300-710 Exam Details
-
Exam Code
:300-710 -
Exam Name
:Securing Networks with Cisco Firepower (SNCF) -
Certification
:CCNP Security -
Vendor
:Cisco -
Total Questions
:433 Q&As -
Last Updated
:Jan 06, 2026
Cisco 300-710 Online Questions & Answers
-
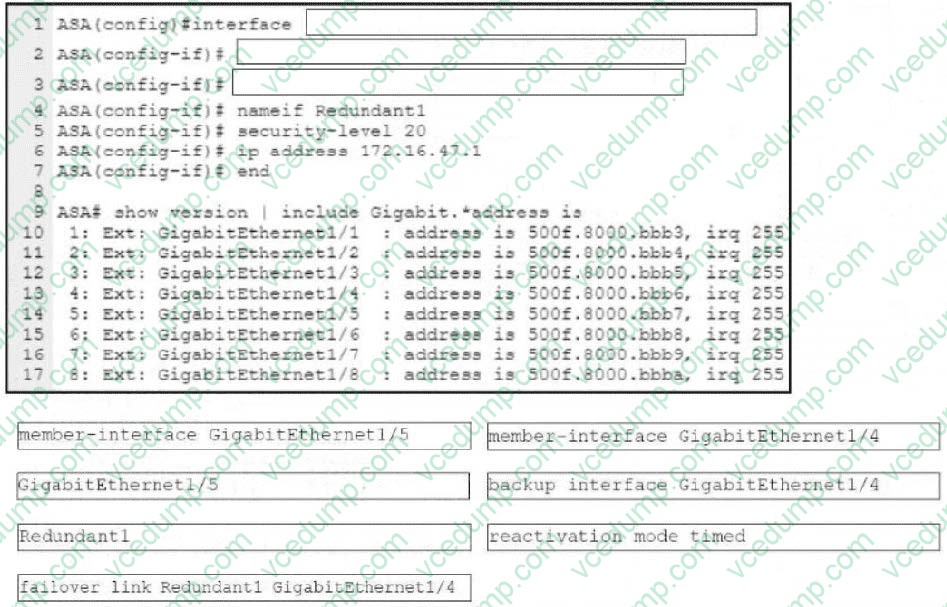
Question 1:
DRAG DROP
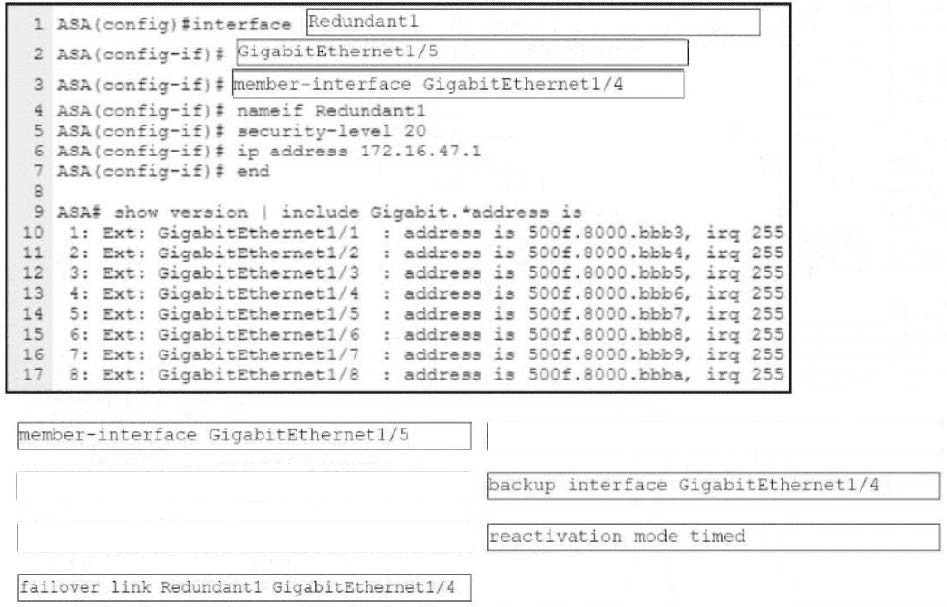
Refer to the exhibit.
