Exam Details
Exam Code
:312-50V8Exam Name
:Certified Ethical Hacker v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1008 Q&AsLast Updated
:Jul 08, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V8 Questions & Answers
-
Question 21:
RC4 is known to be a good stream generator. RC4 is used within the WEP standard on wireless LAN. WEP is known to be insecure even if we are using a stream cipher that is known to be secured.
What is the most likely cause behind this?
A. There are some flaws in the implementation.
B. There is no key management.
C. The IV range is too small.
D. All of the above.
E. None of the above.
-
Question 22:
Look at the following SQL query.
SELECT * FROM product WHERE PCategory='computers' or 1=1--'
What will it return? Select the best answer.
A. All computers and all 1's
B. All computers
C. All computers and everything else
D. Everything except computers
-
Question 23:
Sandra is conducting a penetration test for XYZ.com. She knows that XYZ.com is using wireless networking for some of the offices in the building right down the street. Through social engineering she discovers that they are using 802.11g. Sandra knows that 802.11g uses the same 2.4GHz frequency range as 802.11b. Using NetStumbler and her 802.11b wireless NIC, Sandra drives over to the building to map the wireless networks. However, even though she repositions herself around the building several times, Sandra is not able to detect a single AP.
What do you think is the reason behind this?
A. Netstumbler does not work against 802.11g.
B. You can only pick up 802.11g signals with 802.11a wireless cards.
C. The access points probably have WEP enabled so they cannot be detected.
D. The access points probably have disabled broadcasting of the SSID so they cannot be detected.
E. 802.11g uses OFDM while 802.11b uses DSSS so despite the same frequency and 802.11b card cannot see an 802.11g signal.
F. Sandra must be doing something wrong,as there is no reason for her to not see the signals.
-
Question 24:
Bill is attempting a series of SQL queries in order to map out the tables within the database that he is trying to exploit.
Choose the attack type from the choices given below.
A. Database Fingerprinting
B. Database Enumeration
C. SQL Fingerprinting
D. SQL Enumeration
-
Question 25:
Exhibit:
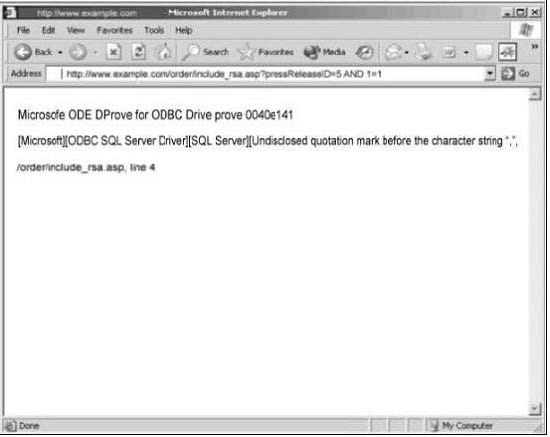
You are conducting pen-test against a company's website using SQL Injection techniques.
You enter "anuthing or 1=1-" in the username filed of an authentication form. This is the output returned from the server.
What is the next step you should do?
A. Identify the user context of the web application by running_ http://www.example.com/order/include_rsa_asp?pressReleaseID=5 AND USER_NAME() = `dbo'
B. Identify the database and table name by running:
http://www.example.com/order/include_rsa.asp?pressReleaseID=5
AND
ascii(lower(substring((SELECT TOP 1 name FROM sysobjects WHERE
xtype='U'),1))) > 109
C. Format the C: drive and delete the database by running: http://www.example.com/order/include_rsa.asp?pressReleaseID=5 AND xp_cmdshell `format c: /q /yes `; drop database myDB; -
D. Reboot the web server by running: http://www.example.com/order/include_rsa.asp?pressReleaseID=5 AND xp_cmdshell `iisreset eboot'; -
-
Question 26:
Your boss Tess King is attempting to modify the parameters of a Web-based application in order to alter the SQL statements that are parsed to retrieve data from the database.
What would you call such an attack?
A. SQL Input attack
B. SQL Piggybacking attack
C. SQL Select attack
D. SQL Injection attack
-
Question 27:
When a malicious hacker identifies a target and wants to eventually compromise this target, what would be among the first steps that he would perform? (Choose the best answer)
A. Cover his tracks by eradicating the log files and audit trails.
B. Gain access to the remote computer in order to conceal the venue of attacks.
C. Perform a reconnaissance of the remote target for identical of venue of attacks.
D. Always begin with a scan in order to quickly identify venue of attacks.
-
Question 28:
A particular database threat utilizes a SQL injection technique to penetrate a target system.
How would an attacker use this technique to compromise a database?
A. An attacker uses poorly designed input validation routines to create or alter SQL commands to gain access to unintended data or execute commands of the database
B. An attacker submits user input that executes an operating system command to compromise a target system
C. An attacker gains control of system to flood the target system with requests,preventing legitimate users from gaining access
D. An attacker utilizes an incorrect configuration that leads to access with higher-than-expected privilege of the database
-
Question 29:
Which of the following is the best way an attacker can passively learn about technologies used in an organization?
A. By sending web bugs to key personnel
B. By webcrawling the organization web site
C. By searching regional newspapers and job databases for skill sets technology hires need to possess in the organization
D. By performing a port scan on the organization's web site
-
Question 30:
Which of the following is most effective against passwords? Select the Answer:
A. Dictionary Attack
B. BruteForce attack
C. Targeted Attack
D. Manual password Attack
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.