Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jul 07, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 341:
Policy allows scanning of vulnerabilities during production hours, but production servers have been crashing lately due to unauthorized scans performed by junior technicians. Which of the following is the BEST solution to avoid production server downtime due to these types of scans?
A. Transition from centralized to agent-based scans.
B. Require vulnerability scans be performed by trained personnel.
C. Configure daily-automated detailed vulnerability reports.
D. Implement sandboxing to analyze the results of each scan.
E. Scan only as required for regulatory compliance.
-
Question 342:
Several accounting department users are reporting unusual Internet traffic in the browsing history of their workstations after returning to work and logging in. The building security team informs the IT security team that the cleaning staff was caught using the systems after the accounting department users left for the day. Which of the following steps should the IT security team take to help prevent this from happening again? (Choose two.)
A. Install a web monitor application to track Internet usage after hours.
B. Configure a policy for workstation account timeout at three minutes.
C. Configure NAC to set time-based restrictions on the accounting group to normal business hours.
D. Configure mandatory access controls to allow only accounting department users to access the workstations.
E. Set up a camera to monitor the workstations for unauthorized use.
-
Question 343:
On which of the following organizational resources is the lack of an enabled password or PIN a common vulnerability?
A. VDI systems
B. Mobile devices
C. Enterprise server Oss
D. VPNs
E. VoIP phones
-
Question 344:
The development team currently consists of three developers who each specialize in a specific programming language:
Developer 1 ?C++/C# Developer 2 ?Python Developer 3 ?Assembly
Which of the following SDLC best practices would be challenging to implement with the current available staff?
A. Fuzzing
B. Peer review
C. Regression testing
D. Stress testing
-
Question 345:
A security analyst determines that several workstations are reporting traffic usage on port 3389. All workstations are running the latest OS patches according to patch reporting. The help desk manager reports some users are getting logged off of their workstations, and network access is running slower than normal. The analyst believes a zero-day threat has allowed remote attackers to gain access to the workstations. Which of the following are the BEST steps to stop the threat without impacting all services? (Choose two.)
A. Change the public NAT IP address since APTs are common.
B. Configure a group policy to disable RDP access.
C. Disconnect public Internet access and review the logs on the workstations.
D. Enforce a password change for users on the network.
E. Reapply the latest OS patches to workstations.
F. Route internal traffic through a proxy server.
-
Question 346:
A security analyst was asked to join an outage call for a critical web application. The web middleware support team determined the web server is running and having no trouble processing requests; however, some investigation has revealed firewall denies to the web server that began around 1.00 a.m. that morning. An emergency change was made to enable the access, but management has asked for a root cause determination. Which of the following would be the BEST next step?
A. Install a packet analyzer near the web server to capture sample traffic to find anomalies.
B. Block all traffic to the web server with an ACL.
C. Use a port scanner to determine all listening ports on the web server.
D. Search the logging servers for any rule changes.
-
Question 347:
Which of the allowing is a best practice with regard to interacting with the media during an incident?
A. Allow any senior management level personnel with knowledge of the incident to discuss it.
B. Designate a single port of contact and at least one backup for contact with the media.
C. Stipulate that incidents are not to be discussed with the media at any time during the incident.
D. Release financial information on the impact of damages caused by the incident.
-
Question 348:
During a recent audit, there were a lot of findings similar to and including the following:
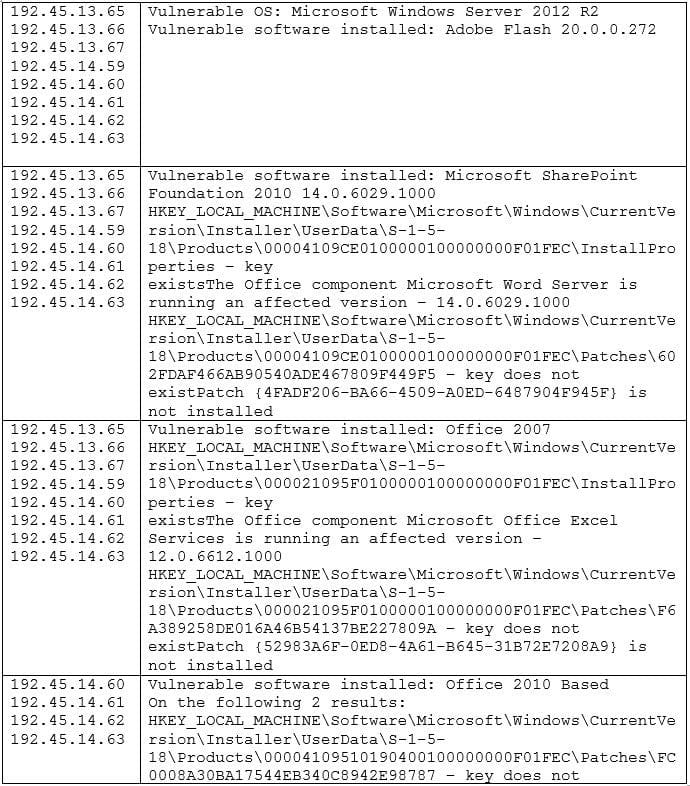
Which of the following would be the BEST way to remediate these findings and minimize similar findings in the future?
A. Use an automated patch management solution.
B. Remove the affected software programs from the servers.
C. Run Microsoft Baseline Security Analyzer on all of the servers.
D. Schedule regular vulnerability scans for all servers on the network.
-
Question 349:
The Chief Information Security Officer (CISO) asks a security analyst to write a new SIEM search rule to determine if any credit card numbers are being written to log files. The CISO and security analyst suspect the following log snippet contains real customer card data:
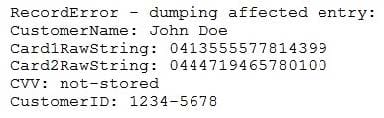
Which of the following expressions would find potential credit card numbers in a format that matches the log snippet?
A. ^[0-9](16)$
B. (0-9) x 16
C. "1234-5678"
D. "04*"
-
Question 350:
A security analyst is preparing for the company's upcoming audit. Upon review of the company's latest vulnerability scan, the security analyst finds the following open issues: Which of the following vulnerabilities should be prioritized for remediation FIRST?
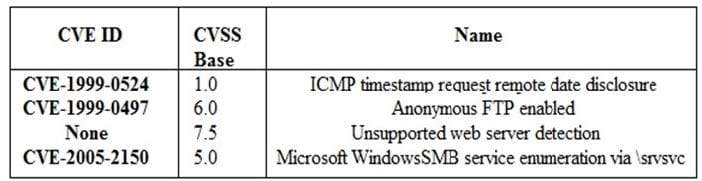
A. ICMP timestamp request remote date disclosure
B. Anonymous FTP enabled
C. Unsupported web server detection
D. Microsoft Windows SMB service enumeration via \srvsvc
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.