Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Aug 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 551:
Harold is a computer forensics investigator working for a consulting firm out of Atlanta Georgia. Harold is called upon to help with a corporate espionage case in Miami Florida. Harold assists in the investigation by pulling all the data from the computers allegedly used in the illegal activities. He finds that two suspects in the company where stealing sensitive corporate information and selling it to competing companies. From the email and instant messenger logs recovered, Harold has discovered that the two employees notified the buyers by writing symbols on the back of specific stop signs. This way, the buyers knew when and where to meet with the alleged suspects to buy the stolen material. What type of steganography did these two suspects use?
A. Text semagram
B. Visual semagram
C. Grill cipher
D. Visual cipher
-
Question 552:
To check for POP3 traffic using Ethereal, what port should an investigator search by?
A. 143
B. 25
C. 110
D. 125
-
Question 553:
Why should you never power on a computer that you need to acquire digital evidence from?
A. When the computer boots up, files are written to the computer rendering the data nclean?When the computer boots up, files are written to the computer rendering the data ?nclean
B. When the computer boots up, the system cache is cleared which could destroy evidence
C. When the computer boots up, data in the memory buffer is cleared which could destroy evidenceWhen the computer boots up, data in the memory? buffer is cleared which could destroy evidence
D. Powering on a computer has no affect when needing to acquire digital evidence from it
-
Question 554:
Where is the default location for Apache access logs on a Linux computer?
A. usr/local/apache/logs/access_log
B. bin/local/home/apache/logs/access_log
C. usr/logs/access_log
D. logs/usr/apache/access_log
-
Question 555:
What type of attack sends SYN requests to a target system with spoofed IP addresses?
A. SYN flood
B. Ping of death
C. Cross site scripting
D. Land
-
Question 556:
What is one method of bypassing a system BIOS password?
A. Removing the processor
B. Removing the CMOS battery
C. Remove all the system memoryRemove all the system? memory
D. Login to Windows and disable the BIOS password
-
Question 557:
You are called by an author who is writing a book and he wants to know how long the copyright for his book will last after he has the book published?
A. 70 years
B. The life of the author
C. The life of the author plus 70 years
D. Copyrights last forever
-
Question 558:
What is the CIDR from the following screenshot?
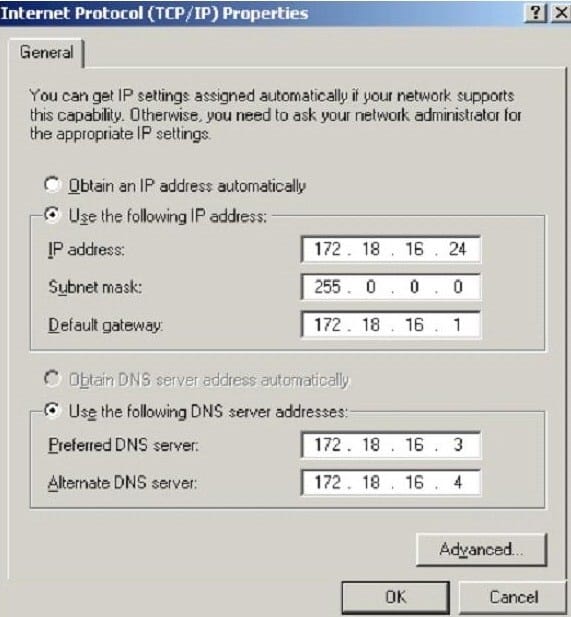
A. /24A./24A./24
B. /32 B./32 B./32
C. /16 C./16 C./16
D. /8D./8D./8
-
Question 559:
What does the acronym POST mean as it relates to a PC?
A. Power On Self Test
B. Pre Operational Situation Test
C. Primary Operating System Test
D. Primary Operations Short Test
-
Question 560:
When searching through file headers for picture file formats, what should be searched to find a JPEG file in hexadecimal format?
A. FF D8 FF E0 00 10
B. FF FF FF FF FF FF
C. FF 00 FF 00 FF 00
D. EF 00 EF 00 EF 00
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.