Exam Details
Exam Code
:312-50Exam Name
:Certified Ethical HackerCertification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:614 Q&AsLast Updated
:Aug 10, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-50 Questions & Answers
-
Question 21:
Which of the following activities will NOT be considered as passive footprinting?
A. Go through the rubbish to find out any information that might have been discarded.
B. Search on financial site such as Yahoo Financial to identify assets.
C. Scan the range of IP address found in the target DNS database.
D. Perform multiples queries using a search engine.
-
Question 22:
User which Federal Statutes does FBI investigate for computer crimes involving e-mail scams and mail fraud?
A. 18 U.S.C 1029 Possession of Access Devices
B. 18 U.S.C 1030 Fraud and related activity in connection with computers
C. 18 U.S.C 1343 Fraud by wire, radio or television
D. 18 U.S.C 1361 Injury to Government Property
E. 18 U.S.C 1362 Government communication systems
F. 18 U.S.C 1831 Economic Espionage Act
G. 18 U.S.C 1832 Trade Secrets Act
-
Question 23:
You are footprinting Acme.com to gather competitive intelligence. You visit the acme.com websire for contact information and telephone number numbers but do not find it listed there. You know that they had the entire staff directory listed on their website 12 months ago but now it is not there. How would it be possible for you to retrieve information from the website that is outdated?
A. Visit google search engine and view the cached copy.
B. Visit Archive.org site to retrieve the Internet archive of the acme website.
C. Crawl the entire website and store them into your computer.
D. Visit the company's partners and customers website for this information.
-
Question 24:
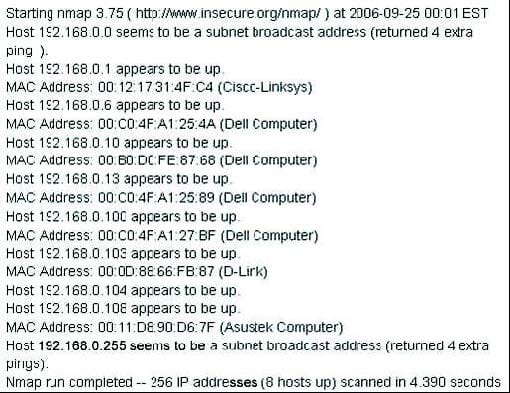
Which of the following nmap command in Linux procedures the above output?
A. sudo nmap sP 192.168.0.1/24
B. root nmap sA 192.168.0.1/24
C. run nmap TX 192.168.0.1/24
D. launch nmap PP 192.168.0.1/24
-
Question 25:
While reviewing the results of a scan run against a target network you come across the following:

What was used to obtain this output?
A. An SNMP Walk
B. Hping2 diagnosis
C. A Bo2K System query
D. Nmap protocol/port scan
-
Question 26:
You are conducting an idlescan manually using HPING2. During the scanning process, you notice that almost every query increments the IPID- regardless of the port being queried. One or two of the queries cause the IPID to increment by more than one value. Which of he following options would be a possible reason?
A. Hping2 can't be used for idlescanning
B. The Zombie you are using is not truly idle
C. These ports are actually open on the target system
D. A stateful inspection firewall is resetting your queries
-
Question 27:
Which of the following is a patch management utility that scans one or more computers on your network and alerts you if you important Microsoft Security patches are missing. It then provides links that enable those missing patches to be downloaded and installed.
A. MBSA
B. BSSA
C. ASNB
D. PMUS
-
Question 28:
Gerald, the systems administrator for Hyped Enterprise, has just discovered that his network has been breached by an outside attacker. After performing routine maintenance on his servers, his discovers numerous remote tools were installed that no one claims to have knowledge of in his department.
Gerald logs onto the management console for his IDS and discovers an unknown IP address that scanned his network constantly for a week and was able to access his network through a high-level port that was not closed. Gerald traces the IP address he found in the IDS log to proxy server in Brazil.
Gerald calls the company that owns the proxy server and after searching through their logs, they trace the source to another proxy server in Switzerland. Gerald calls the company in Switzerland that owns the proxy server and after scanning through the logs again, they trace the source back to a proxy server in China.
What tool Geralds's attacker used to cover their tracks?
A. Tor
B. ISA
C. IAS
D. Cheops
-
Question 29:
Study the log below and identify the scan type. tcpdump w host 192.168.1.10

A. nmap R 192.168.1.10
B. nmap S 192.168.1.10
C. nmap V 192.168.1.10
D. nmap sO T 192.168.1.10
-
Question 30:
Which type of scan does not open a full TCP connection?
A. Stealth Scan
B. XMAS Scan
C. Null Scan
D. FIN Scan
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-50 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.