Exam Details
Exam Code
:156-315.77Exam Name
:Check Point Certified Security ExpertCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-315.77 Questions & Answers
-
Question 121:
Your online bookstore has customers connecting to a variety of Web servers to place or change orders and check order status. You ran penetration tests through the Security Gateway to determine if the Web servers were protected from a recent series of cross-site scripting attacks. The penetration testing indicated the Web servers were still vulnerable. You have checked every box in the Web Intelligence tab, and installed the Security Policy. What else might you do to reduce the vulnerability?
A. Configure the Security Gateway protecting the Web servers as a Web server.
B. Check the Products / Web Server box on the host node objects representing your Web servers.
C. Add Port (TCP 443) as an additional port on the Web Server tab for the host node.
D. The penetration software you are using is malfunctioning and is reporting a false- positive.
-
Question 122:
You find that Gateway fw2 can NOT be added to the cluster object.
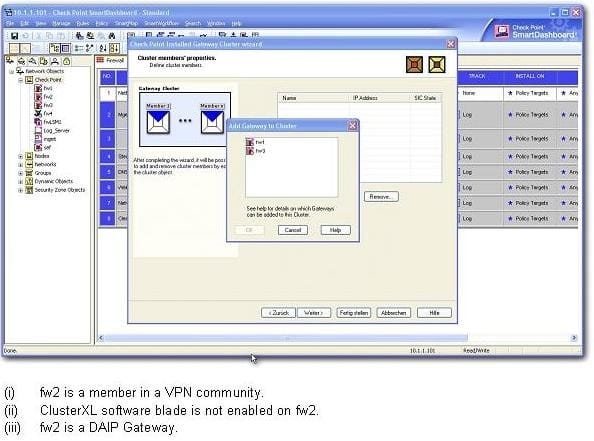
What are possible reasons for that?
A. 2 or 3
B. 1 or 2
C. 1 or 3
D. All
-
Question 123:
Which of the following statements about the Port Scanning feature of IPS is TRUE?
A. The default scan detection is when more than 500 open inactive ports are open for a period of 120 seconds.
B. The Port Scanning feature actively blocks the scanning, and sends an alert to SmartView Monitor.
C. Port Scanning does not block scanning; it detects port scans with one of three levels of detection sensitivity.
D. When a port scan is detected, only a log is issued, never an alert.
-
Question 124:
You run cphaprob -a if. When you review the output, you find the word DOWN. What does DOWN mean?
A. The cluster link is down.
B. The physical interface is administratively set to DOWN.
C. The physical interface is down.
D. CCP pakets couldn't be sent to or didn't arrive from neighbor member.
-
Question 125:
How do you upload the results of "CPSIZEME" to Check Point when using a PROXY server with authentication?
A. [expert@HostName]# ./cpsizeme.exe -a username:password@proxy_address:port
B. [expert@HostName]# ./cpsizeme -p username:password@proxy_address:port
C. [expert@HostName]# ./cpsizeme -a username:password@proxy_address:port
D. [expert@HostName]# ./cpsizeme.exe -p username:password@proxy_address:port
-
Question 126:
If your firewall is performing a lot of IPS inspection and the CPUs assigned to fw_worker_thread are at or near 100%, which of the following could you do to improve performance?
A. Add more RAM to the system.
B. Add more Disk Drives.
C. Assign more CPU cores to CoreXL
D. Assign more CPU cores to SecureXL.
-
Question 127:
The connection to the ClusterXL member `A' breaks. The ClusterXL member `A' status is now `down'. Afterwards the switch admin set a port to ClusterXL member `B' to `down'. What will happen?
A. ClusterXL member `B' also left the cluster.
B. ClusterXL member `B' stays active as last member.
C. Both ClusterXL members share load equally.
D. ClusterXL member `A' is asked to come back to cluster.
-
Question 128:
Refer to the network topology below.
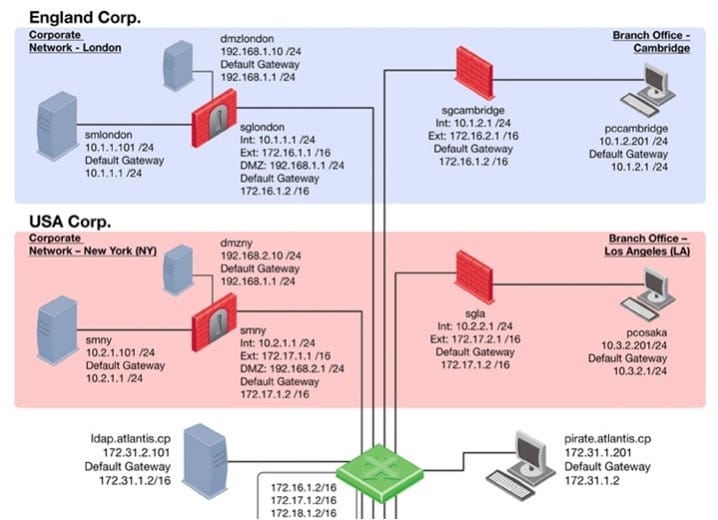
You have IPS Software Blades active on the Security Gateways sglondon, sgla, and sgny, but still experience attacks on the Web server in the New York DMZ. How is this possible?
A. All of these options are possible.
B. The attacker may have used a bunch of evasion techniques like using escape sequences instead of cleartext commands. It is also possible that there are entry points not shown in the network layout, like rogue access points.
C. Since other Gateways do not have IPS activated, attacks may originate from their networks without anyone noticing.
D. An IPS may combine different detection technologies, but is dependent on regular signature updates and well-tuned anomaly algorithms. Even if this is accomplished, no technology can offer 100% protection.
-
Question 129:
Can you implement a complete IPv6 deployment without IPv4 addresses?
A. No. IPv4 addresses are required for management.
B. No. SmartCenter cannot be accessed from everywhere on the Internet.
C. Yes, There is no requirement for managing IPv4 addresses.
D. Yes. Only one TCP stack (IPv6 or IPv4) can be used at the same time.
-
Question 130:
You plan to incorporate OPSEC servers, such asWeb senseand Trend Micro, to do content filtering. Which segment is the BEST location for these OPSEC servers, when you consider Security Server performance and data security?
A. On the Security Gateway
B. Internal network, where users are located
C. On the Internet
D. DMZ network, where application servers are located
E. Dedicated segment of the network
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.