Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Apr 24, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 201:
What is a benefit of agent-based protection when compared to agentless protection?
A. It lowers maintenance costs
B. It provides a centralized platform
C. It collects and detects all traffic locally
D. It manages numerous devices simultaneously
-
Question 202:
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
A. integrity
B. confidentiality
C. availability
D. scope
-
Question 203:
Refer to the exhibit.
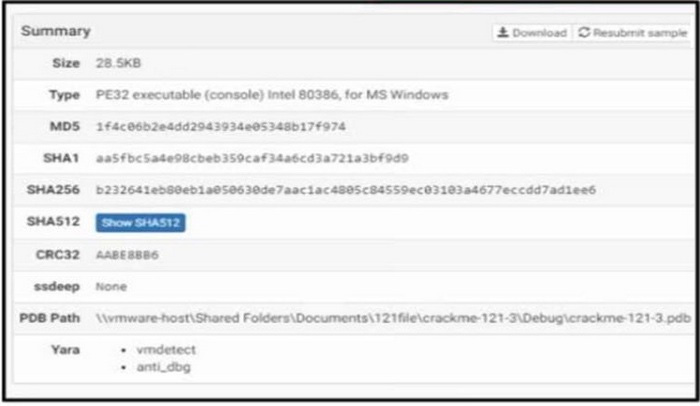
An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?
A. The file will appear legitimate by evading signature-based detection.
B. The file will not execute its behavior in a sandbox environment to avoid detection.
C. The file will insert itself into an application and execute when the application is run.
D. The file will monitor user activity and send the information to an outside source.
-
Question 204:
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
A. Hypertext Transfer Protocol
B. SSL Certificate
C. Tunneling
D. VPN
-
Question 205:
What is obtained using NetFlow?
A. session data
B. application logs
C. network downtime report
D. full packet capture
-
Question 206:
Refer to the exhibit.
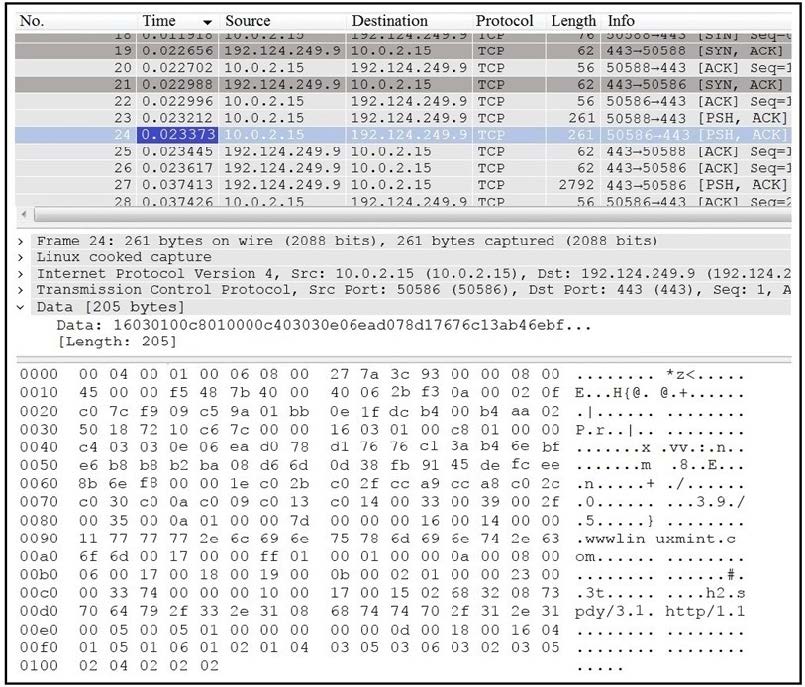
Which application protocol is in this PCAP file?
A. SSH
B. TCP
C. TLS
D. HTTP
-
Question 207:
What are two denial of service attacks? (Choose two.)
A. MITM
B. TCP connections
C. ping of death
D. UDP flooding
E. code red
-
Question 208:
Which two elements are used for profiling a network? (Choose two.)
A. session duration
B. total throughput
C. running processes
D. listening ports
E. OS fingerprint
-
Question 209:
What is the difference between statistical detection and rule-based detection models?
A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
-
Question 210:
How does TOR alter data content during transit?
A. It spoofs the destination and source information protecting both sides.
B. It encrypts content and destination information over multiple layers.
C. It redirects destination traffic through multiple sources avoiding traceability.
D. It traverses source traffic through multiple destinations before reaching the receiver
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.