Exam Details
Exam Code
:250-440Exam Name
:Administration of Symantec PacketShaper 11.9.1Certification
:Symantec CertificationsVendor
:SymantecTotal Questions
:70 Q&AsLast Updated
:Aug 04, 2025
Symantec Symantec Certifications 250-440 Questions & Answers
-
Question 11:
Which option allows an administrator to differentiate Citrix-based applications and protect their performance?
A. Choose Priority 7 from the matching rule's Citrix-specific classification criteria to identify print traffic.
B. Assign the default partition and policy to all parts of the Citrix traffic tree, regardless of application urgency.
C. Enable discovery and let PacketShaper discover the Citrix-based applications, then create a traffic class for each one.
D. When Citrix applications generate a large amount of print traffic, merge multiple Citrix-based applications into one traffic class
-
Question 12:
A network administrator is interested in protecting VoIP traffic on the network.
How can the administrator best accomplish this while maintaining visibility into overall VoIP bandwidth
utilization'
A. An administrator is unable to monitor and protect All VoIP traffic at once using a PacketShaper
B. Create a class based on the IP addresses of the IP phones so that all traffic between them can be measured and controlled
C. Use PacketShaper's Flow Detail Record (FDR) feature to have the PacketShaper export VoIP flow data to ReportCenter
D. Create a folder with a guaranteed minimum sue partition and move all of the VoIP related classes into the folder
-
Question 13:
Refer to the exhibit.
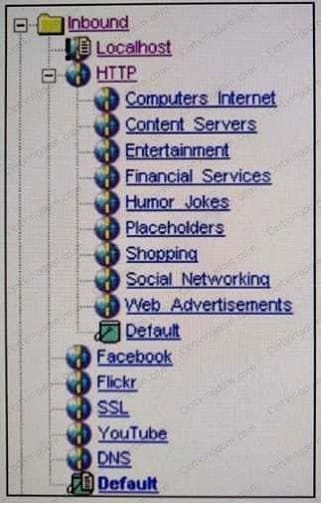
The Global Intelligence Network Of WebPulse service classifies .1 website as "Entertainment;
Mumor/tokes." The current configuration of PacketShaper has traffic discovery enabled within the Inbound/
HTTP class and has the class tree shown as in the exhibit with WebPulse enabled.
What two (2) classes will the traffic flow into when the client makes a request to the website in question?
(Select two)
A. Inbound/Local host
B. inbound/Entertainment
C. Inbound/HTTP/Default
D. Inbound/HTTP/Entertainment
E. Inbound/Humor_jotes
-
Question 14:
What is the purpose of a "Traffic Class"?
A. It enforces the policy by normalizing all traffic
B. It applies source routing features for load balancing
C. It identities the traffic type, which allows a policy to be applied
D. It forwards traffic to the Measurement Engine
-
Question 15:
Which class will automatically be at the highest point n the traffic tree?
A. The Default bucket
B. TCP Discovered_PoH_123
C. Any class with an IP address
D. HTTP which was auto-discovered
-
Question 16:
Which statement accurately describes the Transaction Delay Distribution graph?
A. Each time slot contains the number of transactions that are delayed within the specified number of minutes
B. The transaction delays ate categorized in one of fourteen transaction -time buckets, with the median delay indicated on the bottom of the graph
C. Fourteen colored lines track the total, network and server delays, so you can determine the source of any significant delays
D. The transaction delays are graphed on one of three colored lines, with the median delay indicated on the bottom of the graph
-
Question 17:
Which statement accurately describes rate policies and priority policies?
A. Priority policies are most appropriate tor interactive traffic that is burstable
B. Rate polices apply only to non-IP traffic
C. Traffic classes without a specific policy assigned, are allocated no bandwidth
D. Traffic with rate policies are applied before the priority policy
-
Question 18:
What do instances of bold text in the PacfcetShapet Wffie lice represent?
A. Default Policy
B. Policy that n actively being used
C. Policy that was changed during the current session D. Inheritable Policy
-
Question 19:
In some instances, there may be more flows than can be satisfied with the available bandwidth. Which graph identifies this situation in PacketShapet?
A. The Guaranteed Rate failures graph
B. The Partition Utilization graph
C. Automatic calculation, with no graph visible
D. The Network Efficiency graph
-
Question 20:
A PacketSHaper is installed between the VPN Gateway and Internet i outer at the main site of a company's
network A server at the main site is hosting business critical applications. A local ionbased traffic tree has
been created which classifies traffic coming from three remote sites by subnet.
All traffic between the remote sites and the central sue is encrypted.
Which two (2) useful pieces of data can the PacketShaper provide in this scenario? (Select two)
A. Bandwidth utilization of each individual application
B. Bandwidth utilization of the total encrypted VPN traffic
C. lop talkers and Top Listeners at the remote site
D. Bandwidth utilization of each individual remote site
E. Subnets or host lists of location-based classes
Related Exams:
250-428
Administration of Symantec Endpoint Protection 14250-438
Administration of Symantec Data Loss Prevention 15250-440
Administration of Symantec PacketShaper 11.9.1250-441
Administration of Symantec Advanced Threat Protection 3.0250-445
Administration of Symantec Email Security.cloud (v1)250-447
Administration of Symantec Client Management Suite 8.5250-513
Administration of Symantec Data Loss Prevention 12250-556
Administration of Symantec ProxySG 6.7250-561
Endpoint Security Complete - Administration R1250-580
Endpoint Security Complete - R2 Technical Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 250-440 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.