Exam Details
Exam Code
:1D0-571Exam Name
:CIW v5 Security EssentialsCertification
:CIW CertificationsVendor
:CIWTotal Questions
:62 Q&AsLast Updated
:Jul 28, 2025
CIW CIW Certifications 1D0-571 Questions & Answers
-
Question 11:
Your organization has made a particularly unpopular policy decision. Your supervisor fears that a series of attacks may occur as a result. You have been assigned to increase automated auditing on a server. When fulfilling this request, which of the following resources should you audit the most aggressively?
A. Authentication databases, including directory servers
B. Intrusion detection systems, especially those placed on sensitive networks
C. Log files on firewall systems
D. Firewall settings for desktop systems
-
Question 12:
You have just deployed an application that uses hash-based checksums to monitor changes in the configuration scripts of a database server that is accessible via the Internet. Which of the following is a primary concern for this solution?
A. The extra hard disk space required to store the database of checksums
B. The amount of memory remaining now that the checksum-based application is running
C. The possibility of a bufferoverflow attack leading to a security breach
D. The security of the checksum database on a read-only media format
-
Question 13:
Which of the following activities is the most effective at keeping the actions of nae end users from putting the company's physical and logicalWhich of the following activities is the most effective at keeping the actions of na?e end users from putting the company's physical and logical resources at risk?
A. Configuring network intrusion-detection software to monitor end user activity
B. Conducting a training session at the time of hire
C. Reconfiguring the network firewall
D. Assembling a team of security professionals to monitor the network
-
Question 14:
Which of the following applications can help determine whether a denial-of-service attack is occurring against a network host?
A. Thenetstat command and a packet sniffer
B. Theps command and a network scanner
C. The ping command and User Manager
D. Theiptables command and Windows desktop firewall
-
Question 15:
Which of the following is a primary auditing activity?
A. Encrypting data files
B. Changing login accounts
C. Checking log files
D. Configuring the firewall
-
Question 16:
You have determined that an attack is currently underway on your database server. An attacker is currently logged in, modifying data. You want to preserve logs, caching and other data on this affected server.
Which of the following actions will best allow you to stop the attack and still preserve data?
A. Pull the server network cable
B. Shut down the server
C. Back up the system logs
D. Force an instant password reset
-
Question 17:
Consider the following image of a packet capture: This packet capture has recorded two types of attacks. Which choice lists both attack types?
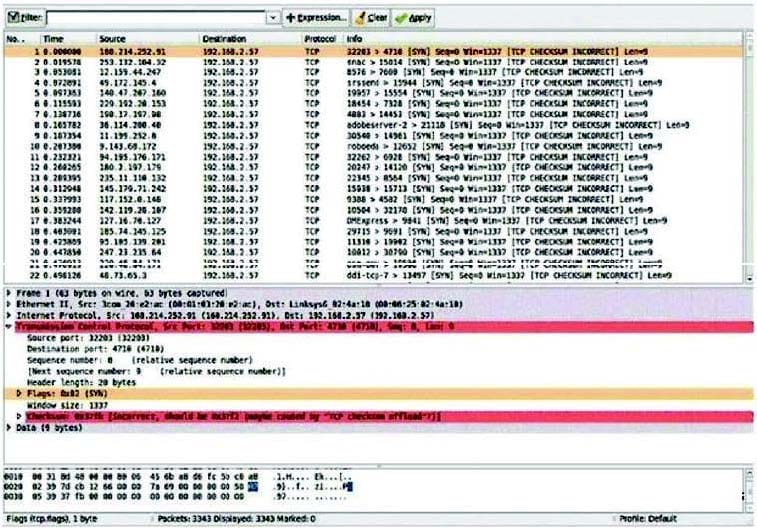
A. A dictionary attack and a worm-basedattackA.A dictionary attack and a worm-based attack
B. Asyn flood attack and a spoofing attackB.A syn flood attack and a spoofing attack
C. A worm attack and abotnet attack C.A worm attack and a botnet attack
D. A SQL injection attack and a virusattackD.A SQL injection attack and a virus attack
-
Question 18:
Which tool is best suited for identifying applications and code on a Web server that can lead to a SQL injection attack?
A. A vulnerability scanner
B. A packet sniffer
C. An intrusion-detection system
D. A network switch
-
Question 19:
Which of the following is a common problem, yet commonly overlooked, in regards to physical security in server rooms?
A. Firewalls that do not have a dedicated backup
B. False ceilings
C. Logic bombs
D. Biometric malfunctions
-
Question 20:
You are creating an information security policy for your company. Which of the following activities will help you focus on creating policies for the most important resources?
A. Auditing the firewall
B. Implementing non-repudiation
C. Logging users
D. Classifying systems
Related Exams:
1D0-410
CIW Foundations1D0-430
CIW Application Developer1D0-435
CIW JavaScript Fundamentals1D0-437
CIW PERL FUNDAMENTALS1D0-442
CIW EnterprISE SPECIALIST1D0-450
CIW SERVER ADMINISTRATOR1D0-460
CIW INTERNetworking PROFESSIONAL1D0-470
CIW SECURITY PROFESSIONAL1D0-510
CIW v5 Founfations1D0-51B
CIW V5 Foundations SDF Module
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CIW exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1D0-571 exam preparations and CIW certification application, do not hesitate to visit our Vcedump.com to find your solutions here.