Exam Details
Exam Code
:156-915.80Exam Name
:Check Point Certified Security Expert Update - R80.10Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:536 Q&AsLast Updated
:Aug 07, 2025
CheckPoint Checkpoint Certifications 156-915.80 Questions & Answers
-
Question 361:
Your R80 primary Security Management Server is installed on GAiA;
You plan to schedule the Security Management Server to run fw logswitch automatically every 48 hours.
How do you create this schedule?
A. On a GAiA Security Management Server, this can only be accomplished by configuring the command fw logswitch via the cron utility.
B. Create a time object, and add 48 hours as the interval. Open the primary Security Management Server object's Logs and Masters window, enable Schedule log switch, and select the Time object.
C. Create a time object, and add 48 hours as the interval. Open the Security Gateway object's Logs and Masters window, enable Schedule log switch, and select the Time object.
D. Create a time object, and add 48 hours as the interval. Select that time object's Global Properties > Logs and Masters window, to schedule a logswitch.
-
Question 362:
Which of the following commands can provide the most complete restoration of a R80 configuration?
A. upgrade_import
B. cpinfo -recover
C. cpconfig
D. fwm dbimport -p
-
Question 363:
When restoring R80 using the command upgrade_import, which of the following items are NOT restored?
A. SIC Certificates
B. Licenses
C. Route tables
D. Global properties
-
Question 364:
Your organization's disaster recovery plan needs an update to the backup and restore section to reap the new distributed R80 installation benefits. Your plan must meet the following required and desired objectives:
Required Objective: The Security Policy repository must be backed up no less frequently than every 24 hours.
Desired Objective: The R80 components that enforce the Security Policies should be backed up at least once a week.
Desired Objective: Back up R80 logs at least once a week.
Your disaster recovery plan is as follows:
-
Use the cron utility to run the command upgrade_export each night on the Security Management Servers.
-
Configure the organization's routine back up software to back up the files created by the command upgrade_export.
-
Configure the GAiA back up utility to back up the Security Gateways every Saturday night.
-
Use the cron utility to run the command upgrade_export each Saturday night on the log servers.
-Configure an automatic, nightly logswitch.
-
Configure the organization's routine back up software to back up the switched logs every night. Upon evaluation, your plan:
A.
Meets the required objective and only one desired objective.
B.
Meets the required objective but does not meet either desired objective.
C.
Does not meet the required objective.
D.
Meets the required objective and both desired objectives.
-
Question 365:
The third-shift Administrator was updating Security Management Server access settings in Global Properties and testing. He managed to lock himself out of his account. How can you unlock this account?
A. Type fwm unlock_admin from the Security Management Server command line.
B. Type fwm unlock_admin -u from the Security Gateway command line.
C. Type fwm lock_admin -u
from the Security Management Server command line. D. Delete the file admin.lock in the Security Management Server directory $FWDIR/tmp/.
-
Question 366:
The third-shift Administrator was updating Security Management Server access settings in Global Properties. He managed to lock all administrators out of their accounts. How should you unlock these accounts?
A. Delete the file admin.lock in the Security Management Server directory $FWDIR/tmp/.
B. Reinstall the Security Management Server and restore using upgrade_import.
C. Type fwm lock_admin -ua from the Security Management Server command line.
D. Login to SmartDashboard as the special cpconfig_admin user account; right-click on each administrator object and select unlock.
-
Question 367:
You are the Security Administrator for ABC-Corp. A Check Point Firewall is installed and in use on GAiA;
You are concerned that the system might not be retaining your entries for the interfaces and routing configuration. You would like to verify your entries in the corresponding file(s) on GAiA; Where can you view them? Give the BEST answer.
A. /etc/sysconfig/netconf.C
B. /etc/conf/route.C
C. /etc/sysconfig/network-scripts/ifcfg-ethx
D. /etc/sysconfig/network
-
Question 368:
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?
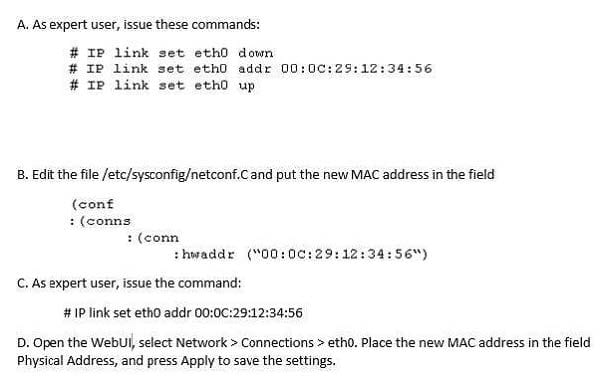
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 369:
Several Security Policies can be used for different installation targets. The Firewall protecting Human Resources' servers should have its own Policy Package. These rules must be installed on this machine and not on the Internet Firewall. How can this be accomplished?
A. A Rule Base is always installed on all possible targets. The rules to be installed on a Firewall are defined by the selection in the Rule Base row Install On.
B. When selecting the correct Firewall in each line of the Rule Base row Install On, only this Firewall is shown in the list of possible installation targets after selecting Policy > Install on Target.
C. In the menu of SmartDashboard, go to Policy > Policy Installation Targets and select the correct firewall via Specific Targets.
D. A Rule Base can always be installed on any Check Point Firewall object. It is necessary to select the appropriate target directly after selecting Policy > Install on Target.
-
Question 370:
You intend to upgrade a Check Point Gateway from R71 to R80. Prior to upgrading, you want to back up the Gateway should there be any problems with the upgrade. Which of the following allows for the Gateway configuration to be completely backed up into a manageable size in the least amount of time?
A. database revision
B. snapshot
C. upgrade_export
D. backup
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-915.80 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.