Exam Details
Exam Code
:312-50V12Exam Name
:EC-Council Certified Ethical Hacker (C|EH v12)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:596 Q&AsLast Updated
:Jul 23, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V12 Questions & Answers
-
Question 401:
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
A. USER, NICK
B. LOGIN, NICK
C. USER, PASS
D. LOGIN, USER
-
Question 402:
Judy created a forum, one day. she discovers that a user is posting strange images without writing comments. She immediately calls a security expert, who discovers that the following code is hidden behind those images:
What issue occurred for the users who clicked on the image?
A. The code inject a new cookie to the browser.
B. The code redirects the user to another site.
C. The code is a virus that is attempting to gather the users username and password.
D. This php file silently executes the code and grabs the users session cookie and session ID.
-
Question 403:
From the following table, identify the wrong answer in terms of Range (ft). Standard Range (ft) 802.11a 150-150 802.11b 150-150 802.11g 150-150
802.16 (WiMax) 30 miles
A. 802.16 (WiMax)
B. 802.11g
C. 802.11b
D. 802.11a
-
Question 404:
Consider the following Nmap output:
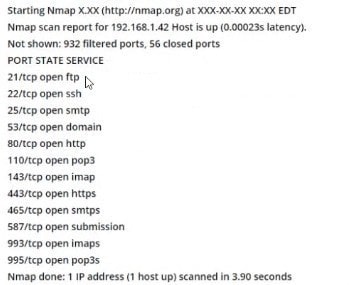
What command-line parameter could you use to determine the type and version number of the web server?
A. -sv B. -Pn
C. -V
D. -ss
-
Question 405:
Which of the following is the BEST way to defend against network sniffing?
A. Using encryption protocols to secure network communications
B. Register all machines MAC Address in a Centralized Database
C. Use Static IP Address
D. Restrict Physical Access to Server Rooms hosting Critical Servers
-
Question 406:
Attacker Steve targeted an organization's network with the aim of redirecting the company's web traffic to another malicious website. To achieve this goal, Steve performed DNS cache poisoning by exploiting the vulnerabilities in the DNS
server software and modified the original IP address of the target website to that of a fake website. What is the technique employed by Steve to gather information for identity theft?
A. Pretexting
B. Pharming
C. Wardriving
D. Skimming
-
Question 407:
A zone file consists of which of the following Resource Records (RRs)?
A. DNS, NS, AXFR, and MX records
B. DNS, NS, PTR, and MX records
C. SOA, NS, AXFR, and MX records
D. SOA, NS, A, and MX records
-
Question 408:
A "Server-Side Includes" attack refers to the exploitation of a web application by injecting scripts in HTML pages or executing arbitrary code remotely. Which web-page file type, if it exists on the web server, is a strong indication that the server is vulnerable to this kind of attack?
A. .stm
B. .html
C. .rss
D. .cms
-
Question 409:
One of your team members has asked you to analyze the following SOA record. What is the version? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.) (Choose four.)
A. 200303028
B. 3600
C. 604800
D. 2400
E. 60
F. 4800
-
Question 410:
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?
A. har.txt
B. SAM file
C. wwwroot
D. Repair file
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V12 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.