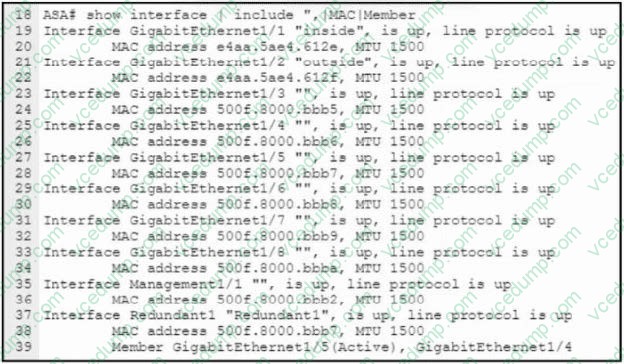
An engineer must configure a connection on a Cisco ASA Firewall with a Cisco Secure Firewall Services Module to ensure that the secondary interface takes over all the functions of the primary interface if the primary interface fails. Drag and drop the code snippets from the bottom onto the boxes in the CLI commands to configure the failover. Not all options are used.
Select and Place:
-
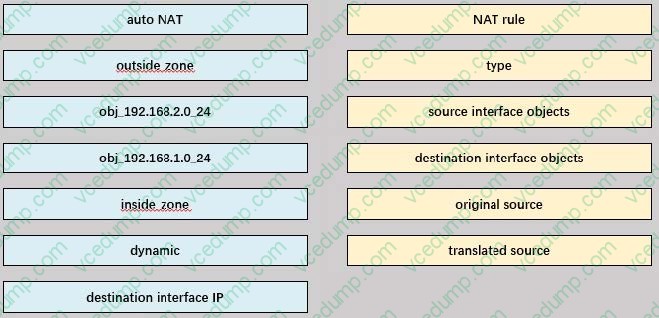
Question 2:
DRAG DROP
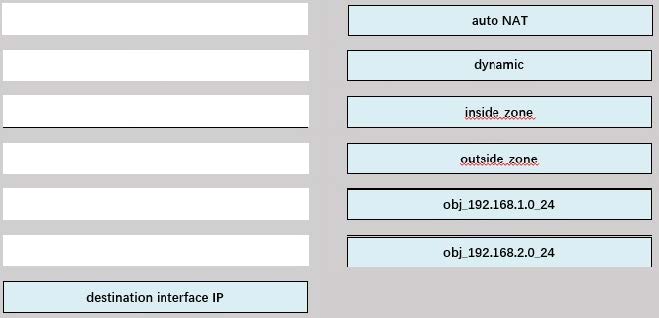
Refer to the exhibit.

An engineer configures a NAT rule allowing clients to use the internet only if clients are located on the directly connected internal network. Dynamic auto PAT must be configured. Drag and drop the NAT rules from the left onto the corresponding targets on the right. Not all options are used.
Select and Place:
-
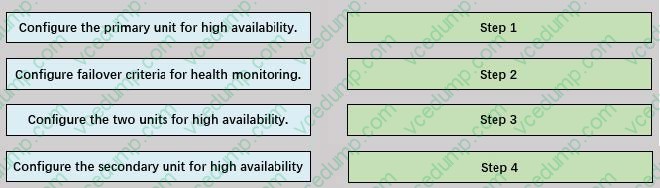
Question 3:
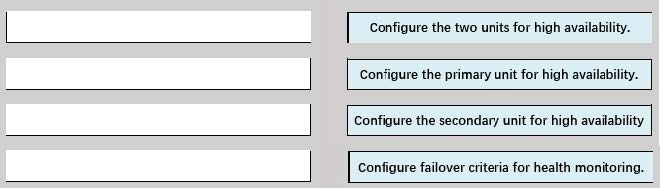
DRAG DROP
An engineer must configure high availability on two Cisco Secure Firewall Threat Defense appliances. Drag and drop the configuration steps from the left into the sequence on the right.
