Exam Details
Exam Code
:156-915.80Exam Name
:Check Point Certified Security Expert Update - R80.10Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:536 Q&AsLast Updated
:Jul 22, 2025
CheckPoint Checkpoint Certifications 156-915.80 Questions & Answers
-
Question 471:
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only
from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a
rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
What should John do when he cannot access the web server from a different personal computer?
A. John should lock and unlock his computer
B. Investigate this as a network connectivity issue
C. The access should be changed to authenticate the user instead of the PC
D. John should install the Identity Awareness Agent
-
Question 472:
Study the Rule base and Client Authentication Action properties screen After being authenticated by the Security Gateway, when a user starts an HTTP connection to a Web site, the user tries to FTP to another site using the command line. What happens to the user? The:
A. user is prompted for authentication by the Security Gateway again.
B. FTP data connection is dropped after the user is authenticated successfully.
C. user is prompted to authenticate from that FTP site only, and does not need to enter his username and password for Client Authentication.
D. FTP connection is dropped by Rule 2.
-
Question 473:
You find that Users are not prompted for authentication when they access their Web servers, even though you have created an HTTP rule via User Authentication. Choose the BEST reason why.
A. You checked the cache password on desktop option in Global Properties.
B. Another rule that accepts HTTP without authentication exists in the Rule Base.
C. You have forgotten to place the User Authentication Rule before the Stealth Rule.
D. Users must use the SecuRemote Client, to use the User Authentication Rule.
-
Question 474:
How are cached usernames and passwords cleared from the memory of a R80 Security Gateway?
A. By using the Clear User Cache button in SmartDashboard.
B. Usernames and passwords only clear from memory after they time out.
C. By retrieving LDAP user information using the command fw fetchldap.
D. By installing a Security Policy.
-
Question 475:
Your users are defined in a Windows 2008 R2 Active Directory server. You must add LDAP users to a Client Authentication rule. Which kind of user group do you need in the Client Authentication rule in R80?
A. External-user group
B. LDAP group
C. A group with a generic user
D. All Users
-
Question 476:
Assume you are a Security Administrator for ABCTech. You have allowed authenticated access to users from Mkting_net to Finance_net. But in the user's properties, connections are only permitted within Mkting_net. What is the BEST way to resolve this conflict?
A. Select Ignore Database in the Action Properties window.
B. Permit access to Finance_net.
C. Select Intersect with user database in the Action Properties window.
D. Select Intersect with user database or Ignore Database in the Action Properties window.
-
Question 477:
Which of the following are authentication methods that Security Gateway R80 uses to validate connection attempts? Select the response below that includes the MOST complete list of valid authentication methods.
A. Proxied, User, Dynamic, Session
B. Connection, User, Client
C. User, Client, Session
D. User, Proxied, Session
-
Question 478:
Security Gateway R80 supports User Authentication for which of the following services? Select the response below that contains the MOST correct list of supported services.
A. SMTP, FTP, TELNET
B. SMTP, FTP, HTTP, TELNET
C. FTP, HTTP, TELNET
D. FTP, TELNET
-
Question 479:
You are about to integrate RSA SecurID users into the Check Point infrastructure. What kind of users are to be defined via SmartDashboard?
A. A group with generic user
B. All users
C. LDAP Account Unit Group
D. Internal user Group
-
Question 480:
Review the rules.
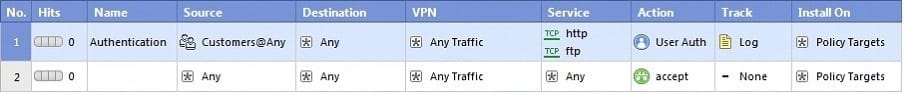
Assume domain UDP is enabled in the impled rules.
What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
A. can connect to the Internet successfully after being authenticated.
B. is prompted three times before connecting to the Internet successfully.
C. can go to the Internet after Telnetting to the client authentication daemon port 259.
D. can go to the Internet, without being prompted for authentication.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-915.80 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.