Exam Details
Exam Code
:GSLCExam Name
:GIAC Security Leadership Certification (GSLC)Certification
:GIAC Information SecurityVendor
:GIACTotal Questions
:701 Q&AsLast Updated
:Oct 25, 2024
GIAC GIAC Information Security GSLC Questions & Answers
-
Question 671:
John works as a Programmer for We-are-secure Inc. On one of his routine visits to the company, he noted down the passwords of the employees while they were typing them on their computer screens. Which of the following social engineering attacks did he just perform?
A. Shoulder surfing
B. Important user posing
C. Dumpster diving
D. Authorization by third party
-
Question 672:
Fill in the blank with the appropriate type of router.
A _________ router performs packet-filtering and is used as a firewall.
-
Question 673:
Fill in the blank with the appropriate term.
____________is a configuration of a network card that makes the card pass all traffic it receives to the central processing unit rather than just packets addressed to it.
-
Question 674:
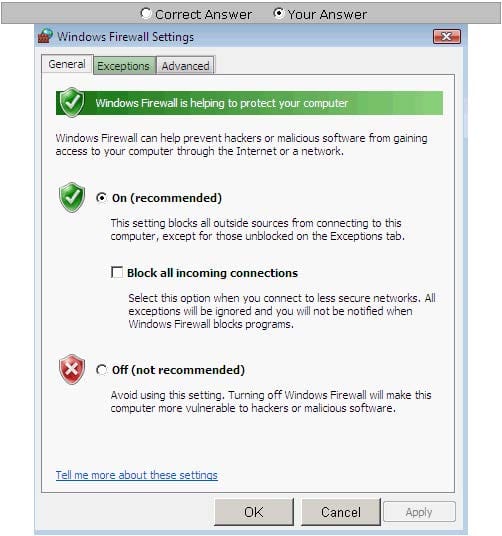
Steve works as a Network Administrator for Blue Tech Inc. All client computers in the company run the Windows Vista operating system. He often travels long distances on official duty. While traveling, he connects to the office server through his laptop by using remote desktop connection. He wants to run an application that is available on the server of the company. When he connects to the server, he gets a message that the connection is blocked by the firewall. He returns to his

office to resolve the issue. He opens the Windows Firewall Settings dialog box. What actions should he perform in the dialog box given below to accomplish the task?
Hot Area:
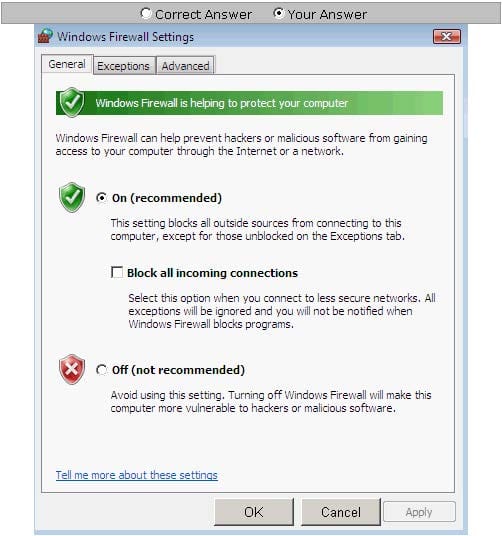
-
Question 675:
You work as a Network Administrator for Net World International. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. All client computers on the
network run Windows XP Professional.
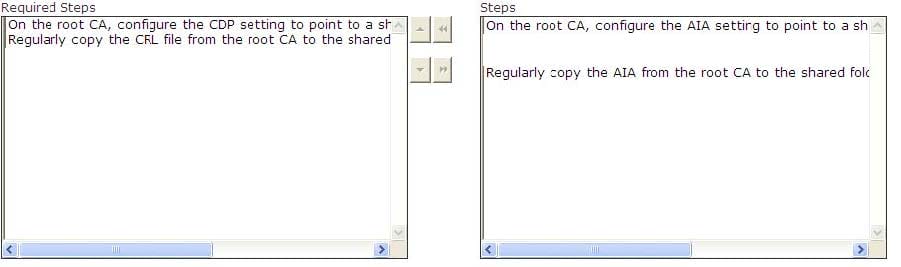
You configure a public key infrastructure (PKI) on the network. You configure a root CA and a subordinate CA on the network. For security reasons, you want to take the root CA offline. You are required to configure the CA servers to support
for certificate revocation. Choose the steps you will require to accomplish the task.
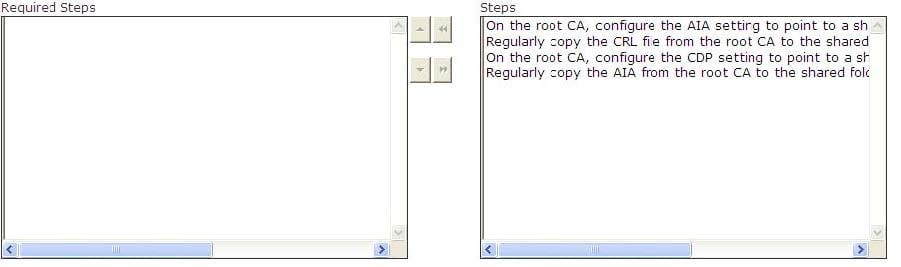
Select and Place:

