Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Aug 10, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 361:
Bob is a very security conscious computer user. He plans to test a site that is known to have malicious applets, code, and more. Bob always make use of a basic Web Browser to perform such testing. Which of the following web browser can adequately fill this purpose?
A. Internet Explorer
B. Mozila
C. Lynx
D. Tiger
-
Question 362:
Which of the following statements best describes the term Vulnerability?
A. A weakness or error that can lead to a compromise
B. An agent that has the potential to take advantage of a weakness
C. An action or event that might prejudice security
D. The loss potential of a threat.
-
Question 363:
Johnny is a member of the hacking group orpheus1. He is currently working on breaking into the Department of Defense's front end exchange server. He was able to get into the server, located in a DMZ, by using an unused service account that had a very weak password that he was able to guess. Johnny wants to crack the administrator password, but does not have a lot of time to crack it. He wants to use a tool that already has the LM hashes computed for all possible permutations of the administrator password.
What tool would be best used to accomplish this?
A. RainbowCrack
B. SMBCrack
C. SmurfCrack
D. PSCrack
-
Question 364:
Which of the following is most effective against passwords ? Select the Answer:
A. Dictionary Attack
B. BruteForce attack
C. Targeted Attack
D. Manual password Attack
-
Question 365:
You have chosen a 22 character word from the dictionary as your password. How long will it take to crack the password by an attacker?
A. 5 minutes
B. 23 days
C. 200 years
D. 16 million years
-
Question 366:
Which of the following is the best way an attacker can passively learn about technologies used in an organization?
A. By sending web bugs to key personnel
B. By webcrawling the organization web site
C. By searching regional newspapers and job databases for skill sets technology hires need to possess in the organization
D. By performing a port scan on the organization's web site
-
Question 367:
Bank of Timbukut is a medium-sized, regional financial institution in Timbuktu. The bank has deployed a new Internet-accessible Web Application recently. Customers can access their account balances, transfer money between accounts, pay bills and conduct online financial business using a web browser.
John Stevens is in charge of information security at Bank of Timbukut. After one month in production, several customers have complained about the Internet enabled banking application. Strangely, the account balances of many of the bank's customers had been changed ! However, money hasn't been removed from the bank, instead money was transferred between accounts. Given this attack profile, John Stevens reviewed the Web Application's logs and found the following entries.
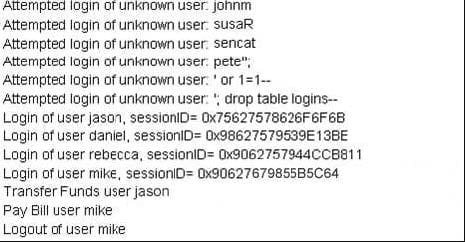
What kind of attack did the Hacker attempt to carry out at the Bank?
A. Brute Force attack in which the Hacker attempted guessing login ID and password from password cracking tools
B. The Hacker used a generator module to pass results to the Web Server and exploited Web Application CGI vulnerability.
C. The Hacker first attempted logins with suspected user names, then used SQL injection to gain access to valid login IDs
D. The Hacker attempted Session Hijacking, in which the hacker opened an account with the bank, then logged in to receive a session ID, guessed the next ID and took over Jason's session.
-
Question 368:
Look at the following SQL query.
SELECT * FROM product WHERE PCategory='computers' or 1=1--' What will it return?
Select the best answer.
A. All computers and all 1's
B. All computers
C. All computers and everything else
D. Everything except computers
-
Question 369:
What is the problem with this ASP script (login.asp)?
<% Set objConn = CreateObject("ADODB.Connection") objConn.Open Application("WebUsersConnection")
sSQL="SELECT * FROM Users where Username=? and Request("user") and _ "?and Password=? and Request("pwd") and "?
Set RS = objConn.Execute(sSQL)
If RS.EOF then Response.Redirect("login.asp?msg=Invalid Login") Else Session.Authorized = True Set RS = nothing Set objConn = nothing Response.Redirect("mainpage.asp") End If %>
A. The ASP script is vulnerable to XSS attack
B. The ASP script is vulnerable to SQL Injection attack
C. The ASP script is vulnerable to Session Splice attack
D. The ASP script is vulnerable to Cross Site Scripting attack
-
Question 370:
Identify SQL injection attack from the HTTP requests shown below:
A. http://www.victim.com/example?accountnumber=67891andcreditamount=999999999
B. http://www.xsecurity.com/cgiin/bad.cgi?foo=..%fc%80%80%80%80%af../bin/ls%20-al
C. http://www.myserver.com/search.asp?lname=smith%27%3bupdate%20usertable%20set%20passwd %3d%27hAx0r%27%3b--%00
D. http://www.myserver.com/script.php?mydata=%3cscript%20src=%22http%3a%2f %2fwww.yourserver.c0m%2fbadscript.js%22% 3e%3c%2fscript%3e
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.