Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Jun 28, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 271:
A penetration tester submitted data to a form in a web application, which enabled the penetration tester to retrieve user credentials. Which of the following should be recommended for remediation of this application vulnerability?
A. Implementing multifactor authentication on the server OS
B. Hashing user passwords on the web application
C. Performing input validation before allowing submission
D. Segmenting the network between the users and the web server
-
Question 272:
A cybersecurity analyst notices unusual network scanning activity coming from a country that the company does not do business with. Which of the following is the best mitigation technique?
A. Geoblock the offending source country.
B. Block the IP range of the scans at the network firewall.
C. Perform a historical trend analysis and look for similar scanning activity.
D. Block the specific IP address of the scans at the network firewall.
-
Question 273:
An analyst has received an IPS event notification from the SIEM stating an IP address, which is known to be malicious, has attempted to exploit a zero-day vulnerability on several web servers. The exploit contained the following snippet:
/wp-json/trx_addons/V2/get/sc_layout?sc=wp_insert_userandrole=administrator
Which of the following controls would work best to mitigate the attack represented by this snippet?
A. Limit user creation to administrators only.
B. Limit layout creation to administrators only.
C. Set the directory trx_addons to read only for all users.
D. Set the directory V2 to read only for all users.
-
Question 274:
Which of the following activities is designed to handle a control failure that leads to a breach?
A. Risk assessment
B. Incident management
C. Root cause analysis
D. Vulnerability management
-
Question 275:
A security team conducts a lessons-learned meeting after struggling to determine who should conduct the next steps following a security event. Which of the following should the team create to address this issue?
A. Service-level agreement
B. Change management plan
C. Incident response plan
D. Memorandum of understanding
-
Question 276:
A code review reveals a web application is using time-based cookies for session management. This is a security concern because time-based cookies are easy to:
A. parameterize
B. decode
C. guess
D. decrypt
-
Question 277:
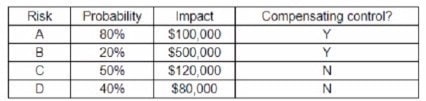
An organization has the following risk mitigation policies
1.
Risks without compensating controls will be mitigated first it the nsk value is greater than $50,000
2.
Other nsk mitigation will be pnontized based on risk value.
The following risks have been identified: Which of the following is the ordei of priority for risk mitigation from highest to lowest?
A. A, C, D, B
B. B, C, D, A
C. C, B, A, D
D. C. D, A, B
E. D, C, B, A
-
Question 278:
Which of the following is the best reason why organizations need operational security controls?
A. To supplement areas that other controls cannot address
B. To limit physical access to areas that contain sensitive data
C. To assess compliance automatically against a secure baseline
D. To prevent disclosure by potential insider threats
-
Question 279:
A technician working at company.com received the following email:
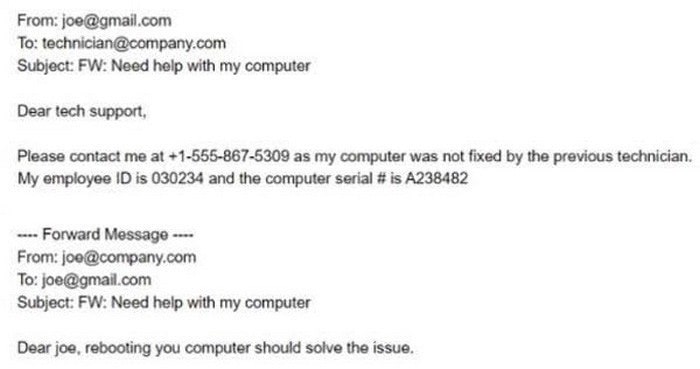
After looking at the above communication, which of the following should the technician recommend to the security team to prevent exposure of sensitive information and reduce the risk of corporate data being stored on non-corporate assets?
A. Forwarding of corporate email should be disallowed by the company.
B. A VPN should be used to allow technicians to troubleshoot computer issues securely.
C. An email banner should be implemented to identify emails coming from external sources.
D. A rule should be placed on the DLP to flag employee IDs and serial numbers.
-
Question 280:
A company is aiming to test a new incident response plan. The management team has made it clear that the initial test should have no impact on the environment. The company has limited resources to support testing. Which of the following exercises would be the best approach?
A. Tabletop scenarios
B. Capture the flag
C. Red team vs. blue team
D. Unknown-environment penetration test
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.