Exam Details
Exam Code
:312-49V8Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V8)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:180 Q&AsLast Updated
:Aug 21, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V8 Questions & Answers
-
Question 41:
Why is it Important to consider health and safety factors in the work carried out at all stages of the forensic process conducted by the forensic analysts?
A. This is to protect the staff and preserve any fingerprints that may need to be recovered at a later date
B. All forensic teams should wear protective latex gloves which makes them look professional and cool
C. Local law enforcement agencies compel them to wear latest gloves
D. It is a part of ANSI 346 forensics standard
-
Question 42:
Which of the following commands shows you the username and IP address used to access the system via a remote login session and the Type of client from which they are accessing the system?
A. Net sessions
B. Net file
C. Net config
D. Net share
-
Question 43:
What is the first step that needs to be carried out to investigate wireless attacks?
A. Obtain a search warrant
B. Identify wireless devices at crime scene
C. Document the scene and maintain a chain of custody
D. Detect the wireless connections
-
Question 44:
All the Information about the user activity on the network, like details about login and logoff attempts, is collected in the security log of the computer. When a user's login is successful, successful audits generate an entry whereas unsuccessful audits generate an entry for failed login attempts in the logon event ID table.
In the logon event ID table, which event ID entry (number) represents a successful logging on to a computer?
A. 528
B. 529
C. 530
D. 531
-
Question 45:
Operating System logs are most beneficial for Identifying or Investigating suspicious activities involving a particular host. Which of the following Operating System logs contains information about operational actions performed by OS components?
A. Event logs
B. Audit logs
C. Firewall logs
D. IDS logs
-
Question 46:
A mobile operating system manages communication between the mobile device and other compatible devices like computers, televisions, or printers.
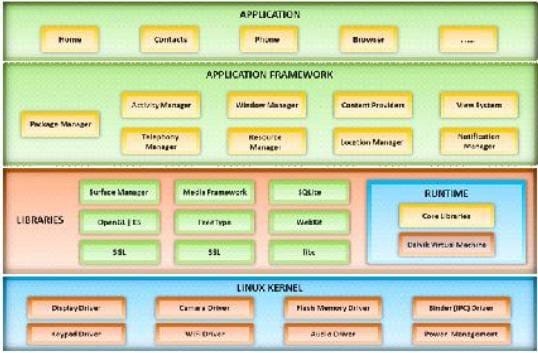
Which mobile operating system architecture is represented here?
A. webOS System Architecture
B. Symbian OS Architecture
C. Android OS Architecture
D. Windows Phone 7 Architecture
-
Question 47:
Which of the following statements is not a part of securing and evaluating electronic crime scene checklist?
A. Locate and help the victim
B. Transmit additional flash messages to other responding units
C. Request additional help at the scene if needed
D. Blog about the incident on the internet
-
Question 48:
The Apache server saves diagnostic information and error messages that it encounters while processing requests. The default path of this file is usr/local/apache/logs/error.log in Linux. Identify the Apache error log from the following logs.
A. 127.0.0.1 - frank [10/Oct/2000:13:55:36-0700] "GET /apache_pb.grf HTTP/1.0" 200 2326
B. [Wed Oct 11 14:32:52 2000] [error] [client 127.0.0.1] client denied by server configuration: /export/home/live/ap/htdocs/test
C. http://victim.com/scripts/..%c0%af./..%c0%af./..%c0%af./..%c0%af./..%c0%af./..%c0%af./.. %c0%af./..%c0%af./../winnt/system32/cmd.exe?/c+di r+c:\wintt\system32\Logfiles\W3SVC1
D. 127.0.0.1 --[10/Apr/2007:10:39:11 +0300] ] [error] "GET /apache_pb.gif HTTP/1.0' 200 2326
-
Question 49:
What is the smallest allocation unit of a hard disk?
A. Cluster
B. Spinning tracks
C. Disk platters
D. Slack space
-
Question 50:
Which one of the following statements is not correct while preparing for testimony?
A. Go through the documentation thoroughly
B. Do not determine the basic facts of the case before beginning and examining the evidence
C. Establish early communication with the attorney
D. Substantiate the findings with documentation and by collaborating with other computer forensics
professionals
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.