Exam Details
Exam Code
:1D0-571Exam Name
:CIW v5 Security EssentialsCertification
:CIW CertificationsVendor
:CIWTotal Questions
:62 Q&AsLast Updated
:Jul 28, 2025
CIW CIW Certifications 1D0-571 Questions & Answers
-
Question 31:
Which of the following errors most commonly occurs when responding to a security breach?
A. Shutting down network access using the firewall, rather than the network router
B. Adhering to the company policy rather than determining actions based on the IT manager's input
C. Making snap judgments based on emotions, as opposed to company policy
D. Taking too much time to document the attack
-
Question 32:
The best way to thwart a dictionary attack is by enforcing a:
A. strong password policy.
B. restricted access policy.
C. firewall configuration policy.
D. proxy server policy.
-
Question 33:
A disgruntled employee has discovered that the company Web server is not protected against a particular buffer overflow vulnerability. The disgruntled employee has created an application to take advantage of this vulnerability and secretly obtain sensitive data from the Web server's hard disk. This application sends a set of packets to the Web server that causes it to present an unauthenticated terminal with root privileges. What is the name for this particular type of attack?
A. Man-in-the-middle attack
B. Trojan
C. Denial of service
D. Zero-day attack
-
Question 34:
Which of the following is a typical target of a trojan on a Linux system?
A. Kernel modules
B. Shared libraries
C. Boot sector files
D. System32 DLL files
-
Question 35:
You want to create a quick solution that allows you to obtain real-time login information for the administrative account on an LDAP server that you feel may become a target. Which of the following will accomplish this goal?
A. Reinstall the LDAP service on the server so that it is updated and more secure.
B. Install an application that creates checksums of the contents on the hard disk.
C. Create a login script for the administrative account that records logins to a separate server.
D. Create a dummy administrator account on the system so that a potential hacker is distracted from the
real login account.
-
Question 36:
What is the primary drawback of using symmetric-key encryption?
A. Key transport across a network
B. Speed of encryption
C. Denial-of-service attacks
D. Inability to support convergence traffic
-
Question 37:
A security breach has occurred involving the company e-commerce server. Customer credit card data has been released to unauthorized third parties. Which of the following lists the appropriate parties to inform?
A. Shareholders, law enforcement agencies and company employees
B. Affected customers, credit card companies and law enforcement agencies
C. The Internet Service Provider, ICANN and company shareholders
D. External securityconsultants, company board members and affected customers
-
Question 38:
You are using a PKI solution that is based on Secure Sockets Layer (SSL). Which of the following describes the function of the asymmetric-key-encryption algorithm used?
A. It encrypts the symmetric key.
B. It encrypts all of the data.
C. It encrypts the hash code used for data integrity.
D. It encrypts the X.509 key.
-
Question 39:
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
A. Application layer B. Network layer
C. Session layer
D. Transport layer
-
Question 40:
A new server has been placed on the network. You have been assigned to protect this server using a packet-filtering firewall. To comply with this request, you have enabled the following ruleset:
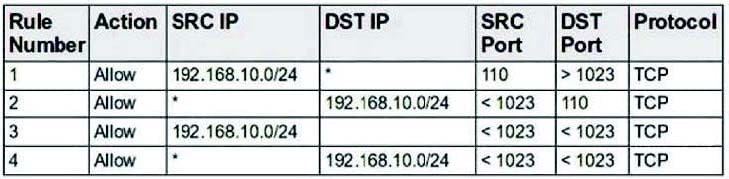
Which choice describes the next step to take now that this ruleset has been enabled?
A. From the internal network, use your Web browser to determine whether all internal users can access the Web server.
B. From the internal network, use your e-mail client to determine whether all internal users can access the e-mail server.
C. From the external network, use your Web browser to determine whether all external users can access the Web server.
D. From the external network, use your e-mail client to determine whether all external users can access the e-mail server.
Related Exams:
1D0-410
CIW Foundations1D0-430
CIW Application Developer1D0-435
CIW JavaScript Fundamentals1D0-437
CIW PERL FUNDAMENTALS1D0-442
CIW EnterprISE SPECIALIST1D0-450
CIW SERVER ADMINISTRATOR1D0-460
CIW INTERNetworking PROFESSIONAL1D0-470
CIW SECURITY PROFESSIONAL1D0-510
CIW v5 Founfations1D0-51B
CIW V5 Foundations SDF Module
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CIW exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1D0-571 exam preparations and CIW certification application, do not hesitate to visit our Vcedump.com to find your solutions here.