional. You configure a public key infrastructure (PKI) on the network. You configure a root CA and a subordinate CA on the network.
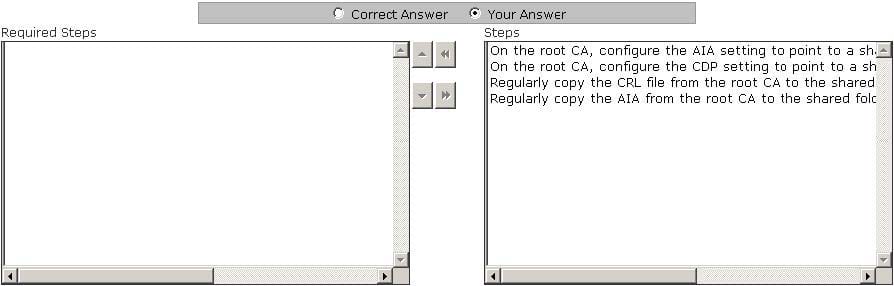
For security reasons, you want to take the root CA offline. You are required to configure the CA servers to support for certificate revocation. Choose the steps you will require to accomplish the task.
Select and Place:

-
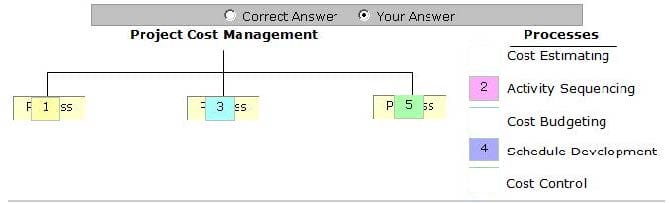
Question 682:
Place the processes that are grouped under the Project Cost Management Knowledge Area in the image below.
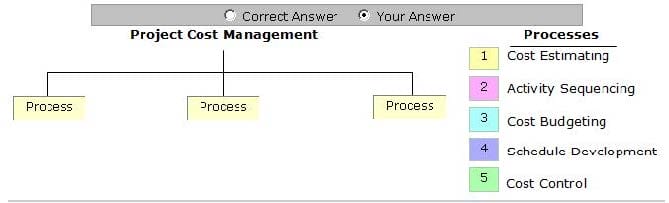
Select and Place:

-
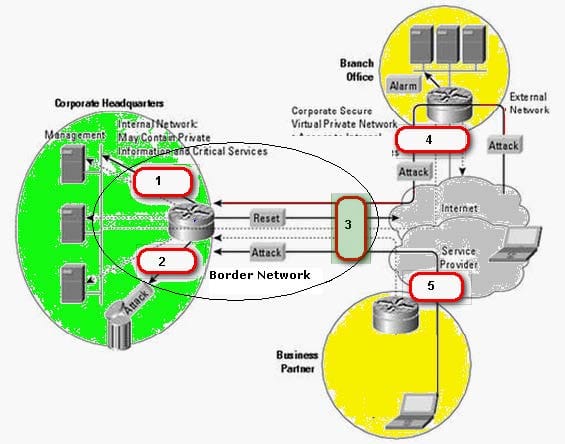
Question 683:
You work as a Security manager for Caterxiss Inc. The headquarters of your company is connected to the branch office in another state and a service partner in the same state. The network of the company is being attacked from the connected networks. You decide to analyze and then prevent the corporate headquarters network from these attacks using a Snort IDS.
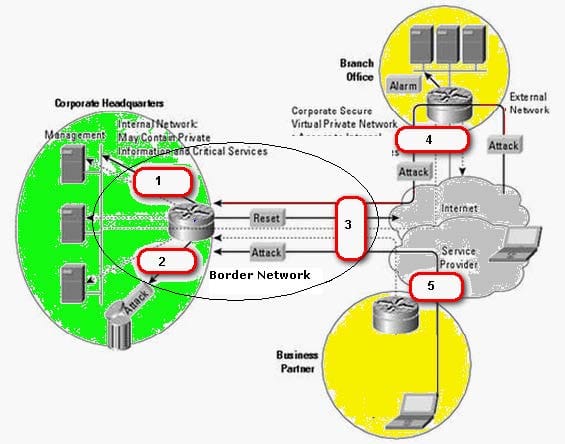
What is the most appropriate spot on the network where you should set up an Intrusion detection system (IDS)?
Hot Area:
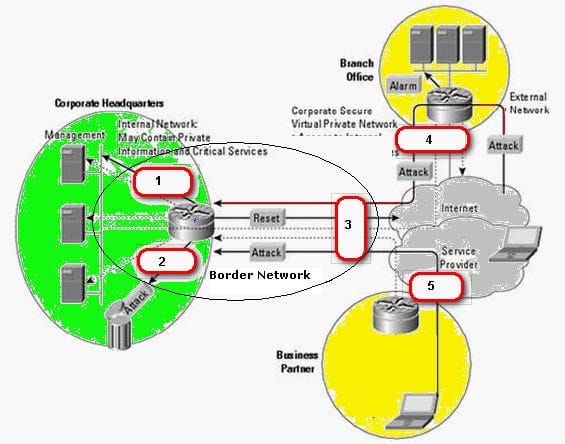
-
Question 684:
Fill in the blank with the appropriate tool name.
________ is a wireless network cracking tool that exploits the vulnerabilities in the RC4 Algorithm, which comprises the WEP security parameters.
-
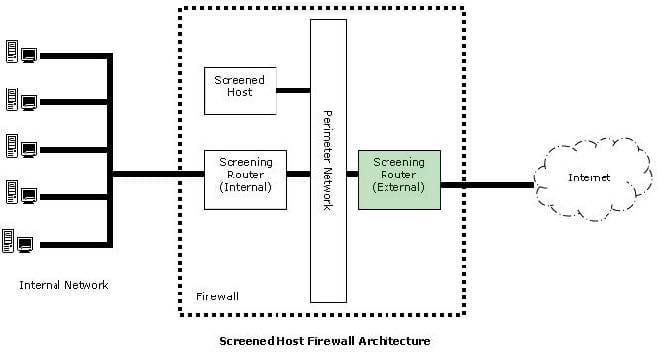
Question 685:
In the image of the Screened Host Firewall Architecture given below, select the element that is commonly known as the access router.
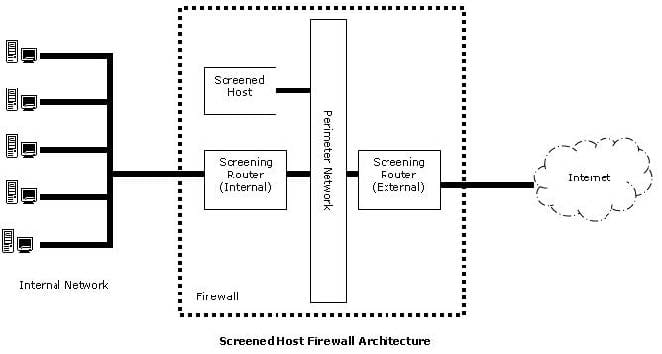
Hot Area:
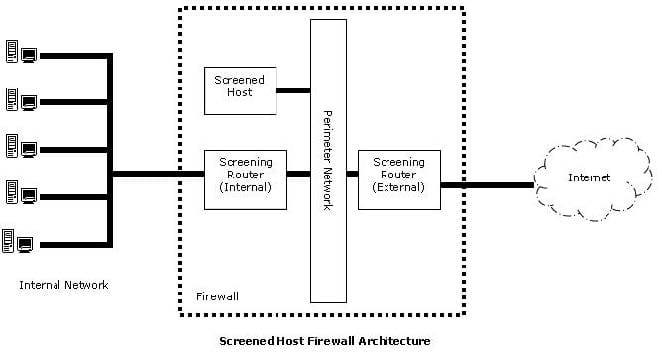
-
Question 686:
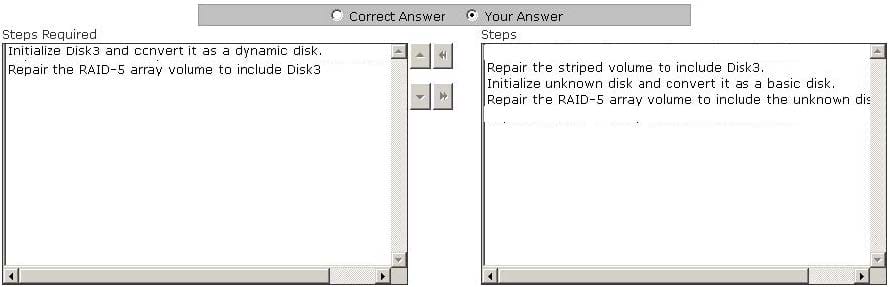
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 single domain-based Active Directory network. The network has five Windows 2003 member servers and 200 Windows XP Professional client computers. One of the member servers named FSERV works as a file server. A three disk RAID-5 array that is used for data storage is configured on FSERV. One morning, during a routine checkup Mark notices that one of the disks of the RAID-5 array has failed. Mark replaces the failed disk with a new one. He restarts the server, runs the Disk Management utility. The status of the RAID-5 array disks shows Disk3 as not initialized and its status as unknown. The array also lists a missing offline dynamic disk. Mark wants to restore the fault tolerant RAID-5 array volume. Choose the required steps that Mark has to take to accomplish the task and arrange them in the correct order.
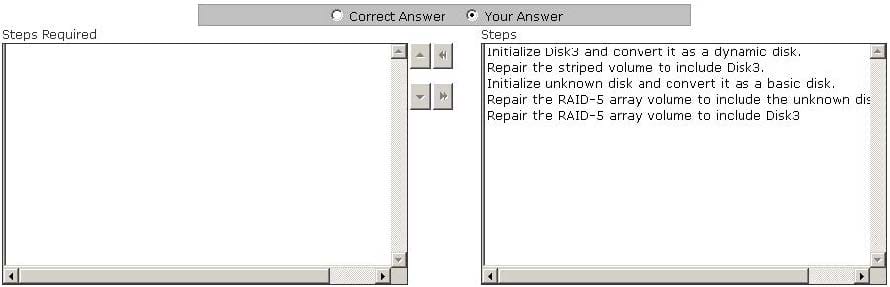
Select and Place:

-
Question 687:
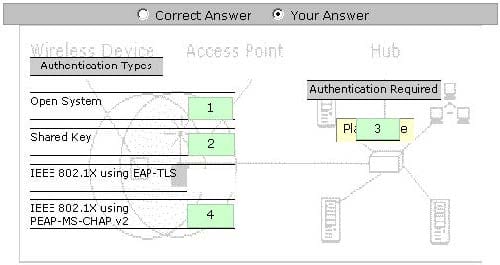
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. The company has recently provided laptops to its sales team members. You have configured access points in the network to enable a wireless network. The company's security policy states that all users using laptops must use smart cards for authentication. Select and
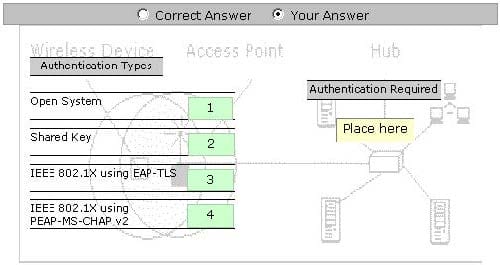
place the authentication method you are required to configure to implement the security policy of the company.
Select and Place:

-
Question 688:
You work as a Network Administrator for Net World International. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. All client computers on the network run Windows XP Professional. You are configuring public key interface (PKI) to support the domain users and computers. All users will use smart cards for logon. You have configured a global group named SCIssuer that will issue smart cards for all domain users. A file server named SecServer is configured on the network. The certificate-based IPSec encryption is required for all communications to and from the SecServer server. A VPN server is configured on the network to enable sales managers to connect to the network from the remote locations. They will use their laptops, which run Windows XP Professional, to connect to the network. The L2TP connection is required for the VPN server. Place the users, computers, and groups to the certificate templates that are required for implementing the PKI infrastructure.
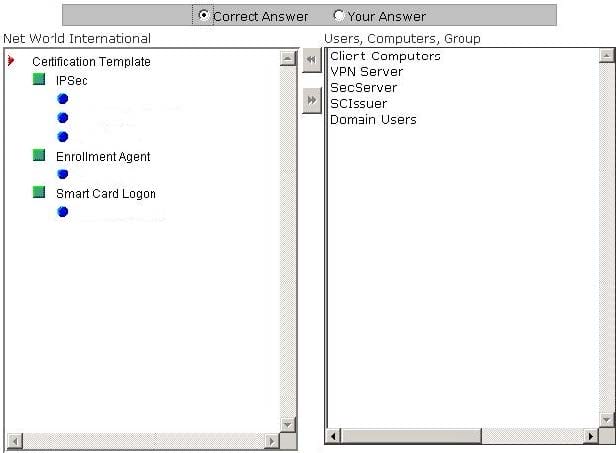
Select and Place:

-
Question 689:
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. According to the company's security policy, you want to apply a firewall profile to the network.Choose the firewall profiles supported by Windows Server 2008 and Windows Vista.
Select and Place:

-
Question 690:
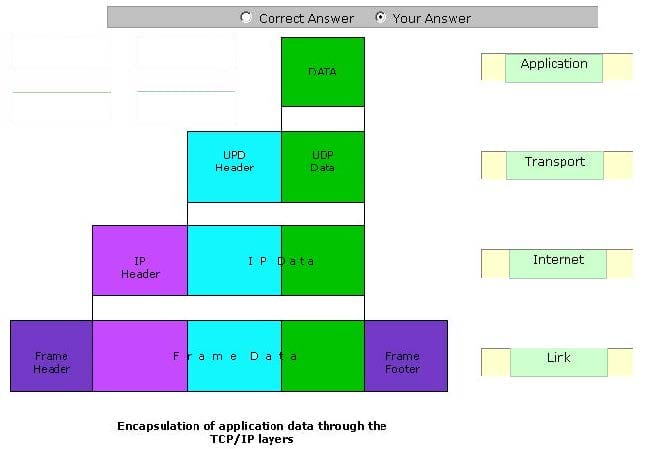
Drag and Drop the layers of TCP/IP model according to their level of data encapsulation.

Select and Place:

Related Exams:
G2700
GIAC Certified ISO-2700 Specialist Practice TestGCED
GIAC Certified Enterprise Defender Practice TestGCFW
GIAC Certified Firewall AnalystGCIA
GIAC Certified Intrusion AnalystGCIH
GIAC Certified Incident HandlerGCPM
GIAC Certified Project Manager Certification Practice TestGISF
GIAC Information Security FundamentalsGISP
GIAC Information Security ProfessionalGNSA
GIAC Systems and Network AuditorGPEN
GIAC Certified Penetration Tester
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GIAC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your GSLC exam preparations and GIAC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.