Exam Details
Exam Code
:156-315.77Exam Name
:Check Point Certified Security ExpertCertification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:60 Q&AsLast Updated
:Dec 13, 2024
CheckPoint Checkpoint Certifications 156-315.77 Questions & Answers
-
Question 141:
When a packet is flowing through the security gateway, which one of the following is a valid inspection path?
A. Acceleration Path
B. Small Path
C. Firewall Path
D. Medium Path
-
Question 142:
The relay mail server configured under Email Notifications is used by the DLP Gateway to: (Choose the BEST answer.)
A. IfUser Checkis configured, there is no need to configure this relay server if there are no Ask User rules and there is no need to notify any Data Owners.
B. Send e-mail notifications to users and Data Owners.
C. Define My Organization / DLP Gateway and scan only e-mails that originate from this relay server.
D. Synchronize with other mail servers in the network.
-
Question 143:
Using the output below,why is the QoS rule not limiting the internal users to 2000 Bps of GNUtella traffic?
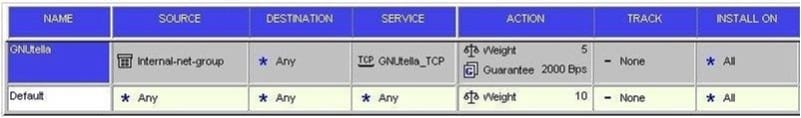
A. Rule Guarantee needs to be changed to Rule Limit
B. Rule Weight needs to be changed to 10
C. The Source and Destination columns need to be reversed
D. Encrypted traffic needs to be added to the Action field
-
Question 144:
You are trying to configure Directional VPN Rule Match in the Rule Base. But the Match column does not have the option to see the Directional Match. You see the following window.
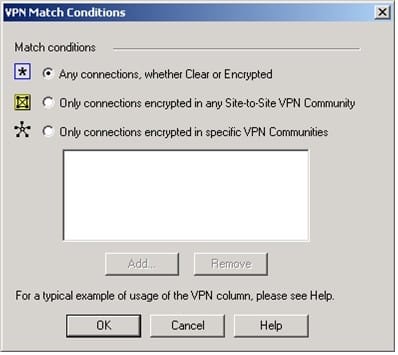
What must you enable to see the Directional Match?
A. VPN Directional Match on the Gateway object's VPN tab
B. Advanced Routing on each Security Gateway
C. VPN Directional Match on the VPN advanced window, in Global Properties
D. directional_match(true) in the objects_5_0.C file on Security Management Server
-
Question 145:
Which Remote Desktop protocols are supported natively in SSL VPN?
A. Microsoft RDP only
B. ATandT VNC and Microsoft RDP
C. Citrix ICA and Microsoft RDP
D. ATandT VNC, Citrix ICA and Microsoft RDP
-
Question 146:
You are responsible for the IPS configuration of your Check Point firewall. Inside the Denial of service section you need to set the protection parameters against the Teardrop attack tool with high severity. How would you characterize this attack tool? Give the BEST answer.
A. Hackers can send high volumes of non-TCP traffic in an effort to fill up a firewall State Table. This results in a Denial of Service by preventing the firewall from accepting new connections. Teardrop is a widely available attack tool that exploits this vulnerability.
B. A remote attacker may attack a system by sending a specially crafted RPC request to execute arbitrary code on a vulnerable system. Teardrop is a widely available attack tool that exploits this vulnerability.
C. Some implementations of TCP/IP are vulnerable to packets that are crafted in a particular way (a SYN packet in which the source address and port are the same as the destination, i.e., spoofed). Teardrop is a widely available attack tool that exploits this vulnerability
D. Some implementations of the TCP/IP IP fragmentation re-assembly code do not properly handle overlapping IP fragments. Sending two IP fragments, the latter entirely contained inside the former, causes the server to allocate too much memory and crash. Teardrop is a widely available attack tool that exploits this vulnerability.
-
Question 147:
Which of the following is a supported deployment for Connectra?
A. IPSO 4.9 build 88
B. VMWare ESX
C. Solaris 10
D. Windows server 2007
-
Question 148:
You need to verify the effectiveness of your IPS configuration for your Web server farm. You have a colleague run penetration tests to confirm that the Web servers are secure against traffic hijacks. Of the following, which would be the best configuration to protect from a traffic hijack attempt?
A. Enable the Web intelligence > SQL injection setting.
B. Activate the Cross-Site Scripting property.
C. Configure TCP defenses such as Small PMTU size.
D. Create resource objects for the Web farm servers and configure rules for the Web farm.
-
Question 149:
With is theSmart EventCorrelation Unit's function?
A. Assign severity levels to events.
B. Display received threats and tune the Events Policy
C. Invoke and define automatic reactions and add events to the database.
D. Analyze log entries, looking for Event Policy patterns.
-
Question 150:
Which technology would describe RDED for Qos?
A. A mechanism for reducing the number of retransmits and retransmit storms.
B. A mechanism for managing packet buffers.
C. A mechanism to accurately classify traffic and place it in the proper transmission queue.
D. A mechanism to derive complete state and context information for all network traffic.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215
Check Point Security Administration NGX156-215.1
Check Point Certified Security Administrator NGX156-215.70
Check Point Certified Security Administrator R70156-215.71
Check Point Certified Security Administrator R71156-215.75
Check Point Certified Security Administrator156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-315.77 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.