Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jun 29, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 21:
A security analyst needs to develop a brief that will include the latest incidents and the attack phases of the incidents. The goal is to support threat intelligence and identify whether or not the incidents are linked. Which of the following methods would be MOST appropriate to use?
A. An adversary capability model
B. The MITRE ATTandCK framework
C. The Cyber Kill Chain
D. The Diamond Model of Intrusion Analysis
-
Question 22:
A security analyst reviews the latest reports from the company's vulnerability scanner and discovers the following:
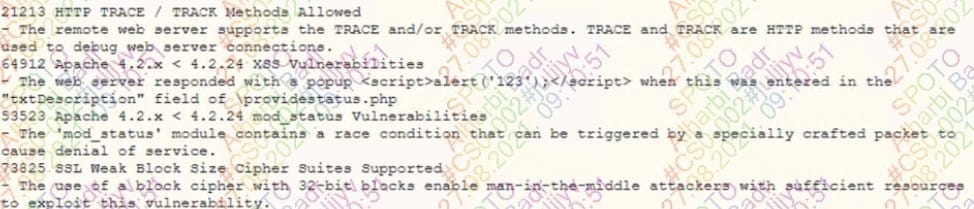
Which of the following changes should the analyst recommend FIRST?
A. Configuring SSL ciphers to use different encryption blocks
B. Programming changes to encode output
C. Updating the 'mod_status' module
D. Disabling HTTP connection debugging commands
-
Question 23:
A security analyst inspects the header of an email that is presumed to be malicious and sees the following:
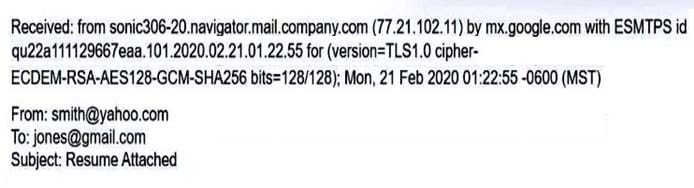
Which of the following is inconsistent with the rest of the header and should be treated as suspicious?
A. The subject line
B. The sender's email address
C. The destination email server
D. The use of a TLS cipher
-
Question 24:
In web application scanning, static analysis refers to scanning:
A. the system for vulnerabilities before installing the application.
B. the compiled code of the application to detect possible issues.
C. an application that is installed and active on a system.
D. an application that is installed on a system that is assigned a static IP.
-
Question 25:
An organization has the following risk mitigation policy:
1.
Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
2.
All other prioritization will be based on risk value. The organization has identified the following risks:
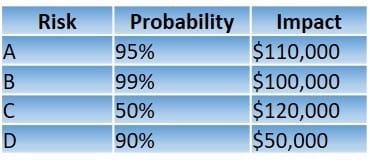
Which of the following is the order of priority for risk mitigation from highest to lowest?
A. A, B, D, C
B. A, B, C, D
C. D, A, B, C
D. D, A, C, B
-
Question 26:
A security analyst receives an alert to expect increased and highly advanced cyberattacks originating from a foreign country that recently had sanctions implemented. Which of the following describes the type of threat actors that should concern the security analyst?
A. Insider threat
B. Nation-state
C. Hacktivist
D. Organized crime
-
Question 27:
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization: Which of the following technologies would MOST likely be used to prevent this phishing attempt?
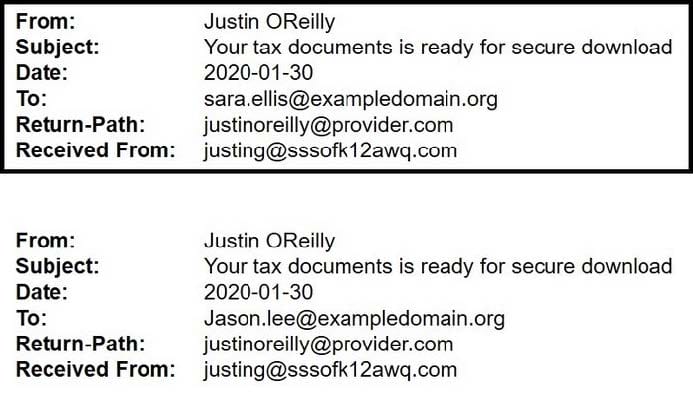
A. DNSSEC
B. DMARC
C. STP
D. S/IMAP
-
Question 28:
A small business does not have enough staff in the accounting department to segregate duties. The controller writes the checks for the business and reconciles them against the ledger. To ensure there is no fraud occurring, the business conducts quarterly reviews in which a different officer in the business compares all the cleared checks against the ledger. Which of the following BEST describes this type of control?
A. Deterrent
B. Preventive
C. Compensating
D. Detective
-
Question 29:
While reviewing a cyber-risk assessment, an analyst notes there are concerns related to FPGA usage. Which of the following statements would BEST convince the analyst's supervisor to use additional controls?
A. FPGAs are expensive and can only be programmed once. Code deployment safeguards are needed.
B. FPGAs have an inflexible architecture. Additional training for developers is needed.
C. FPGAs are vulnerable to malware installation and require additional protections for their codebase.
D. FPGAs are expensive to produce. Anti-counterfeiting safeguards are needed.
-
Question 30:
A company's security officer needs to implement geographical IP blocks for nation-state actors from a foreign country. On which of the following should the blocks be implemented?
A. Data loss prevention
B. Network access control
C. Access control list
D. Web content filter
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.