Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jul 07, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 761:
A consumer credit card database was compromised, and multiple representatives are unable to review the appropriate customer information. Which of the following should the cybersecurity analyst do first?
A. Start the containment effort.
B. Confirm the incident.
C. Notify local law enforcement officials.
D. Inform the senior management team.
-
Question 762:
A large company would like a security analyst to recommend a solution that will allow only company laptops to connect to the corporate network. Which of the following technologies should the analyst recommend?
A. UEBA
B. DLP
C. NAC
D. EDR
-
Question 763:
A security operations manager wants some recommendations for improving security monitoring. The security team currently uses past events to create an IoC list for monitoring. Which of the following is the best suggestion for improving monitoring capabilities?
A. Update the IPS and IDS with the latest rule sets from the provider.
B. Create an automated script to update the IPS and IDS rule sets.
C. Use an automated subscription to select threat feeds for IDS.
D. Implement an automated malware solution on the IPS.
-
Question 764:
Which of the following is a reason for correctly identifying APTs that might be targeting an organization?
A. APTs’ passion for social justice will make them ongoing and motivated attackers.
B. APTs utilize methods and technologies differently than other threats.
C. APTs are primarily focused on financial gain and are widely available over the internet.
D. APTs lack sophisticated methods, but their dedication makes them persistent.
-
Question 765:
A large company wants to address frequent outages on critical systems with a secure configurations program. The Chief Information Security Officer (CISO) has asked the analysts to conduct research and make recommendations for a cost-effective solution with the least amount of disruption to the business. Which of the following would be the best way to achieve these goals?
A. Adopt the CIS security controls as a framework, apply configurations to all assets, and then notify asset owners of the change.
B. Coordinate with asset owners to assess the impact of the CIS critical security controls, perform testing, and then implement across the enterprise.
C. Recommend multiple security controls depending on business unit needs, and then apply configurations according to the organization's risk tolerance.
D. Ask asset owners which configurations they would like, compile the responses, and then present all options to the CISO for approval to implement.
-
Question 766:
A Chief Information Security Officer is concerned that contract developers may be able to steal the code used to design the company's latest application since they are able to pull code from a cloud-based repository directly to laptops that are not owned by the company. Which of the following solutions would best protect the company code from being stolen?
A. MDM
B. SCA
C. CASB
D. VDI
-
Question 767:
The SFTP server logs show thousands of failed login attempts from hundreds of IP addresses worldwide. Which of the following controls would BEST protect the service?
A. Whitelisting authorized IP addresses
B. Blacklisting unauthorized IP addresses
C. Enforcing more complex password requirements
D. Establishing a sinkhole service
-
Question 768:
A security operations manager wants to build out an internal threat-hunting capability. Which of the following should be the first priority when creating a threat-hunting program?
A. Establishing a hypothesis about which threats are targeting which systems
B. Profiling common threat actors and activities to create a list of IOCs
C. Ensuring logs are sent to a centralized location with search and filtering capabilities
D. Identifying critical assets that will be used to establish targets for threat-hunting activities
-
Question 769:
A security analyst is reviewing the logs and notices the following entries:
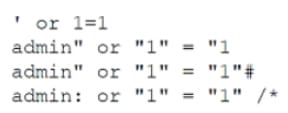
Which of the following most likely occurred?
A. LDAP injection
B. Clickjacking
C. XSS
D. SQLi
-
Question 770:
After running the cat file01.bin | hexdump -C command, a security analyst reviews the following output snippet: Which of the following digital-forensics techniques is the analyst using?

A. Reviewing the file hash
B. Debugging the binary file
C. Implementing file carving
D. Verifying the file type
E. Utilizing reverse engineering
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.