Select and Place:
-
Question 4:
An engineer is configuring a multidomain instance of Cisco Secure Firewall Management Center. The instance must be integrated with Cisco Secure Endpoint. What must the engineer configure to allow multiple domains to have hosts with the same IP-MAC address pairs?
A. second-level domain
B. leaf domain
C. global domain
D. subdomain -
Question 5:
An engineer is configuring two new Cisco Secure Firewall Threat Defense devices to replace the existing firewalls. Network traffic must be analyzed for intrusion events without impacting the traffic. What must the engineer implement next to accomplish the goal?
A. Passive mode
B. Inline Pair in Tap mode
C. ERSPAN Passive mode
D. Inline Pair mode -
Question 6:
An engineer is deploying Cisco Secure Endpoint for the first time and on endpoint with MAC address 50:54:15:04:0:AB. The engineer must make sure that during the testing phase no files are isolated and network connections must not be blocked. Which policy type must be configured to accomplish the task?
A. Triage
B. Quarantine
C. Protect
D. Audit -
Question 7:
An engineer must permit SSH on the inside interface of a Cisco Secure Firewall Threat Defense device. SSH is currently permitted only on the management interface. Which type of policy must the engineer configure?
A. platform policy
B. access control policy
C. NAT policy
D. intrusion policy -
Question 8:
Refer to the exhibit.
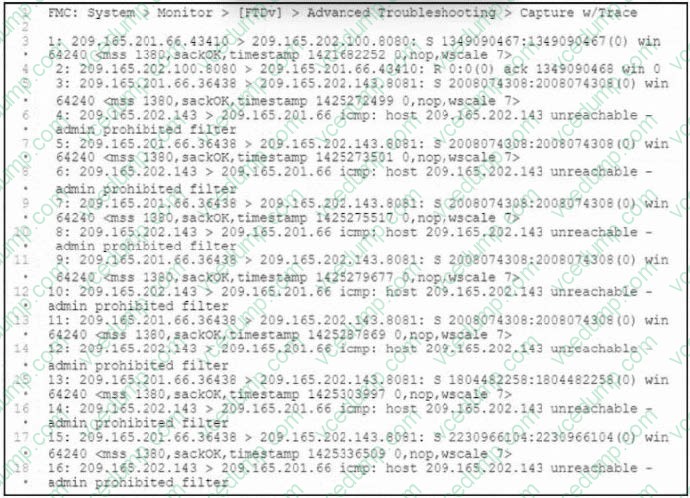
Users attempt to connect to numerous external resources on various TCP ports. If the users mistype the port, their connection closes immediately, and it takes more than one minute before the connection is torn down. An engineer manages to capture both types of connections as shown in the exhibit. What must the engineer configure to lower the timeout values for the second group of connections and resolve the user issues?
A. outbound access rule that allows the entire ICMP protocol suite
B. inbound access rule that allows ICMP Type 3 from outside
C. inbound access rule that allows TCP reset packets from outside
D. outbound access rule with the Block with reset action -
Question 9:
What is a feature of Cisco Secure Endpoint private cloud?
A. It disables direct connections to the public cloud.
B. It supports security intelligence filtering.
C. It support anonymized retrieval of threat intelligence.
D. It performs dynamic analysis. -
Question 10:
In a Cisco Secure Firewall Malware Defense deployment, which disposition is returned if the cloud cannot be reached?
A. unavailable
B. unknown
C. clean
D. disconnected
Related Exams:
-
300-710
Securing Networks with Cisco Firepower (SNCF) -
300-715
Implementing and Configuring Cisco Identity Services Engine (SISE) -
300-720
Securing Email with Cisco Email Security Appliance (SESA) -
300-725
Securing the Web with Cisco Web Security Appliance (SWSA) -
300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN) -
300-735
Automating and Programming Cisco Security Solutions (SAUTO) -
300-740
Designing and Implementing Secure Cloud Access for Users and Endpoints -
350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-710 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.