Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Jun 28, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 281:
An analyst received an alert regarding an application spawning a suspicious command shell process Upon further investigation, the analyst observes the following registry change occurring immediately after the suspicious event:

Which of the following was the suspicious event able to accomplish?
A. Impair defenses.
B. Establish persistence.
C. Bypass file access controls.
D. Implement beaconing.
-
Question 282:
Which of the following lines from this output most likely indicates that attackers could quickly use brute force and determine the negotiated secret session key?
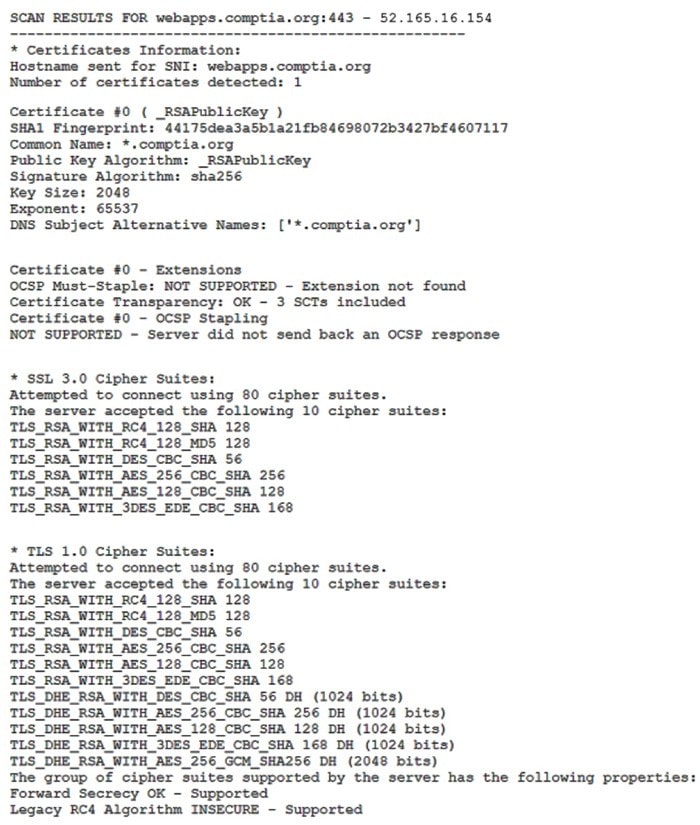
A. TLS_RSA_WITH_DES_CBC_SHA 56
B. TLS_DHE_RSA_WITH_AES_128_CBC_SHA 128 DH (1024 bits)
C. TLS_RSA_WITH_AES_256_CBC_SHA 256
D. TLS_DHE_RSA_WITH_AES_256_GCM_SHA256 DH (2048 bits)
-
Question 283:
A risk assessment concludes that the perimeter network has the highest potential for compromise by an attacker, and it is labeled as a critical risk environment. Which of the following is a valid compensating control to reduce the volume of valuable information in the perimeter network that an attacker could gain using active reconnaissance techniques?
A. A control that demonstrates that all systems authenticate using the approved authentication method
B. A control that demonstrates that access to a system is only allowed by using SSH
C. A control that demonstrates that firewall rules are peer reviewed for accuracy and approved before deployment
D. A control that demonstrates that the network security policy is reviewed and updated yearly
-
Question 284:
A forensic analyst is conducting an investigation on a compromised server Which of the following should the analyst do first to preserve evidence''
A. Restore damaged data from the backup media
B. Create a system timeline
C. Monitor user access to compromised systems
D. Back up all log files and audit trails
-
Question 285:
A cybersecurity analyst is researching operational data to develop a script that will detect the presence of a threat on corporate assets. Which of the following contains the most useful information to produce this script?
