Exam Details
Exam Code
:312-49V8Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V8)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:180 Q&AsLast Updated
:Aug 21, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V8 Questions & Answers
-
Question 21:
What document does the screenshot represent?
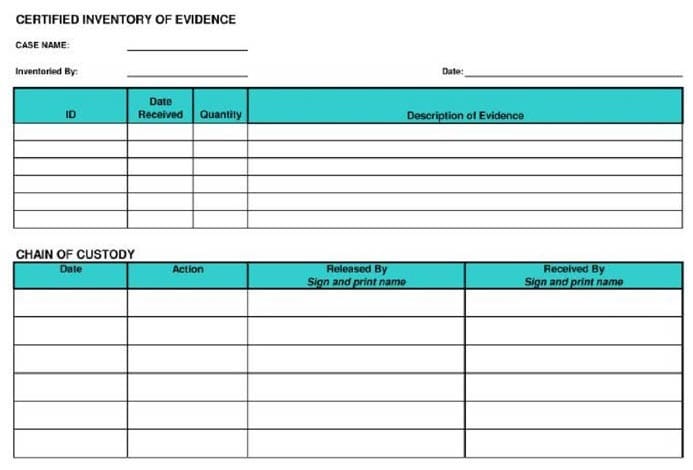
A. Chain of custody form
B. Search warrant form
C. Evidence collection form
D. Expert witness form
-
Question 22:
Which of the following standard is based on a legal precedent regarding the admissibility of scientific examinations or experiments in legal cases?
A. Daubert Standard
B. Schneiderman Standard
C. Frye Standard
D. FERPA standard
-
Question 23:
A forensic investigator is a person who handles the complete Investigation process, that is, the preservation, identification, extraction, and documentation of the evidence. The investigator has many roles and responsibilities relating to the cybercrime analysis. The role of the forensic investigator is to:
A. Take permission from all employees of the organization for investigation
B. Harden organization network security
C. Create an image backup of the original evidence without tampering with potential evidence
D. Keep the evidence a highly confidential and hide the evidence from law enforcement agencies
-
Question 24:
Which of the following is not a part of disk imaging tool requirements?
A. The tool should not change the original content
B. The tool should log I/O errors in an accessible and readable form, including the type and location of the error
C. The tool must have the ability to be held up to scientific and peer review
D. The tool should not compute a hash value for the complete bit stream copy generated from an image file of the source
-
Question 25:
How do you define Technical Steganography?
A. Steganography that uses physical or chemical means to hide the existence of a message
B. Steganography that utilizes written natural language to hide the message in the carrier in some non-obvious ways
C. Steganography that utilizes written JAVA language to hide the message in the carrier in some non-obvious ways
D. Steganography that utilizes visual symbols or signs to hide secret messages
-
Question 26:
Mobile phone forensics is the science of recovering digital evidence from a mobile phone under forensically sound conditions.
A. True
B. False
-
Question 27:
An attack vector is a path or means by which an attacker can gain access to computer or network resources in order to deliver an attack payload or cause a malicious outcome.
A. True
B. False
-
Question 28:
The need for computer forensics is highlighted by an exponential increase in the number of cybercrimes and litigations where large organizations were involved. Computer forensics plays an important role in tracking the cyber criminals. The main role of computer forensics is to:
A. Maximize the investigative potential by maximizing the costs
B. Harden organization perimeter security
C. Document monitoring processes of employees of the organization
D. Extract, process, and interpret the factual evidence so that it proves the attacker's actions in the court
-
Question 29:
What is static executable file analysis?
A. It is a process that consists of collecting information about and from an executable file without actually launching the file under any circumstances
B. It is a process that consists of collecting information about and from an executable file by launching the file under any circumstances
C. It is a process that consists of collecting information about and from an executable file without actually launching an executable file in a controlled and monitored environment
D. It is a process that consists of collecting information about and from an executable file by launching an executable file in a controlled and monitored environment
-
Question 30:
Ever-changing advancement or mobile devices increases the complexity of mobile device examinations. Which or the following is an appropriate action for the mobile forensic investigation?
A. To avoid unwanted interaction with devices found on the scene, turn on any wireless interfaces such as Bluetooth and Wi-Fi radios
B. Do not wear gloves while handling cell phone evidence to maintain integrity of physical evidence
C. If the device's display is ON. the screen's contents should be photographed and, if necessary, recorded manually, capturing the time, service status, battery level, and other displayed icons
D. If the phone is in a cradle or connected to a PC with a cable, then unplug the device from the computer
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.