Exam Details
Exam Code
:312-50V7Exam Name
:Ethical Hacking and Countermeasures (CEHv7)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:514 Q&AsLast Updated
:Jun 14, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V7 Questions & Answers
-
Question 161:
What is a successful method for protecting a router from potential smurf attacks?
A. Placing the router in broadcast mode
B. Enabling port forwarding on the router
C. Installing the router outside of the network's firewall
D. Disabling the router from accepting broadcast ping messages
-
Question 162:
Which of the following tools will scan a network to perform vulnerability checks and compliance auditing?
A. NMAP
B. Metasploit
C. Nessus
D. BeEF
-
Question 163:
The use of technologies like IPSec can help guarantee the followinG. authenticity, integrity, confidentiality and
A. non-repudiation.
B. operability.
C. security.
D. usability.
-
Question 164:
A security administrator notices that the log file of the company`s webserver contains suspicious entries:
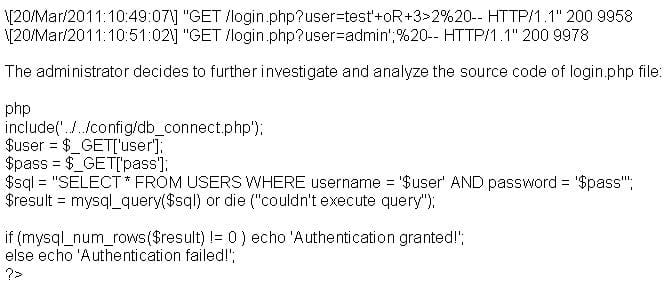
Based on source code analysis, the analyst concludes that the login.php script is vulnerable to
A. command injection.
B. SQL injection.
C. directory traversal.
D. LDAP injection.
-
Question 165:
Which of the following is a detective control?
A. Smart card authentication
B. Security policy
C. Audit trail
D. Continuity of operations plan
-
Question 166:
A penetration tester is attempting to scan an internal corporate network from the internet without alerting the border sensor. Which is the most efficient technique should the tester consider using?
A. Spoofing an IP address
B. Tunneling scan over SSH
C. Tunneling over high port numbers
D. Scanning using fragmented IP packets
-
Question 167:
A circuit level gateway works at which of the following layers of the OSI Model?
A. Layer 5 - Application
B. Layer 4 TCP
C. Layer 3 Internet protocol
D. Layer 2 Data link
-
Question 168:
Which of the following lists are valid data-gathering activities associated with a risk assessment?
A. Threat identification, vulnerability identification, control analysis
B. Threat identification, response identification, mitigation identification
C. Attack profile, defense profile, loss profile
D. System profile, vulnerability identification, security determination
-
Question 169:
What is the purpose of conducting security assessments on network resources?
A. Documentation
B. Validation
C. Implementation
D. Management
-
Question 170:
A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank's DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank's job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank's corporate office. What phase of the penetration test is the tester currently in?
A. Information reporting
B. Vulnerability assessment
C. Active information gathering
D. Passive information gathering
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V7 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.