Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Jun 29, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 111:
When investigating a compromised system, a security analyst finds the following script in the /tmp directory:
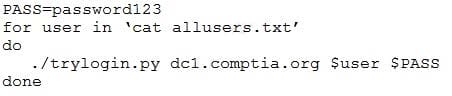
Which of the following attacks is this script attempting, and how can it be mitigated?
A. This is a password-hijacking attack, and it can be mitigated by using strong encryption protocols.
B. This is a password-spraying attack, and it can be mitigated by using multifactor authentication.
C. This is a password-dictionary attack, and it can be mitigated by forcing password changes every 30 days.
D. This is a credential-stuffing attack, and it can be mitigated by using multistep authentication.
-
Question 112:
Which of the following sources will provide the MOST relevant threat intelligence data to the security team of a dental care network?
A. H-ISAC
B. Dental forums
C. Open threat exchange
D. Dark web chatter
-
Question 113:
A company has contracted with a software development vendor to design a web portal for customers to access a medical records database. Which of the following should the security analyst recommend to BEST control the unauthorized disclosure of sensitive data when sharing the development database with the vendor?
A. Establish an NDA with the vendor.
B. Enable data masking of sensitive data tables in the database.
C. Set all database tables to read only.
D. Use a de-identified data process for the development database.
-
Question 114:
A security analyst receives an alert from the SIEM about a possible attack happening on the network. The analyst opens the alert and sees the IP address of the suspected server as 192.168.54.66, which is part of the network 192.168.54.0/24. The analyst then pulls all the command history logs from that server and sees the following:
$ route -n $ ifconfig -a $ ping 192.168.54.1 $ tcpdump 192.168.54.80 -nns $ hping -s 192.168.54.80 -c 3
Which of the following activities is MOST likely happening on the server?
A. A vulnerability scan
B. Enumeration
C. Fuzzing
D. A MITM attack
-
Question 115:
A security analyst wants to capture large amounts of network data that will be analyzed at a later time. The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called "packetCapture". The capture must be as efficient as possible, and the analyst wants to minimize the likelihood that packets will be missed. Which of the following commands will BEST accomplish the analyst's objectives?
A. tcpdump -w packetCapture
B. tcpdump -a packetCapture
C. tcpdump -n packetCapture
D. nmap -v > packetCapture
E. nmap -oA > packetCapture
-
Question 116:
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verify that a user's data is not altered without the user's consent. Which of the following would be an appropriate course of action?
A. Automate the use of a hashing algorithm after verified users make changes to their data.
B. Use encryption first and then hash the data at regular, defined times.
C. Use a DLP product to monitor the data sets for unauthorized edits and changes.
D. Replicate the data sets at regular intervals and continuously compare the copies for unauthorized changes.
-
Question 117:
An organization is experiencing issues with emails that are being sent to external recipients. Incoming emails to the organization are working fine. A security analyst receives the following screenshot of an email error from the help desk:
Mail delivery failed: Returning message to sender A message could not be delivered to one or more of its recipients SMTP Error from remote mail server after RCPT To: [email protected]
The analyst then checks the email server and sees many of the following messages in the logs:
Error 550 - Message rejected
Which of the following is MOST likely the issue?
A. SPF is failing.
B. The DMARC queue is full.
C. The DKIM private key has expired.
D. Port 25 is not open.
-
Question 118:
A company's data is still being exfiltered to business competitors after the implementation of a DLP solution. Which of the following is the most likely reason why the data is still being compromised?
A. Printed reports from the database contain sensitive information
B. DRM must be implemented with the DLP solution
C. Users are not labeling the appropriate data sets
D. DLP solutions are only effective when they are implemented with disk encryption
-
Question 119:
An information security analyst discovered a virtual machine server was compromised by an attacker. Which of the following should be the FIRST step to confirm and respond to the incident?
A. Pause the virtual machine,
B. Shut down the virtual machine.
C. Take a snapshot of the virtual machine.
D. Remove the NIC from the virtual machine.
E. Review host hypervisor log of the virtual machine.
F. Execute a migration of the virtual machine.
-
Question 120:
A cybersecurity analyst is investigating a potential incident affecting multiple systems on a company's internal network. Although there is a negligible impact to performance, the following symptoms are present on each of the affected systems:
1.
Existence of a new and unexpected svchost.exe process
2.
Persistent, outbound TCP/IP connections to an unknown external host with routine keep-alives transferred
3.
DNS query logs showing successful name resolution for an Internet-resident dynamic DNS domain
If this situation remains unresolved, which of the following will MOST likely occur?
A. The affected hosts may participate in a coordinated DDoS attack upon command
B. An adversary may leverage the affected hosts to reconfigure the company's router ACLs
C. Key files on the affected hosts may become encrypted and require ransom payment for unlock
D. The adversary may attempt to perform a man-in-the-middle attack
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.