-
Question 676:
You work as a Network Administrator for Perfect Solutions Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single
domain single forest network. The company's network is connected to the Internet through a T1 line.
The firewall is configured on the network for securing the internal network from the intruders on the Internet. The functional level of the forest is Windows Server 2008.
You are designing a public key infrastructure (PKI) for the network. The security policy of the company states that all users should use smart cards for authentication.
Select and place the type of certificate authority (CA) that is required to be configured on the network to implement the security policy of the company.

Select and Place:

-
Question 677:
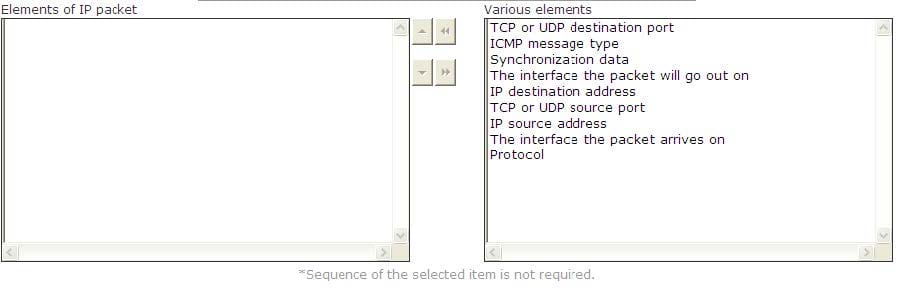
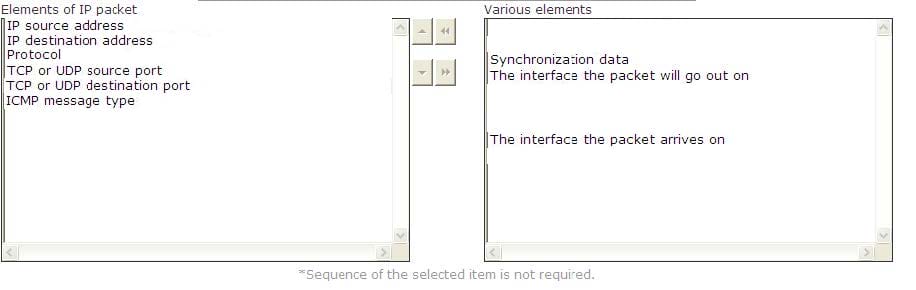
Choose and select the information present in the header of a single IP packet that are helpful in packet filtering.
Select and Place:

