Exam Details
Exam Code
:312-50V12Exam Name
:EC-Council Certified Ethical Hacker (C|EH v12)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:596 Q&AsLast Updated
:Jun 04, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50V12 Questions & Answers
-
Question 161:
Peter is surfing the internet looking for information about DX Company. Which hacking process is Peter doing?
A. Scanning
B. Footprinting
C. Enumeration
D. System Hacking
-
Question 162:
Which of the following provides a security professional with most information about the system's security posture?
A. Phishing, spamming, sending trojans
B. Social engineering, company site browsing tailgating
C. Wardriving, warchalking, social engineering
D. Port scanning, banner grabbing service identification
-
Question 163:
Susan, a software developer, wants her web API to update other applications with the latest information. For this purpose, she uses a user-defined HTTP tailback or push APIs that are raised based on trigger events: when invoked, this
feature supplies data to other applications so that users can instantly receive real-time Information.
Which of the following techniques is employed by Susan?
A. web shells
B. Webhooks
C. REST API
D. SOAP API
-
Question 164:
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
A. [inurl:]
B. [related:]
C. [info:]
D. [site:]
-
Question 165:
Abel, a security professional, conducts penetration testing in his client organization to check for any security loopholes. He launched an attack on the DHCP servers by broadcasting forged DHCP requests and leased all the DHCP addresses available in the DHCP scope until the server could not issue any more IP addresses. This led to a Dos attack, and as a result, legitimate employees were unable to access the clients network. Which of the following attacks did Abel perform in the above scenario?
A. VLAN hopping
B. DHCP starvation
C. Rogue DHCP server attack
D. STP attack
-
Question 166:
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below. What conclusions can be drawn based on these scan results?
TCP port 21 no response TCP port 22 no response TCP port 23 Time-to-live exceeded
A. The lack of response from ports 21 and 22 indicate that those services are not running on the destination server.
B. The scan on port 23 was able to make a connection to the destination host prompting the firewall to respond with a TTL error.
C. The scan on port 23 passed through the filtering device. This indicates that port 23 was not blocked at the firewall.
D. The firewall itself is blocking ports 21 through 23 and a service is listening on port 23 of the target host.
-
Question 167:
What hacking attack is challenge/response authentication used to prevent?
A. Replay attacks
B. Scanning attacks
C. Session hijacking attacks
D. Password cracking attacks
-
Question 168:
Why is a penetration test considered to be more thorough than vulnerability scan?
A. Vulnerability scans only do host discovery and port scanning by default.
B. A penetration test actively exploits vulnerabilities in the targeted infrastructure, while a vulnerability scan does not typically involve active exploitation.
C. It is not ?a penetration test is often performed by an automated tool, while a vulnerability scan requires active engagement.
D. The tools used by penetration testers tend to have much more comprehensive vulnerability databases.
-
Question 169:
Chandler works as a pen-tester in an IT-firm in New York. As a part of detecting viruses in the systems, he uses a detection method where the anti-virus executes the malicious codes on a virtual machine to simulate CPU and memory
activities.
Which type of virus detection method did Chandler use in this context?
A. Heuristic Analysis
B. Code Emulation
C. Scanning
D. Integrity checking
-
Question 170:
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.
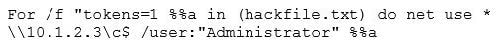
What is Eve trying to do?
A. Eve is trying to connect as a user with Administrator privileges
B. Eve is trying to enumerate all users with Administrative privileges
C. Eve is trying to carry out a password crack for user Administrator
D. Eve is trying to escalate privilege of the null user to that of Administrator
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50V12 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.