A. API documentation
B. Protocol analysis captures
C. MITRE ATTandCK reports
D. OpenloC files
-
Question 286:
A security analyst is reviewing the network security monitoring logs listed below:
Count: 2 Event#3.3505 2020-01-30 10:40 UTC GPL WEB SERVER robots. txt access
10.1.1.128 -> 10.0.0.10 IPVer=4 hlen=5 tos=0 dlen=269 ID=0 flags=0 offset=0 tt1=0 chksum=22704 Protocol: 6 sport=45260 => dport=80 Sec=0 Ack=0 Off=5 Res=0 Flags=******** Win=0 urp=23415 chksum=0
Count: 22 Event#3.3507 2020-01-30 10:40 UTC ET WEB SPECIFIC APPS PHPStudy Remote Code Execution Backdoor
10.1.1.129 -> 10.0.0.10 IPVer=4 hen=5 tos=0 dlen=269 ID=0 flags=0 offset=0 tt1=0 chksum=22704 Protocol: 6 sport=65200 -> dport=80 Sea=0 Ack=0 off=5 Res=0 Flags=******** win=0 urp=26814 chksum=0
Count: 30 Event#3.3522 2020-01-30 10:40 UTC ET WEB SERVER WEB-PHP phpinfo access
10.1.1.130 -> 10.0.0.10 IPVer=4 hen=5 tos=0 dlen=269 ID=0 flags=0 offset=0 tt1=0 chksum=22704 Protocol: 6 sport=58175 -> dport=80 Sec=0 Ack=0 Off=5 Res=0 Flags=******** win=0 urp=22875 chksum=0
Count: 22 Event#3.3728 2020-01-30 10:40 UTC GPL WEB SERVER 403 Forbidden
10.0.0.10 -> 10.1.1.129 IPVer=4 hen=5 tos=0 dlen=533 ID=0 flags=0 offset=0 tt1=0 chksum=20471 Protocol: 6 sport=80 -> dport=65200 Sea=0 Ack=0 Off=5 Res=0 Flags=******** win=0 urp=59638 chksum=0
Which of the following is the analyst MOST likely observing? (Choose two.)
A. 10.1.1.128 sent potential malicious traffic to the web server.
B. 10.1.1.128 sent malicious requests, and the alert is a false positive
C. 10.1.1.129 successfully exploited a vulnerability on the web server
D. 10.1.1.129 sent potential malicious requests to the web server
E. 10.1.1.129 can determine mat port 443 is being used
F. 10.1.1.130 can potentially obtain information about the PHP version
-
Question 287:
A security analyst needs to automate the incident response process for malware infections. When the following logs are generated, an alert email should automatically be sent within 30 minutes:
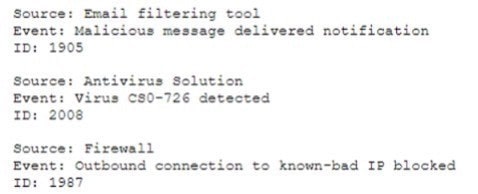
Which of the following is the best way for the analyst to automate alert generation?
A. Deploy a signature-based IDS
B. Install a UEBA-capable antivirus
C. Implement email protection with SPF
D. Create a custom rule on a SIEM
-
Question 288:
An organization wants to consolidate a number of security technologies throughout the organization and standardize a workflow for identifying security issues prioritizing the severity and automating a response Which of the following would best meet the organization's needs'?
A. MaaS
B. SIEM
C. SOAR
D. CI/CD
-
Question 289:
A new prototype for a company's flagship product was leaked on the internet As a result, the management team has locked out all USB drives Optical drive writers are not present on company computers The sales team has been granted an exception to share sales presentation files with third parties Which of the following would allow the IT team to determine which devices are USB enabled?
A. Asset tagging
B. Device encryption
C. Data loss prevention
D. SIEMIogs
-
Question 290:
Which of the following is the greatest security concern regarding ICS?
A. The involved systems are generally hard to identify.
B. The systems are configured for automatic updates, leading to device failure.
C. The systems are oftentimes air gapped, leading to fileless malware attacks.
D. Issues on the systems cannot be reversed without rebuilding the systems.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.