-
Question 678:
You work as a Network Administrator for NetTech Inc. The company has a Windows Server 2008 domain-based network. Your assistant wants to know about the security features of the Internet Protocol security (IPSec) configuration option. Select and move the security features with the appropriate IPSec configuration option.
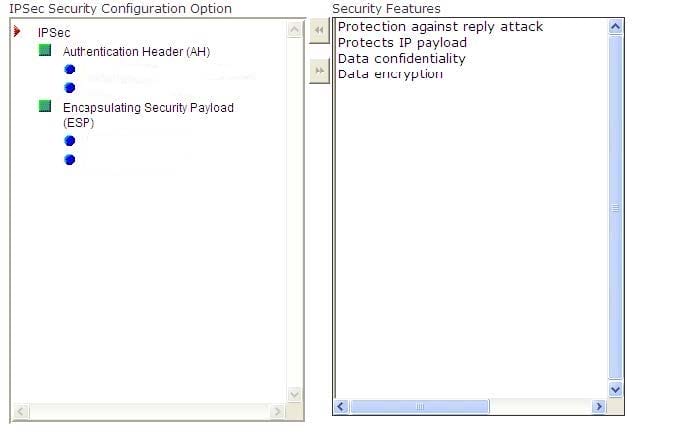
Select and Place:

-
Question 679:
Martha works as a System Administrator for BlueWell Inc. The company provides configuring and troubleshooting support to users for wireless networks. A user named Bob connects his computer to an 802.11 wireless network. He wants to configure 802.1X authentication to improve security on the wireless network. Choose and reorder the steps Martha will assist Bob to take to accomplish the task.
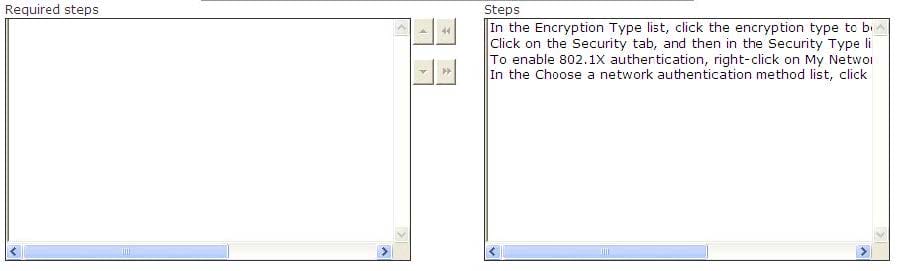
Select and Place:

-
Question 680:
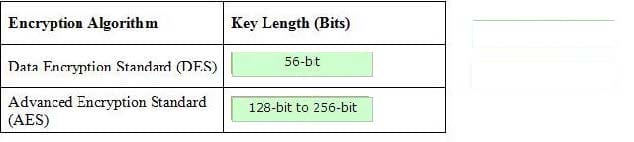
Place the appropriate key length in front of appropriate encryption algorithm.
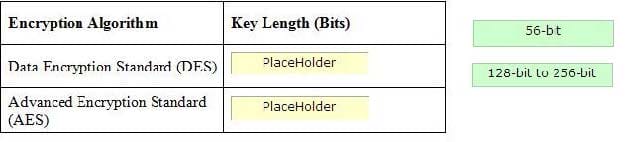
Select and Place:

Related Exams:
G2700
GIAC Certified ISO-2700 Specialist Practice TestGCED
GIAC Certified Enterprise Defender Practice TestGCFW
GIAC Certified Firewall AnalystGCIA
GIAC Certified Intrusion AnalystGCIH
GIAC Certified Incident HandlerGCPM
GIAC Certified Project Manager Certification Practice TestGISF
GIAC Information Security FundamentalsGISP
GIAC Information Security ProfessionalGNSA
GIAC Systems and Network AuditorGPEN
GIAC Certified Penetration Tester
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only GIAC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your GSLC exam preparations and GIAC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.