Exam Details
Exam Code
:350-401Exam Name
:Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)Certification
:CCIE Enterprise WirelessVendor
:CiscoTotal Questions
:1457 Q&AsLast Updated
:Jul 02, 2025
Cisco CCIE Enterprise Wireless 350-401 Questions & Answers
-
Question 1061:
Refer to the exhibit.

An engineer is troubleshooting a connectivity issue and executes a traceoute. What does the result confirm?
A. The destination server reported it is too busy
B. The protocol is unreachable
C. The destination port is unreachable
D. The probe timed out
-
Question 1062:
An engineer runs the code against an API of Cisco DMA Center, and the platform returns this output What does the response indicate?
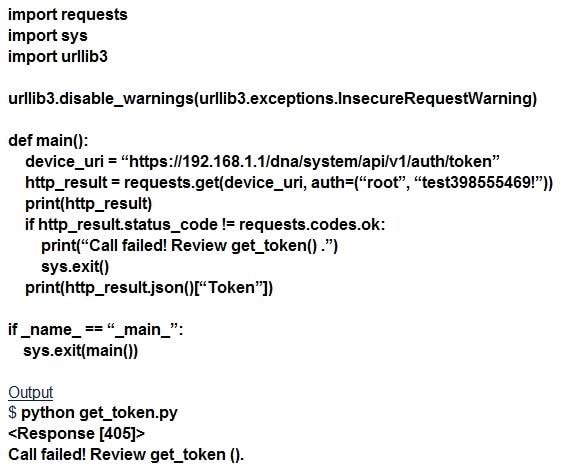
A. The authentication credentials are incorrect.
B. The URl string is incorrect.
C. The Cisco DNA Center API port is incorrect.
D. The HTTP method is incorrect.
-
Question 1063:
What is a consideration when designing a Cisco SD-Access underlay network?
A. End user subnets and endpoints are part of the underlay network.
B. The underlay switches provide endpoint physical connectivity for users.
C. Static routing is a requirement,
D. It must support IPv4 and IPv6 underlay networks.
-
Question 1064:
In a wireless Cisco SD-Access deployment, which roaming method is used when a user moves from one access point to another on a different access switch using a single WLC?
A. Layer 3
B. inter-xTR
C. auto anchor
D. fast roam
-
Question 1065:
How is Layer 3 roaming accomplished in a unified wireless deployment?
A. An EoIP tunnel is created between the client and the anchor controller to provide seamless connectivity as the client is associated with the new AP.
B. The client entry on the original controller is passed to the database on the new controller.
C. The new controller assigns an IP address from the new subnet to the client
D. The client database on the original controller is updated the anchor entry, and the new controller database is updated with the foreign entry.
-
Question 1066:
Which features does Cisco EDR use to provide threat detection and response protection?
A. containment, threat intelligence, and machine learning
B. firewalling and intrusion prevention
C. container-based agents
D. cloud analysis and endpoint firewall controls
-
Question 1067:
Which design principle slates that a user has no access by default to any resource, and unless a resource is explicitly granted, it should be denied?
A. least privilege
B. fail-safe defaults
C. economy of mechanism
D. complete mediation
-
Question 1068:
Which measurement is used from a post wireless survey to depict the cell edge of the access points?
A. SNR
B. Noise
C. RSSI
D. CCI
-
Question 1069:
Refer to the exhibit.

After configurating an IPsec VPN, an engineer enters the show command to verify the ISAKMP SA status. What does the status show?
A. ISAKMP SA is authenticated and can be used for Quick Mode.
B. Peers have exchanged keys, but ISAKMP SA remains unauthenticated.
C. VPN peers agreed on parameters for the ISAKMP SA
D. ISAKMP SA has been created, but it has not continued to form.
-
Question 1070:
Which entity is a Type 1 hypervisor?
A. Oracle VM VirtualBox
B. VMware server
C. Citrix XenServer
D. Microsoft Virtual PC
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-401 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.