Exam Details
Exam Code
:312-50V12Exam Name
:EC-Council Certified Ethical Hacker (C|EH v12)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:596 Q&AsLast Updated
:Jun 28, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V12 Questions & Answers
-
Question 381:
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days. Bob denies that he had ever sent a mail. What do you want to "know" to prove yourself that it was Bob who had send a mail?
A. Authentication
B. Confidentiality
C. Integrity
D. Non-Repudiation
-
Question 382:
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
A. Presentation tier
B. Application Layer
C. Logic tier
D. Data tier
-
Question 383:
Which service in a PKI will vouch for the identity of an individual or company?
A. KDC
B. CR
C. CBC
D. CA
-
Question 384:
Which of the following is a passive wireless packet analyzer that works on Linux-based systems?
A. Burp Suite
B. OpenVAS
C. tshark
D. Kismet
-
Question 385:
What is correct about digital signatures?
A. A digital signature cannot be moved from one signed document to another because it is the hash of the original document encrypted with the private key of the signing party.
B. Digital signatures may be used in different documents of the same type.
C. A digital signature cannot be moved from one signed document to another because it is a plain hash of the document content.
D. Digital signatures are issued once for each user and can be used everywhere until they expire.
-
Question 386:
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all.
Here is a section of the Virus code:
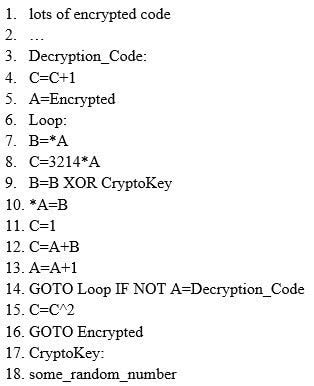
What is this technique called?
A. Polymorphic Virus
B. Metamorphic Virus
C. Dravidic Virus
D. Stealth Virus
-
Question 387:
If executives are found liable for not properly protecting their company's assets and information systems, what type of law would apply in this situation?
A. Criminal
B. International
C. Common
D. Civil
-
Question 388:
Clark is a professional hacker. He created and configured multiple domains pointing to the same host to switch quickly between the domains and avoid detection. Identify the behavior of the adversary In the above scenario.
A. use of command-line interface
B. Data staging
C. Unspecified proxy activities
D. Use of DNS tunneling
-
Question 389:
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host 10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he applied his ACL configuration in the router, nobody can access the ftp, and the permitted hosts cannot access the Internet. According to the next configuration, what is happening in the network?
access-list 102 deny tcp any any access-list 104 permit udp host 10.0.0.3 any access-list 110 permit tcp host 10.0.0.2 eq www any access-list 108 permit tcp any eq ftp any
A. The ACL 104 needs to be first because is UDP
B. The first ACL is denying all TCP traffic and the other ACLs are being ignored by the router
C. The ACL for FTP must be before the ACL 110
D. The ACL 110 needs to be changed to port 80
-
Question 390:
John, a professional hacker, performs a network attack on a renowned organization and gains unauthorized access to the target network. He remains in the network without being detected for a long time and obtains sensitive information without sabotaging the organization. Which of the following attack techniques is used by John?
A. Advanced persistent
B. threat Diversion theft
C. Spear-phishing sites
D. insider threat
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V12 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.