Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Aug 15, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 341:
Click on the Exhibit Button Paulette works for an IT security consulting company that is currently performing an audit for the firm ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible. Paulette presents the following screenshot to her boss so he can inform the client about necessary changes need to be made. From the screenshot, what changes should the client company make?
A. The banner should include the Cisco tech support contact information as well
B. The banner should have more detail on the version numbers for the networkeQuipment
C. The banner should not state "only authorized IT personnel may proceed"
D. Remove any identifying numbers, names, or version information
-
Question 342:
Under which Federal Statutes does FBI investigate for computer crimes involving e- mail scams and mail fraud?
A. 18 U.S.C. 1029 Possession of Access Devices
B. 18 U.S.C. 1030 Fraud and related activity in connection with computers
C. 18 U.S.C. 1343 Fraud by wire, radio or television
D. 18 U.S.C. 1361 Injury to Government Property
E. 18 U.S.C. 1362 Government communication systems
F. 18 U.S.C. 1831 Economic Espionage Act
G. 18 U.S.C. 1832 Trade Secrets Act
-
Question 343:
When cataloging digital evidence, the primary goal is to
A. Make bit-stream images of all hard drives
B. Preserve evidence integrity
C. Not remove the evidence from the scene
D. Not allow the computer to be turned off
-
Question 344:
Which of the following filesystem is used by Mac OS X?
A. EFS
B. HFS+
C. EXT2
D. NFS
-
Question 345:
While looking through the IIS log file of a web server, you find the following entries:
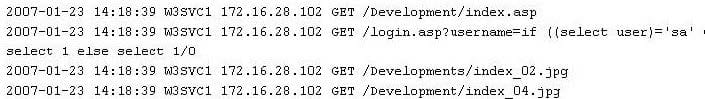
What is evident from this log file?
A. Web bugs
B. Cross site scripting
C. Hidden fields
D. SQL injection is possible
-
Question 346:
Office documents (Word, Excel, PowerPoint) contain a code that allows tracking the MAC, or unique identifier, of the machine that created the document.
What is that code called?
A. the Microsoft Virtual Machine Identifier
B. the Personal Application Protocol
C. the Globally Unique ID
D. the Individual ASCII String
-
Question 347:
Julia is a senior security analyst for Berber Consulting group. She is currently working on a contract for a small accounting firm in Florida. They have given her permission to perform social engineering attacks on the company to see if their in-house training did any good. Julia calls the main number for the accounting firm and talks to the receptionist. Julia says that she is an IT technician from the company's main office in Iowa. She states that she needs the receptionist's network username and password to troubleshoot a problem they are having. Julia says that Bill Hammond, the CEO of the company, reQuested this information. After hearing the name of the CEO, the receptionist gave Julia all the information she asked for. What principal of social engineering did Julia use?
A. Social Validation
B. Friendship/Liking
C. Reciprocation
D. Scarcity
-
Question 348:
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like routers?
A. 18 U.S.C. 1029
B. 18 U.S.C. 1362
C. 18 U.S.C. 2511
D. 18 U.S.C. 2703
-
Question 349:
The police believe that Mevin Matthew has been obtaining unauthorized access to computers belonging to numerous computer software and computer operating systems manufacturers, cellular telephone manufacturers, Internet Service Providers, and educational institutions. They also suspect that he has been stealing, copying, and misappropriating proprietary computer software belonging to the several victim companies. What is preventing the police from breaking down the suspect door and searching his home and seizing all of his computer equipment if they haveis preventing the police from breaking down the suspect? door and searching his home and seizing all of his computer equipment if they have not yet obtained a warrant?
A. The USA Patriot Act
B. The Good Samaritan Laws
C. The Federal Rules of Evidence
D. The Fourth Amendment
-
Question 350:
Area density refers to:
A. the amount of data per disk
B. the amount of data per partition
C. the amount of data per square inch
D. the amount of data per platter
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-055
Sun Certified Programmer for the Java 2 Platform.SE 5.0212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.